Using a cybersecurity risk assessment template is a smart way to get a grip on the digital threats facing your creative business. For UK-based creatives, it’s about turning those vague worries over cyberattacks into a clear, actionable plan that actually protects your client work and, just as importantly, your reputation.
Why Bother With a Security Plan?
As a creative, your headspace is filled with the next brief, the latest client feedback, and hitting that final delivery deadline. You’re not paid to decode technical jargon, and you certainly don't have time for it.
But what if a client’s confidential project files were swiped from your system? Or worse, what if ransomware locked up your entire portfolio—and all your invoices—the day before a major project is due?
These aren't scare tactics; they're genuine risks for freelancers, studios, and agencies all over the UK. For a creative business, the fallout from a cyber incident is uniquely damaging. It’s never just a technical glitch. It’s about losing irreplaceable assets and the trust you’ve worked so hard to build.
The Real-World Risks for Creatives
Forgetting about cybersecurity is a bit like leaving the studio door unlocked overnight. You might get away with it for a while, but eventually, someone’s going to wander in.
Here’s a look at the most frequent threats targeting creative professionals and what they could mean for your business.
Common Cyber Threats for UK Creatives
A quick look at the most frequent risks targeting creative professionals and their potential impact.
| Threat Type | What It Looks Like | Impact on Your Business |
|---|---|---|
| Phishing & Spear Phishing | An email pretending to be from a client, supplier, or service like Dropbox, tricking you into giving up login details. | Loss of access to accounts, stolen data, fraudulent invoices being paid. |
| Ransomware | A pop-up demanding money to unlock your files. Your entire portfolio, client work, and financial records are suddenly inaccessible. | Complete business standstill, missed deadlines, potential permanent loss of all your work. |
| Intellectual Property Theft | A quiet breach where a competitor or malicious actor steals your unreleased designs, client concepts, or proprietary assets. | Loss of competitive advantage, leaked client work, serious reputational harm. |
| Data Breach (Client Info) | Your client list, contact details, and project information are stolen and potentially leaked or sold online. | Severe damage to client trust, potential GDPR fines, and loss of future business. |
These threats are not just hypotheticals. The UK's own Cyber Security Breaches Survey shows that 39% of UK businesses reported a cyber breach or attack in the last year. Phishing is the most common offender, making a proactive plan essential, no matter how small your studio is.
A cybersecurity risk assessment is your first, most practical step towards building a resilient creative business. It helps you move from a state of vague anxiety to one of empowered control, ensuring the technology you rely on supports your creativity instead of threatening it.
Your Simple Risk Assessment Framework

Let's be honest, the moment someone mentions a risk assessment, most people picture mind-numbing spreadsheets and technical jargon. A good cybersecurity risk assessment template should not feel like doing your taxes. For creative professionals, it needs to be visual, straightforward, and focused on action, not just endless analysis.
Forget the complexity for a moment. This is just a simple, three-part process:
- Identify what you need to protect. These are your digital crown jewels, your assets.
- Figure out what could go wrong. These are the threats and any weak spots you might have.
- Decide how serious each risk is. This is where you prioritise your time and energy.
Our goal here is not to build complicated financial models. We are aiming for clarity. For most UK-based freelancers and small creative studios, a qualitative approach is more than enough. It simply means categorising risks as ‘low’, ‘medium’, or ‘high’ based on how likely they are to happen and the potential damage they could cause. It’s a refreshingly quick and effective way to see what needs your immediate attention.
Start with a Simple Asset Inventory
Before you can protect anything, you have to know what you have. This is not about listing every USB cable and mouse. It is about identifying the digital heart of your creative business. Just grab a notepad or open a fresh document and start noting things down. Do not overthink it.
What are the essentials? The things that, if suddenly lost, stolen, or compromised, would cause a massive headache or even bring your business to a grinding halt.
Here are a few common ones to get you started:
- Client Files & Project Data: Think of all your active project folders, final design files, proofs, and any materials your clients have sent you.
- Intellectual Property (IP): This is your own hard work. Your studio's branding, custom templates, unreleased concepts, and your entire portfolio archive.
- Business & Financial Records: Crucial items like invoices, contracts, your client contact lists, and any data held in your accounting software.
- Key Software & Subscriptions: Your access to tools like Adobe Creative Cloud, project management platforms such as Asana or Trello, and of course, your email accounts.
