In our hyper-connected world, you can think of a cyber security consulting service as an expert guide, helping your organisation shield its most critical data and operations from online threats. This isn't just another IT expense- it's a fundamental investment in your business's resilience and, frankly, its survival.
Why UK Businesses Need a Security Strategy

Staring down the barrel of potential cyber attacks can feel overwhelming. It’s all too easy to dismiss the threat as something that only happens to bigger companies. But as one UK creative agency learned the hard way, that kind of thinking can lead to disaster.
Imagine a busy studio, right in the middle of a massive project for a major client. Deadlines are looming, and the team is completely absorbed in delivering outstanding creative work. Their security setup is what you’d call basic: standard antivirus software and a firewall they assume is doing its job. Anything more advanced feels like a luxury, not a necessity.
Then, one Monday morning, everything changes. The team walks in to find their systems totally locked, files encrypted, and a ransom note demanding a hefty payment. It wasn't some sophisticated, targeted operation. It was a simple, automated attack that exploited an unpatched vulnerability on their server.
The Tangible Impacts of a Breach
The immediate fallout is pure chaos. The agency can't touch its client files, project timelines, or even its accounting software. All productive work grinds to a halt. That operational downtime is the first, most obvious cost of a security failure.
But the damage goes much, much deeper. Let’s peel back the layers of harm:
- Loss of Client Data: The breach exposes sensitive information belonging to their clients, from strategic plans to proprietary campaign concepts.
- Reputational Harm: Word gets out, and their reputation takes a nosedive. Clients lose trust, wondering if the agency can really be trusted with their valuable intellectual property.
- Financial Penalties: On top of the ransom demand, the agency now faces potential fines under GDPR for not properly protecting personal data.
- Business Interruption: Getting systems back online from backups- if they even work- is a matter of days, not hours. Every moment of downtime means lost revenue and soaring recovery costs.
The true cost of a cyber incident is rarely just the initial financial loss. It's the erosion of client trust, the long-term damage to your brand's reputation, and the immense operational strain of recovery- impacts that can linger for years.
Proactive Defence Is Not a Luxury
This story drives home a critical point: proactive security isn't just an IT line item; it's a core part of your business strategy. Waiting for an attack to happen is a gamble most businesses simply can't afford to take. Getting to grips with the basics is a great first step, as this essential guide on network security for small businesses explains.
For creative agencies and others handling valuable assets, the stakes are even higher. Your value is in your ideas, designs, and client data. A breach doesn't just halt operations- it strikes at the very heart of what you do.
This is where a cyber security consulting service provides the strategic foresight that was missing from our story. Instead of just reacting to threats, a consultant helps you build a resilient security posture designed for your specific risks. They don't just sell you software; they help you build a culture of security, turning a potential weakness into a real competitive strength. It makes proactive defence a must-have for survival and growth.
What a Cyber Security Consulting Service Actually Does
Let's clear something up. A cyber security consulting service isn't just another IT support contract. It’s the difference between having a guard at the gate and having a master strategist defending your entire fortress.
Think of your business as that fortress. Inside, you're protecting your most valuable assets- client data, original designs, financial records. You've probably got some basic defences in place, like antivirus software (guards) and firewalls (high walls). But are they in the right places? Are there secret tunnels you've completely missed?
A cyber security consultant is the architect of your defence. They don't just sell you more bricks. They study your unique layout, map the surrounding threats, and find the hidden weak points, like that unguarded side entrance everyone forgot about. It's a strategic role that goes miles beyond simply fixing things when they break.
From Assessment to Action Plan
The first thing a consultant does is a proper risk assessment. This isn't a quick virus scan; it’s a deep dive into your people, processes, and technology to see where the real vulnerabilities are hiding.
They’ll look at how your team handles sensitive information, where your most critical data lives, and how your tech is actually configured. For example, they might find that your remote work policies are leaving gaping holes in your security or that your website's content management system is dangerously out of date. For agencies using WordPress, this could involve something like a detailed WordPress security checklist to systematically lock down the site.
Once they have a clear map of the risks, they move on to strategic planning. This is where they draw up the blueprint- a practical road map that outlines prioritised actions to shrink your exposure to threats, all while aligning with your actual business goals.
And this field is growing for a reason. In the UK, which accounts for 15.8% of the European market, cyber security consulting is a huge area of expertise. The European market was valued at around $2.95 billion USD in 2025 and is projected to skyrocket to over $10.97 billion by 2033. This isn't just a trend; it's a fundamental business need.
