Understanding Risk Assessment Fundamentals That Actually Work

A cybersecurity risk assessment is the foundation of any strong security strategy, especially for UK businesses. It's more than just checking boxes; it's about understanding your organization's specific vulnerabilities and building a security program that truly protects your operations. This means going beyond standard checklists and focusing on practical steps that deliver real results. Understanding the UK's specific regulatory environment, including GDPR, is crucial.
Aligning Your Assessment with UK Regulations
The UK's data protection laws and industry regulations significantly influence your risk assessment approach. For example, GDPR compliance requires you to pinpoint data processing activities, evaluate their inherent risks, and put appropriate safeguards in place. Your cybersecurity risk assessment must address not only technical vulnerabilities but also ensure that data protection principles are integrated into your operations. Furthermore, sectors like finance and healthcare have additional requirements to consider.
Choosing Effective Methodologies
Cybersecurity risk assessments vary in effectiveness. Some offer genuine insights, while others generate impressive reports that miss critical vulnerabilities. Choosing the right approach is essential. A qualitative assessment might suit smaller businesses looking for a broad overview. A quantitative assessment, on the other hand, provides more detailed risk measurement for larger organizations.
Addressing the UK Threat Landscape
The UK's cybersecurity environment poses unique challenges. It's characterized by persistent threats. The Cyber Security Breaches Survey 2025 reveals that just over four in ten businesses (43%) reported a cybersecurity breach or attack in the last year. This number jumps significantly for medium and large businesses: 70% and 74%, respectively. This highlights how crucial it is to understand the specific threats your business faces, moving beyond generic threat lists and focusing on the attack patterns actually targeting UK businesses, like ransomware and social engineering.
Avoiding Common Pitfalls
Many organizations invest in expensive solutions for unlikely threats while neglecting basic vulnerabilities in their daily operations. A solid cybersecurity risk assessment helps avoid these pitfalls by prioritizing practical security improvements aligned with your business needs and budget. This involves honest discussions about your organization's actual risk tolerance and building a security program that adapts as your business evolves.
Identifying Real Threats In Today's UK Business Environment

Instead of relying on generic lists of potential cyber threats, let's examine the specific dangers facing UK businesses today. This requires a close look at the real attack patterns security teams are encountering across various industries. For instance, manufacturing firms are increasingly targeted by ransomware, while financial services remain susceptible to social engineering attacks.
Sector-Specific Threats in the UK
Understanding how these threats change and identifying which ones pose real risks to your business model is crucial for a robust cybersecurity risk assessment. This involves analyzing recent security incidents and collaborating with incident response teams. This practical approach allows businesses to gain valuable insights into how real-world attacks happen and their potential consequences.
Furthermore, understanding the specific threats impacting your industry allows you to tailor your security measures effectively. This targeted approach ensures your resources are used efficiently and address the most relevant risks.
The scale of cyber threats in the UK is substantial. Over 7.7 million attacks have targeted UK businesses, highlighting the need for vigilance. This emphasizes the critical importance of thorough cybersecurity risk assessments and robust security strategies. More detailed statistics can be found here.
Practical Approaches to Threat Intelligence
Many companies invest heavily in complex security solutions for unlikely threats, often neglecting everyday vulnerabilities in their operations. A more practical approach involves staying informed about emerging risks through accessible resources.
This includes using government resources like the National Cyber Security Centre (NCSC), participating in industry partnerships, and engaging in intelligence sharing initiatives. This proactive, action-oriented approach allows businesses to address genuine threats and weaknesses rather than hypothetical scenarios. You might also find this helpful: How to master threat modelling for UK accountancy businesses.
Prioritising Actionable Security Measures
Effective threat identification informs a focused cybersecurity risk assessment, resulting in practical security implementations that genuinely protect your business. This method helps prioritize security investments based on real risk reduction, avoiding reactions to vendor marketing.
By understanding the specific threats your business and sector face, you can build a stronger, more resilient security posture. This proactive approach minimizes vulnerabilities and strengthens your overall defenses.