Once you have this list, you are already on your way. You have just created a basic map of your digital world, which is the foundational step for any meaningful cybersecurity risk assessment.
A qualitative assessment gives you the power to prioritise without getting bogged down in numbers. It’s about quickly understanding what’s ‘on fire’ versus what’s a ‘slow burn’, so you can direct your energy where it matters most.
It’s worth noting that official UK frameworks, like ISO/IEC 27005, often come in different forms: qualitative (ranking risks as we are), quantitative (assigning financial values), or a hybrid of both. For a creative business whose main worries are things like phishing scams or a ransomware attack, the simplicity of a qualitative model provides the most practical and immediate path forward. As you get more comfortable, you can always explore these other models to see which one fits your creative business best.
Where Are Your Crown Jewels? Mapping Your Critical Creative Assets
Before you can use a risk assessment template, you first need a clear picture of what you are actually protecting. For any creative business, your most valuable assets are not just the laptops and phones you use every day. They are the intangible, irreplaceable things that are your work.
Your intellectual property, active client projects, your painstakingly curated portfolio, and your hard-won reputation are the crown jewels. A solid security plan starts by knowing exactly what they are and where they live.
Moving Beyond the Obvious
It is easy to list physical hardware, but the real value is in the data. The problem is, that data is usually scattered across many different platforms and devices, which can make it feel impossible to manage. A good first step is to simply map out where your critical information is stored.
Think about all the places your work actually exists:
- On your machine: This includes your computer’s hard drive, any external drives plugged into it, and any on-site servers in your studio.
- In the cloud: Services like Dropbox, Google Drive, or WeTransfer where you store and share those massive files.
- In your workflow tools: Platforms like Asana, Trello, or Notion that hold project briefs, client feedback, and crucial timelines.
- In your inbox: Your email accounts are often a goldmine of contracts, invoices, and sensitive client communications.
Once you have this map, you can start to see the full scope of what needs protecting. This is not about creating a complex inventory; it is about building awareness of your digital footprint.
Assigning a “Can’t-Live-Without-It” Level
Let's be honest: not all assets are created equal. Losing access to a draft blog post for a week is an inconvenience. Losing your entire client archive is a catastrophe that could shut your business down. This is where assigning a 'criticality' level is useful. It’s a simple exercise that helps you prioritise your efforts later.
For each asset you have identified, give it a straightforward rating:
- High Criticality: The business would grind to a halt without it. This includes your primary portfolio, client billing information, or master design files.
- Medium Criticality: Its loss would cause significant disruption. This might cover your project management data or internal communication tools.
- Low Criticality: An annoyance, but work can continue. Think of things like archived social media content or non-essential software.
By rating your assets, you transform a long, intimidating list into a manageable, prioritised action plan. You can see at a glance what needs the strongest locks and the most attention.
Let's look at a couple of real-world UK examples. A freelance copywriter might classify her Google Drive, which holds all her client work, as ‘High Criticality’. A small London design studio would almost certainly do the same for their shared server holding all their Adobe Creative Cloud projects. Both would likely rate their accounting software access as equally critical. This simple exercise provides the clarity you need to start making smart security decisions.
Uncovering Your Unique Risks and Weak Spots
You have mapped out your critical assets. Now it is time to think like a thief. This part of the cybersecurity risk assessment template is where we identify the threats and weaknesses that could put those assets in jeopardy.
This is not about inventing doomsday scenarios. It is a practical, honest look at your day-to-day creative workflows to spot the small gaps an attacker could easily exploit. For creatives, these weak spots often hide in plain sight.
Brainstorming Your Potential Threats
Threats are not just anonymous hackers in dark rooms. A threat can be as mundane as an accidental file deletion, a sudden hardware failure, or an employee making a genuine mistake. Your job here is to create a 'threat library', a simple list of what could go wrong, tailored specifically to your creative business.
To get started, think about these common situations for UK creatives:
- Working on the go: Are you connecting to public Wi-Fi in a café or on the train? Those networks are notoriously insecure, making it easy for someone to snoop on your activity.
- Collaborating with clients: How are you sharing files? Sending sensitive project files through unencrypted email or using a client’s preferred but insecure file-sharing service is a significant risk.
- Managing your team: Does everyone in your studio truly understand the dangers of phishing? A single click on a malicious link can compromise your entire network.
- Maintaining your tools: When was the last time you updated the plugins on your portfolio website? Or the software on your main design machine? Outdated software is one of the most common entry points for attackers.