Building a Resilient Defence
With a strategy sorted, the focus shifts to building your defences. This isn't just about buying new software. It's about creating a security-conscious culture and making smart tech choices.
To help you get a clearer picture, here’s a breakdown of what these services typically involve, from the initial look-around to the ongoing management.
Core Components of a Cyber Security Consulting Service
| Service Component | Objective | Typical Activities |
|---|---|---|
| Risk Assessment | Identify and understand vulnerabilities. | Reviewing policies, scanning systems, and interviewing staff. |
| Strategic Planning | Develop a prioritised action plan. | Creating a security road map, and defining goals and metrics. |
| Policy Development | Create clear security rules for the team. | Writing incident response plans and data handling procedures. |
| Technology Guidance | Select and implement the right tools. | Evaluating software, overseeing configuration, and managing vendors. |
| Ongoing Management | Maintain and adapt defences over time. | Continuous monitoring, regular reviews, and threat intelligence. |
These components work together to build a defence that’s not just strong, but also smart and adaptable.
The consultant’s job is to translate that strategic plan into real-world protection. This happens in two key ways:
Policy development is about creating simple, clear rules for your team to follow. Think of things like:
- Acceptable Use Policies: What can and can't employees do on company devices and networks?
- Incident Response Plans: A step-by-step guide for what to do when a breach happens, so you can minimise panic and damage.
- Data Handling Procedures: Clear protocols for managing sensitive client files securely from start to finish.
Next comes technology implementation guidance. The consultant offers unbiased advice on the right tools for your specific situation. They help you choose, set up, and manage security solutions that fit your needs and budget, making sure you’re not wasting money on flashy software you don’t need or leaving yourself exposed.
The real difference between standard IT support and a cyber security consulting service comes down to foresight. IT support reacts to problems- fixing a broken laptop or restoring a lost file. A consultant works proactively to stop those problems from happening in the first place, building a security posture that can stand up to future threats.
This strategic, forward-thinking approach provides lasting value. It shifts your agency from a state of constant reaction to a position of control and confidence, letting you focus on your creative work without constantly worrying about what might go wrong.
How Consultants Protect Your Business Assets

Bringing in a cyber security consultant is about shifting your mindset from reactive to proactive. Instead of just waiting for something to go wrong, you’re actively building a structured defence around the things that make your business unique and valuable. It’s about so much more than just installing software.
For a creative agency, these assets aren't just servers and laptops. They are the proprietary designs you've crafted, the confidential client campaign data you hold, and the unique creative processes that give you an edge. A consultant’s number one job is to shield these specific, high-value assets from harm.
Shielding Your Intellectual Property
Think about your most important online files for a moment. What comes to mind? The concepts for a new brand identity, the source files for a major advertising campaign, or the client strategy documents you’ve spent months developing. These are your crown jewels.
A security consultant essentially helps you put them in a digital vault.
They start by identifying where this critical data lives and how it moves through your agency. From there, they implement layers of protection. This might mean setting up strict access controls so only authorised team members can touch sensitive files, or deploying encryption to make stolen data completely unreadable. The goal is simple: make your intellectual property a much, much harder target for attackers.
Turning Security into a Competitive Advantage
In today’s climate, demonstrating robust security isn’t just about defence; it's a powerful selling point. When you’re pitching for a contract with a large, security-conscious partner, you can bet they will want to know exactly how you protect their information.
Being able to show them a professional security policy, evidence of regular risk assessments, or proof of your partnership with a cyber security consulting service can be a key differentiator. It tells potential clients that you take their data as seriously as they do, building the trust needed to win those high-stakes contracts. This turns a security investment into a direct business enabler.
A strong security posture is no longer a back-office function. It's a client-facing asset that demonstrates professionalism and trustworthiness, helping you attract and retain the high-value clients you want to work with.
Navigating Complex Regulations
For UK businesses, regulations like the General Data Protection Regulation (GDPR) are not optional. Getting it wrong can result in severe financial penalties and serious reputational damage. The trouble is, the rules can be complex and almost impossible to interpret without specialist knowledge.
A consultant acts as your guide through this maze. They translate dense legal requirements into practical, actionable steps for your agency. For example, they can help you create the right data processing agreements, implement procedures for handling data subject access requests, and ensure your storage practices are fully compliant. This lifts a significant burden, letting you focus on your creative work with confidence.