Asset Discovery And Vulnerability Assessment That Makes Sense
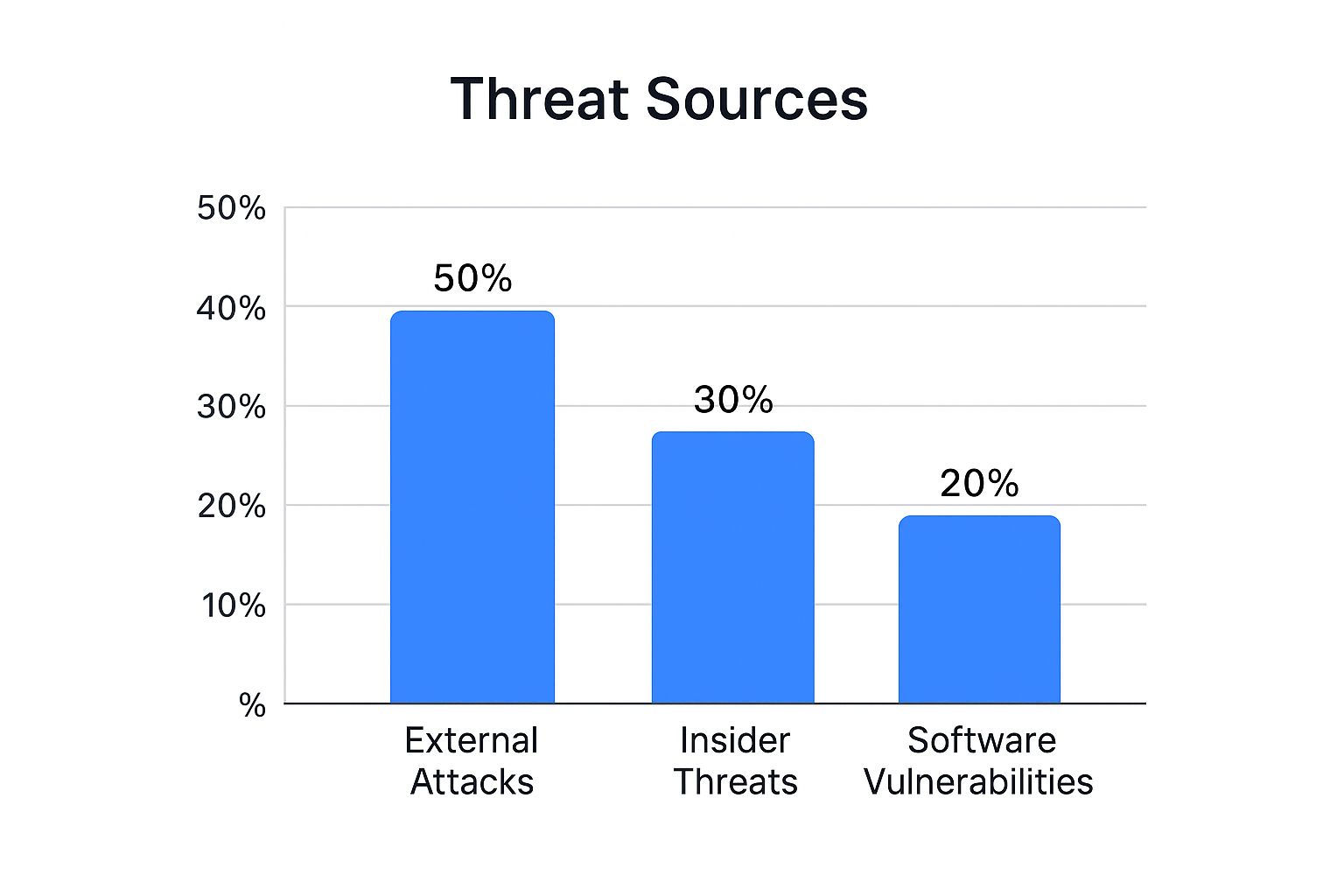
The chart above highlights the sources of common cyber threats. External attacks account for 50%, insider threats represent 30%, and software vulnerabilities make up the remaining 20%. This data emphasizes the need to address both external and internal risks. Keeping software updated is also crucial for minimizing vulnerabilities.
However, understanding threat origins is only the first step. A truly effective cybersecurity risk assessment requires a deep understanding of what needs protecting. This goes beyond simple asset inventories. It demands a comprehensive view of your entire IT environment.
Identifying Critical Assets
Modern IT environments in the UK are complex, spanning cloud services, remote work setups, and even legacy systems running critical processes. This complexity means asset discovery needs a more nuanced approach than a basic checklist.
Successful organizations prioritize assets based on their business impact. For instance, a server containing sensitive client data is more critical than a spare workstation. This practical approach focuses security efforts where they matter most.
Effective Asset Monitoring
Once critical assets are identified, ongoing monitoring is key. This doesn't always require expensive new tools. Many UK businesses effectively track assets through a combination of automated scanning and regular reviews.