Think of this as a pre-mortem for your projects. Instead of asking "what went wrong?" after a disaster, you are proactively asking "what could go wrong?". This simple shift in mindset is the secret to spotting risks before they become incidents.
From Vague Worries to Specific Vulnerabilities
Once you have brainstormed some general threats, it's time to pinpoint the specific vulnerabilities in your setup. A vulnerability is a weakness that a threat can exploit. The threat is the ‘what,’ and the vulnerability is the ‘how.’
Let's break it down with a clear example.
Scenario: A Freelance Photographer
- Critical Asset: A hard drive containing a client's entire wedding photo collection.
- Threat: Accidental damage or simple hardware failure. What happens if the drive is dropped or just fails?
- Vulnerability: There is no backup. The photographer keeps only one copy of the photos, making them completely dependent on a single piece of hardware.
By identifying this specific vulnerability, the solution becomes obvious. The risk is not just "losing photos"; it's "losing photos because there is no backup strategy."
Here are some prompts to help you analyse your own workflows with the same critical eye:
- Passwords: Do you reuse the same password across multiple services, like your email, cloud storage, and client portals? Be honest.
- File Transfers: How do you send large design files to clients? Is the method you use actually secure and encrypted?
- Software Updates: Are your operating system, creative software, and website plugins all set to update automatically, or are you leaving it to chance?
Answering these questions honestly will reveal the specific weak spots in your defences. This detailed analysis is the core of an effective risk assessment and gives you a clear, actionable list of problems to solve.
Analysing and Prioritising Your Biggest Threats

Having a long list of potential problems can feel paralysing. The secret is not to try and fix everything at once, but to know which fire to put out first. This is where proper risk analysis turns vague worries into a concrete, manageable priority list.
The next step in completing your cybersecurity risk assessment template is to score each risk you have identified. This process makes it immediately obvious where your attention is most needed, ensuring you do not waste time and resources on minor issues while a major one looms.
From List to Action with Impact and Likelihood
To prioritise effectively, you need to evaluate each threat against two simple criteria: its likelihood and its potential impact.
- Likelihood: How probable is it that this threat will happen? Use a simple scale: Low, Medium, or High.
- Impact: If it does happen, how much damage would it cause to your business? Again, stick to Low, Medium, or High.
For instance, a junior designer accidentally deleting a draft social media graphic is a High Likelihood, Low Impact event. It’s annoying, but easily fixed. On the other hand, a sophisticated ransomware attack is hopefully a Low Likelihood event, but its consequences would be devastating, making it High Impact.
By combining these two scores, you get a clear risk rating. This simple matrix of likelihood multiplied by impact is the engine that powers your entire action plan. It moves you from "what if?" to "what now?".
This scoring is particularly useful for creatives. It helps you justify spending on things like better backup solutions or security training. A 'High Impact' risk is a clear signal that investment is not just a good idea, but essential for survival.
Creating Your Traffic Light System
Once you've scored your risks, you can visualise your entire threat landscape using a simple traffic light system. This is a brilliant way to quickly communicate priorities to your team or even just to yourself.
Assign a colour to each combination:
- Red (High Priority): These are your most severe risks. A combination of High Likelihood and High Impact, or even Medium Likelihood and High Impact, falls into this category. These require immediate attention.
- Amber (Medium Priority): These are significant risks that need a plan but are not necessarily on fire. This might be a High Likelihood, Medium Impact risk.
- Green (Low Priority): These are minor issues. Think Low Likelihood and Low Impact. You should be aware of them, but they can be addressed after the Red and Amber risks are under control.
This visual system makes your completed cybersecurity risk assessment template incredibly easy to understand at a glance. For remote-first studios, where team members are often scattered, understanding these priorities is especially vital. In fact, you can explore more about the top cybersecurity risks of remote work to see how this applies.
Let’s apply this to a real-world scenario for a small UK-based branding agency.
Risk Prioritisation Example
| Risk | Likelihood | Impact | Priority |
|---|---|---|---|
| Main server failure with no backup | Low | High | Red |
| Phishing email leading to stolen passwords | High | High | Red |
| Project manager leaving with client data | Low | Medium | Amber |
| Temporary website outage (1-2 hours) | Medium | Low | Green |
As you can see, this simple table instantly clarifies where the agency must focus its efforts. The Red risks are non-negotiable and need an immediate action plan, which we will cover next.