Securing Your Modern Workforce
The way we work has changed for good. With team members often working remotely or from different locations, the traditional office network perimeter has dissolved. This creates a whole new set of security challenges- how do you protect company data on an employee's home Wi-Fi network?
A consultant helps you build a security model that’s actually fit for a distributed team. This includes:
- Securing Remote Connections: Implementing secure VPNs (Virtual Private Networks) to encrypt all traffic between remote workers and your company systems.
- Device Management: Establishing policies to ensure that all devices accessing company data- whether they're company-owned or personal- meet minimum security standards.
- Cloud Security: Configuring your cloud apps like Microsoft 365 or Google Workspace with the correct security settings to prevent unauthorised access.
A key part of this involves implementing robust systems like various types of Intrusion Detection Systems (IDS). This proactive monitoring helps to spot suspicious activity before it can escalate. And if your strategy needs continuous oversight, exploring different models such as managed cyber security services can provide the ongoing support necessary to keep your defences strong.
Embedding a Culture of Security
Ultimately, technology alone can’t protect you. Your team is your first and most important line of defence. A great consultant helps foster a culture of security awareness, turning your employees from potential risks into active defenders.
This isn’t about boring, generic presentations. It’s achieved through targeted training that uses real-world examples relevant to your industry, teaching your staff how to spot phishing emails, use strong passwords, and handle sensitive data responsibly. By making security a shared responsibility, you create a far more resilient organisation from the inside out.
Finding the Right Consulting Specialisation
Picking a cyber security consulting service isn't a one-size-fits-all deal. The field is massive, with experts focusing on very specific areas of protection. Choosing the right specialist is critical- it's the difference between getting targeted advice for your actual challenges and a generic solution that completely misses the point.
Think of it like this: if you need a new brand identity, you don't just hire any graphic designer; you find a branding specialist. The same logic applies here. Understanding the different specialisations helps you have much better conversations with potential partners and, ultimately, find the expert who genuinely gets what your agency needs.
Governance, Risk, and Compliance (GRC)
Think of GRC consultants as the legal advisors of the cyber security world. Their main job is to make sure your online operations line up with industry regulations and legal standards. For any creative agency in the UK, this is a huge deal, especially with rules like GDPR in play.
A GRC specialist helps you nail down the answers to crucial questions:
- Are we storing client data in a fully compliant way?
- Do our internal policies actually meet the legal standards we're held to?
- From a regulatory standpoint, where are our biggest risks?
Their role is to build the frameworks, policies, and procedures that keep you on the right side of the law. They don’t just flag problems; they help you create a structured programme to manage risk properly, protecting you from eye-watering fines and reputational damage.
Incident Response Planning
While a GRC consultant helps you avoid legal hot water, an Incident Response (IR) planner gets you ready for the moment a crisis actually hits. These specialists are your emergency coordinators. They create a detailed, step-by-step playbook for what to do when- not if- a security breach happens.
An Incident Response plan is your agency's fire drill for a cyber attack. Without one, you're left scrambling in the dark, wasting precious time and making costly mistakes. A planned response ensures calm, coordinated action that drastically minimises damage.
An IR planner will work with you to define roles, set up communication channels, and outline the technical steps for containing a threat. This proactive prep work is what separates a minor hiccup from a business-ending catastrophe.
The image below shows just how dramatic an impact proactive consulting, including IR planning, can have on real-world security metrics.