This combined approach allows for adaptability. Businesses can stay informed about environmental changes and adjust their security strategies accordingly. For more information on a specific type of threat, check out our guide on what SaaS ransomware is and how to defend against it.
Addressing Shadow IT and Blind Spots
Shadow IT, the use of unauthorized software and services, presents a common blind spot in asset discovery. Addressing this requires a balanced approach. Security is paramount, but maintaining productivity is equally important.
Instead of strict restrictions, fostering open communication and providing approved alternatives is more effective. This cultivates security awareness without hindering productivity. Therefore, a comprehensive cybersecurity risk assessment considers both technical systems and the human element. By prioritizing the business impact of assets and promoting a culture of security awareness, organizations can build a robust security posture.
To help visualize and prioritize security efforts, the following table provides a framework for classifying assets based on risk.
Asset Classification Framework for Risk Assessment
Comparison of different asset types, their typical vulnerabilities, and risk levels to help organisations prioritize their security efforts
| Asset Type | Common Vulnerabilities | Risk Level | Assessment Frequency |
|---|---|---|---|
| Client Data Server | Unauthorized access, data breaches, ransomware | High | Continuous/Monthly |
| Workstations | Malware, phishing, insider threats | Medium | Quarterly |
| Legacy Systems | Outdated software, lack of security patches | High | Monthly/Quarterly |
| Cloud Services | Misconfigurations, API vulnerabilities | Medium-High | Continuous/Monthly |
| Mobile Devices | Loss/theft, malware, unauthorized access | Medium | Quarterly |
This table illustrates how different asset types carry varying levels of risk and require different assessment frequencies. Focusing on high-risk assets like client data servers and legacy systems should be prioritized. Regular assessments, ranging from continuous monitoring to quarterly checks, are essential for maintaining a strong security posture.
Risk Analysis That Drives Smart Security Decisions

This section explores how UK organizations are effectively quantifying cyber risks to make informed business decisions. It's about moving beyond theoretical risk matrices and focusing on practical applications that resonate with leadership and justify security investments.
Quantifying Risk for Clearer Decisions
Quantifying cyber risks successfully requires a balance between detailed analysis and practical application. Consider your specific business model and risk tolerance. A small design studio, for example, will have different priorities and resources than a large marketing agency. Focusing on impact assessment methods tailored to your organization is crucial.
Understanding the potential financial impact of a cyberattack is also key. Calculate potential losses from downtime, data breaches, and regulatory fines. This data provides a concrete basis for justifying security investments to leadership.
Scenario Planning for Cascading Effects
Scenario planning helps you understand the potential cascading effects of cyber risks without getting lost in theoretical what-ifs. Envision realistic attack scenarios and analyze their potential impact on different business areas.
This practical approach helps identify critical vulnerabilities and prioritize mitigation efforts. For instance, understanding how a ransomware attack could affect client projects, internal communications, and financial operations allows for effective resource allocation. This preparation minimizes the impact of potential disruptions.
Presenting Risk Analysis for Actionable Insights
Effective risk analysis needs clear communication to enable informed decision-making. Presenting risk data in a way that resonates with leadership is essential. Use clear visuals, focus on key metrics, and highlight the potential business impact of different risks.
Instead of complex dashboards, concentrate on metrics that reflect your security posture. This could include the number of critical vulnerabilities identified, the time taken to patch them, and the effectiveness of incident response procedures. The Cyber Security Breaches Survey 2025 highlighted a rise in operational breaches, with 7% of businesses reporting temporary loss of access to files or networks, up from 4% the previous year. Find more detailed statistics here. This emphasizes the need for practical security measures. This data-driven approach ensures that cybersecurity risk assessments translate into real-world improvements for UK businesses, strengthening defenses and protecting valuable assets.
Implementing Security Measures That Actually Protect You
Implementing robust security measures isn't just about checking compliance boxes. It's about creating a strategic approach that prioritizes genuine protection and keeps your business running smoothly. This section explores practical risk treatment methods used by successful UK businesses, balancing security needs with realistic budgets and timeframes.
Prioritizing Security Investments for Real Risk Reduction
Effective organizations focus on security investments that genuinely reduce risk, not just the latest vendor buzz. They understand that the most expensive solution isn't always the most effective. For instance, implementing multi-factor authentication (MFA) can dramatically reduce unauthorized access, often at a lower cost than other, less effective measures.
Investing in staff training and cybersecurity awareness is also crucial. Well-trained employees are less likely to fall victim to phishing attacks, a common entry point for cybercriminals. These practical steps offer substantial risk reduction for a reasonable investment.