Building Your Cybersecurity Action Plan
This is where the hard work starts to pay off. You have put in the time to map out your assets, identify the threats around them, and even colour-coded them with a traffic light system. Now, your cybersecurity risk assessment template is about to transform from a document into a clear, powerful action plan.
It is time to decide what to do about those Red and Amber risks.
For every significant risk you've flagged, you have four main options. This is not about getting bogged down in complex technical fixes for everything. It is about making deliberate, practical choices that fit your creative business.
Choosing Your Strategy
Your response to each risk will generally fall into one of four buckets. Let's break down what these actually mean for a busy creative studio.
-
Mitigate: This is your go-to response for most things. You take direct action to make the risk less likely or less damaging. For instance, if you have a 'Red' risk of a ransomware attack, mitigation means setting up solid, off-site backups and running basic security awareness training for your team. Simple. Effective.
-
Avoid: Sometimes, the easiest fix is to just stop doing the risky thing. If you have identified that your team is sending huge, sensitive client files using an insecure public transfer service, you can avoid that risk entirely by switching to a secure, encrypted client portal. Problem solved.
-
Transfer: This is about shifting the financial fallout of a risk onto someone else. For a UK creative business, the classic example is getting a solid cyber insurance policy. It will not stop an attack from happening, but it is a massive help in recovering from the financial damage if the worst happens.
-
Accept: For some low-level risks, the cost and hassle of fixing them is not worth it. If you have a 'Green' risk of a temporary website blip that might last five minutes, you might just accept it. You know it is unlikely to happen and the impact would be minimal.
You do not have to eliminate every single risk. The goal is to make informed decisions that reduce your overall vulnerability to a level you're comfortable with. This is the essence of proactive cybersecurity.
Your downloadable cybersecurity risk assessment template has a column waiting for this exact step. For each risk you've prioritised, you will note down which of these four strategies you are choosing and the specific actions you're going to take.
A Living Document for Ongoing Protection
A crucial point: your risk assessment is not a "one-and-done" task you can file away and forget. To build real resilience, it needs to be a living document that grows and changes right alongside your business.
This simple cycle shows you how to keep your plan relevant.
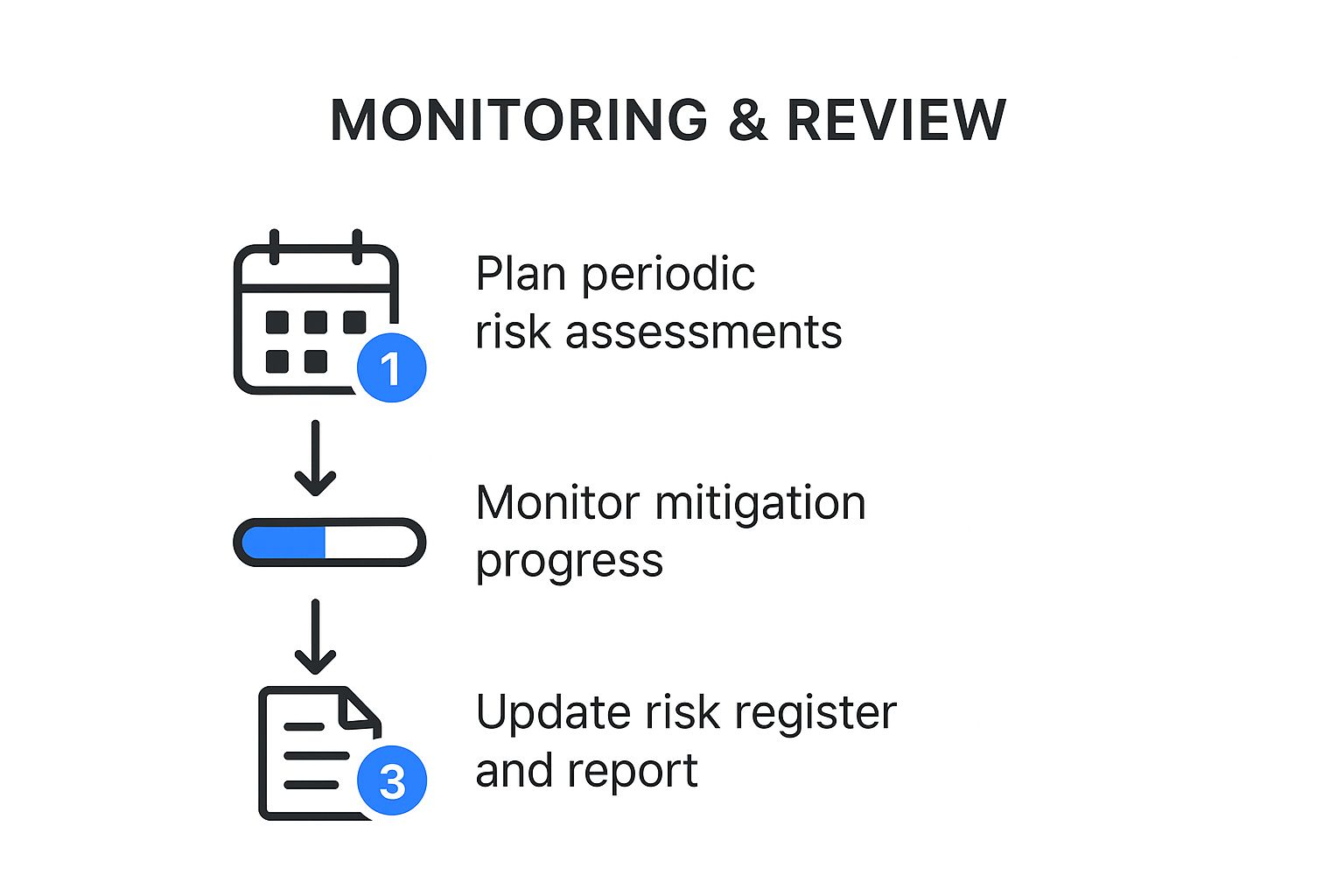
Think of it as a continuous loop: you plan, you monitor, you update. This ensures your security efforts never get stale.
As a rule of thumb, you should review your risk assessment at least once a year. You will also want to review it whenever something big changes in your business, like bringing on a new team member, onboarding a major client, or adopting a new software platform. This ongoing cycle is the core of what we call proactive cybersecurity and how to maximize your business resilience.