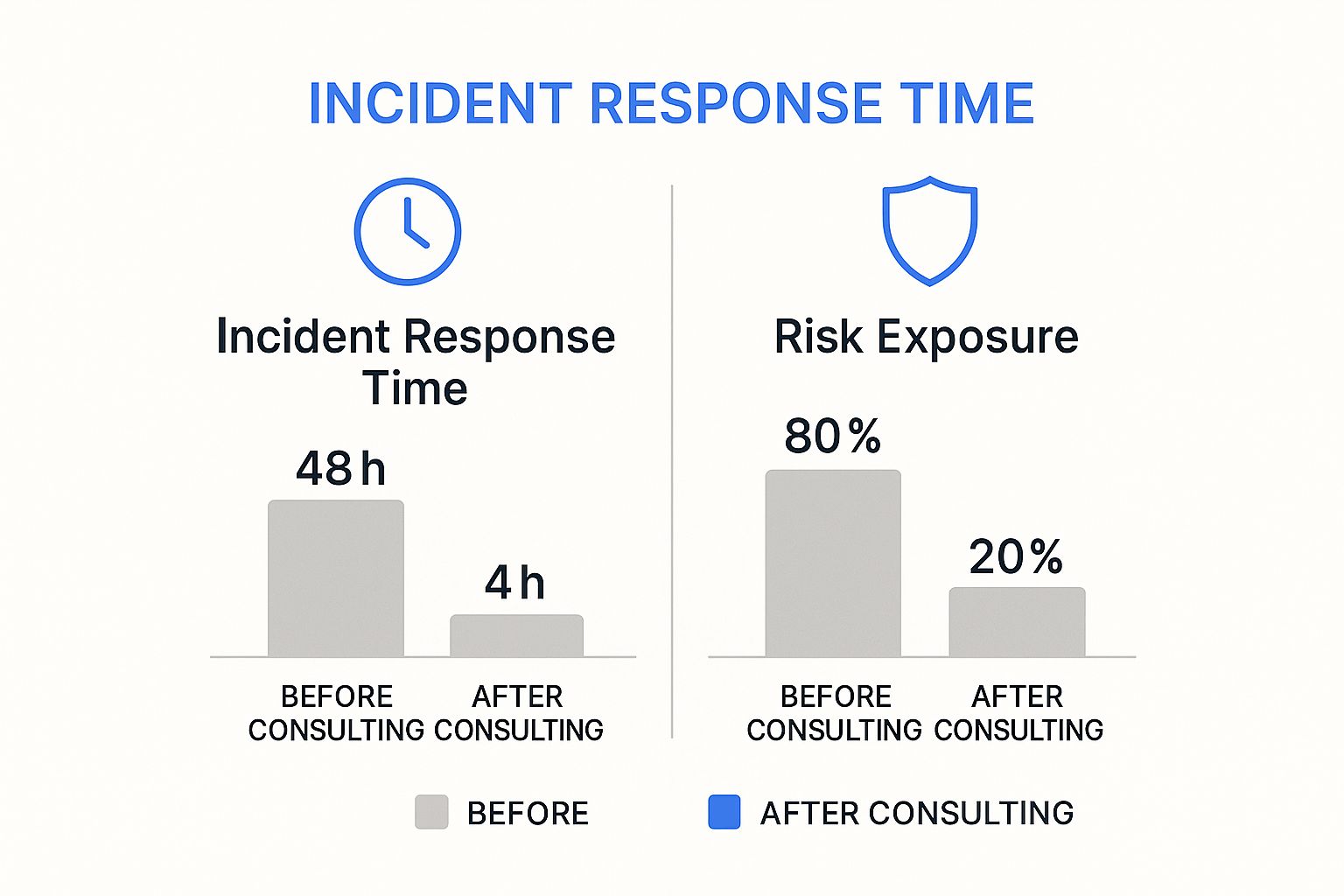
The numbers speak for themselves. A strategic partnership doesn't just offer peace of mind; it significantly cuts down your recovery time and shrinks your overall vulnerability.
Penetration Testing (Ethical Hacking)
Penetration testers, often called "ethical hackers," are the experts you hire to try and break into your own systems. It sounds a bit odd, but it's one of the most powerful ways to uncover weaknesses before a real attacker does. It’s like hiring a building inspector who actively tries to pick your locks and find unsecured windows.
A penetration tester simulates real-world attacks against your:
- Websites and Web Applications: Hunting for flaws that could expose sensitive client data.
- Internal Networks: Checking if an intruder who gets past your first line of defence can wander around freely.
- Cloud Infrastructure: Testing the security of your cloud-based storage and software.
After the tests, they deliver a detailed report that outlines every vulnerability they found and- most importantly- how to fix it. This gives you a practical, prioritised to-do list for beefing up your technical defences. The entire point is to patch the holes before they can be exploited.
Cloud Security Specialisation
With so many creative agencies now living in cloud services like Adobe Creative Cloud, Google Workspace, and Microsoft 365, cloud security has become an essential specialisation. These consultants focus purely on securing your data and workflows within these complex environments.
A cloud security expert helps you configure these powerful platforms correctly- something a surprising number of businesses get wrong. They make sure sharing permissions are locked down tight, multi-factor authentication is properly enforced, and your data is protected according to the best practices for each specific platform. Given that one simple misconfiguration in the cloud can lead to a massive data breach, this specialisation is non-negotiable for a modern creative agency.