To help understand the options available to UK businesses, the table below provides a comparison of different risk treatment approaches, their costs, effectiveness, and suitability for various scenarios.
Introducing the "Risk Treatment Options and Implementation Strategies" table, this comparison highlights key aspects of different security approaches, helping businesses make informed decisions about their cybersecurity investments.
| Treatment Type | Implementation Cost | Effectiveness | Best Use Cases | Timeframe |
|---|---|---|---|---|
| Multi-Factor Authentication (MFA) | Low to Moderate | High | Protecting access to sensitive systems and data | Immediate – Short Term |
| Employee Security Awareness Training | Low to Moderate | High | Reducing human error and vulnerability to phishing | Ongoing |
| Network Segmentation | Moderate | High | Isolating critical systems and limiting the impact of breaches | Short to Medium Term |
| Data Encryption | Low to Moderate | High | Protecting sensitive data at rest and in transit | Short Term |
| Intrusion Detection/Prevention System (IDPS) | Moderate to High | High | Detecting and blocking malicious network activity | Short to Medium Term |
| Regular Security Audits | Moderate | High | Identifying vulnerabilities and ensuring compliance | Ongoing |
| Incident Response Plan Development & Testing | Low to Moderate | High | Minimizing downtime and data loss in the event of a security incident | Ongoing |
Key takeaways from this table include the importance of balancing cost and effectiveness, and the need for ongoing security measures like training and audits. MFA, for example, offers a high level of protection at a relatively low cost, making it a valuable investment for most businesses.
Practical Security in Legacy Environments
Many UK businesses operate with legacy systems, which can create unique security challenges. Implementing security in these environments requires a pragmatic approach. Instead of replacing entire systems, which can be disruptive and expensive, prioritize isolating critical legacy systems from the main network and implementing robust access controls.
This approach minimizes risk without significant infrastructure overhauls. It also allows for gradual modernization over time. Focusing on practical, cost-effective solutions strengthens security without disrupting productivity.
Building an Executable Incident Response
A well-defined incident response plan is essential. But a plan that sits unused on a shelf is ineffective during a crisis. Effective incident response needs to be practical and executable. Regularly test and refine your plan. Conduct tabletop exercises to identify weaknesses and ensure your team knows their roles.
This proactive approach ensures a more effective response when an incident occurs. It also promotes continuous improvement, adapting to evolving threats and business needs. Learn more in our article about how to maximize your business resilience.
Realistic Business Continuity
Business continuity planning often focuses on large infrastructure investments. However, practical continuity can be achieved through simpler, more affordable steps. Cloud-based backups, for example, provide an offsite copy of essential data, protecting against data loss from local disasters.
Implementing redundancy for critical systems also minimizes downtime. This could involve having a backup server on standby if the primary server fails. These pragmatic steps ensure business operations can continue, even during unexpected disruptions.
Maintaining Productivity While Enhancing Protection
Balancing security and productivity is crucial. Security measures shouldn’t impede employee workflows. Explain the reasoning behind security policies to encourage understanding and cooperation. Implement user-friendly security tools that seamlessly integrate with existing processes.
This approach fosters a security-conscious culture without sacrificing productivity. It also empowers employees to participate in protecting the business. By focusing on practical, actionable strategies, UK businesses can establish robust security that effectively protects their operations in today’s challenging environment.
Building Sustainable Security Monitoring and Improvement
This section explores how UK businesses can transform cybersecurity risk assessment from a yearly task into a continuous, adaptable process. It's about creating monitoring systems that deliver real value without overwhelming security teams with excessive alerts and unhelpful metrics.
Building Monitoring Systems That Provide Real Insights
Many organizations grapple with security monitoring systems that produce more noise than actionable information. This can cause alert fatigue, where real threats get lost in a flood of low-priority notifications. Effective monitoring begins by identifying the key indicators that truly matter to your business.
For example, monitoring unusual file access patterns might be crucial for a creative agency, while tracking generic network traffic might be less important. Focusing on quality over quantity is key.
A few well-chosen metrics that reflect genuine risk reduction are more valuable than a dashboard filled with confusing numbers. Prioritize metrics aligned with your business objectives, such as the time it takes to patch critical vulnerabilities or the success rate of phishing simulations.
Integrating Risk Assessment Into Regular Business Processes
Successful UK companies integrate cybersecurity risk assessment into their everyday operations. This makes security a natural part of every decision, not just a last-minute addition. For instance, risk considerations are included from the outset when adopting new software or cloud services.