By regularly revisiting your plan, you make sure your defences always keep pace with your creative ambitions.
Frequently Asked Questions
When you're trying to get your creative work done, the last thing you want to worry about is a mountain of cybersecurity questions. Let's cut through the noise and tackle some of the most common queries we hear from UK-based creatives who are getting to grips with a risk assessment for the first time.
How Often Should I Review My Risk Assessment?
For most creative freelancers and small studios here in the UK, a full, detailed review once a year is a solid baseline. It's enough to keep your security thinking fresh and relevant.
But do not just file it away and forget about it. Your risk assessment should be a living document, not a one-off task.
You will want to give it a quick review whenever your business hits a milestone. Good triggers for a review include:
- Taking on a major new client, especially if they have specific rules about how you handle their data.
- Rolling out a new core software tool across the studio, like a project management system or a different cloud storage provider.
- Hiring your first employee or bringing in regular collaborators who need access to your systems.
Think of it this way: when your business evolves, your security needs to evolve with it. A quick check-in at these key moments ensures your defences are keeping pace.
Do I Really Need Cyber Insurance as a Creative in the UK?
While it is not legally mandatory for most creative businesses, we strongly recommend looking into a cyber insurance policy. It’s a crucial part of the 'Transfer' strategy in your risk plan, and it's a financial safety net you will be glad to have if things go wrong.
An insurance policy can cover the costs that come with a data breach, things like hiring specialist IT support to fix the mess, paying legal fees, or covering the financial hit from business interruption. It effectively transfers some of that financial risk you have identified, letting you focus on getting back on your feet.
If I Only Do One Thing, What's the Most Important Security Measure?
Simple. If you do nothing else today, go and enable multi-factor authentication (MFA) on every critical account you can. This means your email, your cloud storage, your banking, anything that holds sensitive information or client work.
MFA adds a second layer of security, usually a one-time code sent to your phone. This simple step makes it incredibly difficult for an attacker to get in, even if they somehow manage to steal your password.
It is the single biggest security improvement you can make for the least amount of effort.
Ready to turn these insights into a rock-solid plan? At InfraZen Ltd, we specialise in helping UK creative businesses manage their technology and security without the jargon. We handle the complexity behind the scenes, so you have the freedom to focus on your craft. Protect your work and build a more resilient studio by visiting us at https://infrazen.tech.