Comparing Cyber Security Consulting Specializations
Choosing the right expert depends entirely on your agency's immediate priorities and biggest risks. To help clarify which type of consultant you might need, this table breaks down the primary focus of each specialisation.
| Specialization | Primary Focus | Best For Businesses Needing… |
|---|---|---|
| GRC | Aligning security with legal and regulatory standards (e.g., GDPR). | To build legally sound data policies and avoid regulatory fines. |
| Incident Response | Creating a step-by-step plan for handling a security breach. | A clear, actionable playbook for when a cyber attack occurs. |
| Penetration Testing | Actively finding and reporting technical vulnerabilities in systems. | A real-world test of their digital defences to find and fix holes. |
| Cloud Security | Securing data and configurations within cloud platforms (e.g., M365). | To lock down their cloud apps and prevent data leaks. |
Ultimately, the best choice links directly to your most pressing challenge. Are you worried about legal compliance, preparing for a potential attack, testing your tech, or securing your cloud tools? Answering that question is the first step to finding the right expert partner.
Tapping into the UK's Cyber Security Ecosystem

When your creative agency is based in the UK, choosing a local cyber security consulting service is more than a simple matter of convenience. It’s a powerful strategic move that plugs you directly into one of the world's most dynamic and advanced security hubs.
This isn’t just about having someone in your time zone. It’s about tapping into a world-class talent pool, backed by serious government support and private investment. This unique environment means new defensive tech and strategies are constantly emerging right on your doorstep. For your agency, that translates to direct access to consultants who are genuinely at the forefront of threat intelligence and defensive tactics.
Crucially, this proximity ensures the advice you get isn't some generic, off-the-shelf best practice. It’s informed by the very latest regional threat intelligence and fine-tuned for the specific challenges that UK businesses, like yours, actually face. A UK-based consultant simply gets the local regulatory environment and the specific attack vectors targeting British companies.
A Thriving Hub of Expertise
The UK's domestic cyber security sector isn’t just mature- it's booming. As of 2025, the industry generated an incredible £13.2 billion in revenue, marking a 12% surge from the previous year. This isn't just a handful of big players, either. The growth is driven by 2,165 active firms and a highly skilled workforce of over 67,300 professionals.
What does that mean for you? It means there's a deep well of specialised talent right here. Whether you need an expert in GDPR compliance, a specialist in securing cloud workflows for creative projects, or an ethical hacker to stress-test your defences, that expertise is available locally. You can explore more data on the industry's explosive growth and see how it directly benefits UK businesses.
Choosing a UK-based cyber security consulting service isn’t about patriotism. It’s a calculated move to align your business with a global centre of excellence, ensuring you get high-calibre, relevant, and forward-thinking security guidance.
Your Strategic Advantage
Partnering with a local expert gives you a clear edge. They don’t just bring technical skills to the table; they bring a nuanced understanding of the UK business climate. This translates into security strategies that are more practical, more effective, and far easier for your team to implement and maintain.
Ultimately, this direct line to a world-class ecosystem builds immense confidence. You can rest assured that the service you receive is backed by a robust national infrastructure dedicated to cyber defence. It turns your security from a nagging worry into a solid, dependable asset for your business.
How to Choose the Right Security Partner
Picking the right cyber security consultant is a huge decision, one that has a direct line to your agency’s safety and reputation. This isn’t about being wowed by the most complex-sounding tech; it’s about finding a genuine partner who gets the unique pressures and workflows of the creative world. The best ones translate dense security jargon into clear business outcomes.
Making a confident choice means you need a proper evaluation process. You have to look past the marketing fluff and get into their real-world experience, their credentials, and just as importantly, how they communicate. A consultant who can't explain risk in plain English is a bad fit for a creative agency, no matter how brilliant they are technically.
Vetting Potential Consultants
Before you even think about signing a contract, you need to do your homework on a consultant's track record. Look for hard proof that they've worked with businesses like yours before. If they have experience with creative agencies, they’ll already be familiar with your workflows, the kind of data you handle, and where your biggest weak spots are likely to be.
Next, check their credentials. Official UK certifications are a good baseline for quality and professionalism. A couple of key ones to look out for are:
- Cyber Essentials and Cyber Essentials Plus: These are government-backed schemes that show a company has its fundamental security controls sorted.
- CREST Accreditation: This is a sign of top-tier, trusted expertise in specialist areas like penetration testing and handling security incidents.