This involves security teams in project planning and procurement processes. By including security in these discussions, you proactively identify and address potential weaknesses. This integration ensures security measures align with business needs and don't hinder productivity.
Measuring Security Program Effectiveness Beyond Checklists
While compliance is essential, simply checking boxes doesn’t guarantee effective security. This section examines practical ways to measure what truly matters: actual risk reduction. This means going beyond checklists and evaluating the impact of security controls.
Regularly simulating real-world attacks is an effective method. This allows you to test incident response procedures, pinpoint vulnerabilities in your defenses, and quantify the potential damage of a successful attack. This information then informs targeted improvements, ensuring your security program stays robust and adaptable.
Creating Effective Feedback Loops and Maintaining Security Awareness
Continuous improvement relies on feedback. Establish mechanisms to learn from security incidents and near misses. This could involve post-incident reviews to understand what happened, how it could have been prevented, and what changes are necessary.
Feedback isn't limited to reacting to incidents. Regularly review your security program against evolving business needs. If your company expands into new markets or adopts new technologies, reassess your risk profile and adjust security controls accordingly.
Finally, don’t treat security awareness training as a yearly formality. Instead, develop engaging and relevant training programs that encourage behavioral change. This could involve interactive simulations, real-world examples, and ongoing communication to keep security top of mind. Building a culture of security awareness creates a "human firewall" – far more effective than any technical solution alone.
Navigating UK Compliance Without Losing Your Mind
The UK's cybersecurity compliance landscape is undeniably complex. But managing these regulations doesn't have to be a constant source of stress. This section offers practical advice from organizations successfully navigating GDPR, industry-specific rules, and emerging requirements. We'll explore how a well-executed cybersecurity risk assessment strengthens compliance without creating unnecessary bureaucracy.
Essential Documentation vs. Busywork
Knowing which documents truly matter for regulatory compliance is crucial. Many businesses waste time on paperwork that impresses auditors but doesn't enhance security. A robust cybersecurity risk assessment helps focus on documentation that showcases actual security improvements, not just flawless paperwork. This means prioritizing documents that demonstrate an understanding of your risks, the controls implemented, and how those risks are actively managed.
For instance, a documented and regularly tested incident response plan is far more valuable than a binder full of generic, unread security policies. This focused approach streamlines compliance and strengthens your overall security.
Industry-Specific Compliance Approaches
Different industries have unique compliance obligations. Financial institutions, for example, face more stringent regulations than marketing agencies. However, the core principles of a strong cybersecurity risk assessment remain universally applicable. Understanding your industry's specific rules and their interplay with broader UK regulations is vital.
This tailored strategy ensures you address the most relevant compliance obligations without unnecessary overhead. Sharing best practices within your sector can also offer valuable insights and simplify compliance efforts.
Preparing for Audits Effectively
Audits shouldn't be a cause for anxiety. Focusing on genuine security improvements allows you to approach audits with confidence. A cybersecurity risk assessment provides the evidence needed to demonstrate your commitment to security. It assures auditors that you understand your vulnerabilities, are actively managing them, and are continuously improving your defenses.
This proactive strategy is far more effective than scrambling for paperwork just before an audit. It fosters a culture of ongoing compliance that benefits your organization long-term.
Realistic Third-Party Risk Management
Many organizations struggle with third-party risk management, often imposing impractical requirements on suppliers and partners. This can strain relationships and hinder business operations. A practical approach focuses on understanding the actual risks associated with each third-party relationship. This involves evaluating their security practices and implementing appropriate controls without creating unnecessary obstacles.
For example, a small design studio working with a freelance designer likely doesn't need the same level of security controls as a large financial institution working with a major IT provider. A proportionate approach protects your organization without stifling collaboration.
Staying Ahead of Regulatory Changes
The regulatory landscape is constantly shifting, and staying informed can feel overwhelming. However, a proactive cybersecurity risk assessment helps you adapt to new requirements without constant worry. By continuously monitoring regulatory changes and integrating them into existing risk management processes, you can stay ahead of the curve.
This involves engaging with industry groups, subscribing to relevant alerts, and consulting with experts to understand the impact of new regulations. This forward-thinking approach allows you to anticipate changes and adapt your security program accordingly.
Protecting your creative agency or studio requires expert guidance and a calm, focused approach to IT security. InfraZen Ltd offers specialized services tailored to the unique needs of creative businesses in the UK, providing peace of mind without the tech headaches.
Article created using Outrank