These certifications aren't just badges; they signal that a provider meets recognised industry standards. This vetting is also in line with the UK government's push to build a stronger domestic cyber industry through initiatives like the 2025 'Cyber Growth Action Plan', which has invested £16 million to boost innovation. Learn more about how this government plan secures critical services.
Critical Questions to Ask
Once you’ve got a shortlist, it's time to ask some direct questions to see how they really operate. Their answers will tell you everything about their approach and whether it gels with your agency’s culture. You're looking for a partner who is transparent, methodical, and collaborative. To get started, it helps to understand the landscape of UK cyber security service providers and what really sets them apart.
Use this checklist when you talk to them:
Checklist for Evaluating a Security Partner
- Assessment Methodology: How will you actually assess our current security? What frameworks or standards do you follow?
- Reporting Process: What do your reports look like? Can we see a sanitised example? Crucially, how do you explain your findings to people who aren't tech experts?
- Incident Response Management: What’s your process if we have a security breach? What level of support can we expect from you when things go wrong?
- Team Communication: Who will be our main point of contact? How often will we meet to review progress and talk about new threats?
- Understanding Our Business: What experience do you have with creative agencies and protecting valuable intellectual property?
Their responses will give you a gut feeling for their expertise, their communication style, and whether they can become a trusted extension of your team. This structured approach helps you sidestep common hiring mistakes and land a partner who will genuinely help protect your business.
Frequently Asked Questions About Cyber Security Consulting
Diving into the world of cyber security consulting for the first time? It's completely normal to have a list of questions. This is a big decision for your creative agency, and you need clear, honest answers before you commit. Let's tackle some of the most common queries we hear from UK businesses, so you can move forward with confidence.
What Is the First Step in Working with a Consultant?
The first conversation almost always starts with discovery and assessment. A good consultant won't walk in and start pushing new software or rattling off recommendations. Their first job is to get to know you– your unique workflows, your most valuable data, and your current security setup.
This involves talking to your team, taking a look under the bonnet of your existing systems, and figuring out where the real risks are hiding. Think of it like a doctor carrying out a full diagnostic before even thinking about a prescription. This foundational step ensures every piece of advice that follows is genuinely tailored to your agency, not just generic, off-the-shelf solutions.
How Much Does a Cyber Security Consulting Service Cost?
The cost can vary quite a bit, depending on what you need. A one-off project, like a penetration test to check for vulnerabilities or a GDPR compliance audit, will typically have a fixed price. On the other hand, ongoing advisory services- often called a virtual CISO (vCIO) service- are usually based on a monthly retainer.
For smaller UK agencies, you might see project-based work starting from a few thousand pounds. Retained services could be anywhere from several hundred to a few thousand pounds per month. The key is to get a detailed proposal that spells out exactly what's included so you know what you’re paying for.
Remember to weigh the cost of consulting against the potential cost of a security breach. A single incident can easily cost a small business tens of thousands of pounds in downtime, recovery, and reputational damage. Suddenly, that proactive investment looks a lot more manageable.
How Long Does It Take to See Results?
You'll see some results almost immediately. After the initial assessment, a consultant can often identify and help you fix "quick wins"- critical gaps that can be patched up in just a few hours or days. This gives your risk profile an instant, and very welcome, drop.
Building a truly strong security culture, however, is a longer game. Implementing new policies, training your team, and rolling out new technologies all take time. A great consultant will give you a clear road map with milestones, so you can track your progress and see real, tangible improvements month by month. To get a sense of what a solid foundation looks like, it’s worth reviewing the 5 critical cybersecurity measures for small businesses.
Is Our Agency Too Small for a Consultant?
Absolutely not. In fact, it's often the smaller agencies that get the most out of a consultant because they don't have the budget or need for a dedicated, in-house security expert. Attackers love targeting smaller businesses precisely because they assume their defences are weaker.
A consulting service gives you access to enterprise-level expertise without the hefty salary of a full-time hire. It levels the playing field, allowing you to build professional-grade security that protects your work and helps you win business from bigger, more security-conscious clients. It's an investment in resilience and growth, no matter the size of your team.
Ready to stop worrying about IT and focus on what you do best? InfraZen Ltd provides specialist cyber security and IT management for creative agencies, ensuring your systems are secure, efficient, and interruption-free. Get the peace of mind you deserve at https://infrazen.tech.

