Keeping computer viruses at bay is about more than just installing some software and hoping for the best. It’s a combination of the right tech, smart daily habits, and a team that knows what to look out for. Think of it as a layered defence, where you’re actively keeping systems updated, browsing safely, and training your people to spot red flags like phishing emails.
Understanding the Real Threat to Your Business

For a creative business, a computer virus isn't just a tech headache; it’s a direct hit on your intellectual property, client data, and hard-earned reputation. The generic advice to "install an antivirus" just doesn't cut it anymore. Attackers aren’t only gunning for the big fish- they see small and medium-sized businesses as prime targets, often because they have fewer defences in place.
Preventing a virus starts with being honest about where you're vulnerable. Your most valuable assets- designs, client lists, strategic plans, financial records- are exactly what cybercriminals are after. A single breach can mean catastrophic data loss, crippling downtime, and a trust deficit with clients that’s tough to rebuild.
The Financial and Reputational Cost
The fallout from a cyberattack is very real and often severe. In the UK, the annual economic cost of cybercrime is estimated at a staggering £27 billion. For an individual business, recovering from an attack costs, on average, around £21,000.
What’s the most common way in? Phishing. It’s involved in an eye-watering 93% of business-related cyber incidents, which really hammers home the need for solid prevention strategies. You can read more about this in the government's official 2025 Cyber Security Breaches Survey.
This isn't just about the money, either. A successful attack can paralyse your operations, making you miss critical deadlines and damaging the professional relationships you’ve spent years building. The goal here isn't to scare you, but to set the stage for why the proactive, layered steps in this guide are so important.
Building a resilient security posture means shifting from a reactive mindset of fixing problems to a proactive one of preventing them before they happen. It’s about creating a defence that is as creative and dynamic as the work you produce.
A Modern Approach to Prevention
To properly safeguard your business, you need a strategy that weaves together technology, smart processes, and- crucially- an aware and vigilant team. Your defence should rest on a few key pillars:
- Robust Technical Safeguards: This goes way beyond basic antivirus. We're talking properly configured firewalls, secure network settings, and keeping all your software bang up-to-date.
- Human Awareness: Your team is your first line of defence, full stop. Ongoing training on how to spot phishing attempts and other social engineering tricks is absolutely non-negotiable.
- Proactive System Management: Think of this as essential maintenance. Regular updates, consistent data backups, and clear access control policies all work together to close security gaps before they can be exploited.
By focusing on these areas, you move beyond just reacting to threats and start building an environment that is genuinely secure. For a deeper dive, check out resources on identifying and mitigating network security risks. It's also worth getting familiar with the five most dangerous cyber threats that North East businesses face to understand what you're up against.
Building Your First Line of Technical Defence
Your software and settings are the gatekeepers for your entire business. Getting serious about preventing computer viruses starts with building a solid technical foundation- a set of digital defences that actively block threats before they can ever do any damage. This isn't about one magic piece of software, but a coordinated effort across all your systems.
A free antivirus program is certainly better than nothing, but for a creative business juggling valuable client data and its own intellectual property, it’s just the starting point. Today’s threats are far too sophisticated for yesterday's simple file scanners.
Choosing and Configuring Security Software
When you're looking for the right protection, you need to think in layers. Your security software should offer a multi-faceted defence against a wide range of attacks, because the days of a simple virus scanner are long gone.
So what does that look like in practice? Here are the features that actually matter:
- Real-time Scanning: This is completely non-negotiable. Your software must actively monitor files and processes as they run, catching threats the moment they appear, not just during a scheduled scan hours later.
- Behavioural Analysis: Clever new threats often disguise themselves to sneak past traditional signature-based scanners. Behavioural analysis is different; it watches for suspicious actions– like a program suddenly trying to encrypt all your files- and shuts it down, even if the threat is brand new.
- Dedicated Ransomware Defence: Ransomware can bring a creative business to a grinding halt. Look for software with specific features designed to shield your critical folders from unauthorised encryption, effectively creating a vault for your most important work.
A crucial part of building your first line of technical defence is selecting and implementing the best antivirus software for small business, offering real-time protection against malicious threats.
To help clarify the roles these tools play, here's a quick comparison of the essentials.
Essential Security Software Comparison
| Software Type | Primary Function | Key Features to Look For | Best For |
|---|---|---|---|
| Antivirus/Anti-malware | Detects and removes known malicious software (viruses, spyware, trojans). | Real-time scanning, behavioural analysis, automatic updates, low system impact. | Every single device, from laptops to servers. This is the baseline of protection. |
| Firewall | Monitors and controls incoming and outgoing network traffic. | Stateful inspection, application control, logging and reporting capabilities. | Protecting the network perimeter (router) and individual devices (OS firewall). |
| Browser Security Extension | Blocks malicious scripts, ads, and trackers within your web browser. | Script blocking, ad/tracker filtering, phishing protection, privacy controls. | Hardening the primary tool used for accessing the internet, reducing web-based threats. |
Having a combination of these tools creates a much stronger, layered defence than relying on just one.
Fortifying Your Digital Perimeter with Firewalls
Beyond antivirus, your firewall is your network's front door to the internet. You have one on your operating system and another on your network router- both need to be switched on and configured properly to be effective. Think of them as a security guard, inspecting all traffic coming and going, and blocking anything that looks suspicious or doesn't have permission.
For most businesses, the goal is simple: block all unsolicited incoming traffic. This stops random connection attempts from across the internet, which is a common way attackers probe your network for weaknesses. Taking a few minutes to get this right creates a powerful barrier. This strategy is a key part of a bigger security picture, and you can learn more about this by understanding what is endpoint security in our detailed guide.
A well-configured firewall doesn't just block attacks; it gives you valuable insight into the traffic flowing through your network, helping you spot unusual activity that might signal a deeper problem.
Enhancing Browser Security
So much of our daily grind happens inside a web browser, making it a massive entry point for viruses. Malicious scripts, intrusive trackers, and booby-trapped adverts are all common vectors for infection. The good news is you can significantly harden your browser's defences with a few smart extensions.
Look at installing extensions that specifically focus on:
- Blocking Scripts: Tools that give you control over which scripts can run on a webpage can stop many "drive-by-download" attacks in their tracks.
- Ad and Tracker Blocking: Many malicious ads look identical to legitimate ones. Blocking them entirely removes a huge threat vector and, as a bonus, often makes websites load faster.
- Link Inspection: Some extensions can check links for known threats before you even click them, adding another handy layer of proactive defence.
The infographic below shows the simple but essential process for keeping your software secure- a critical routine in preventing viruses.
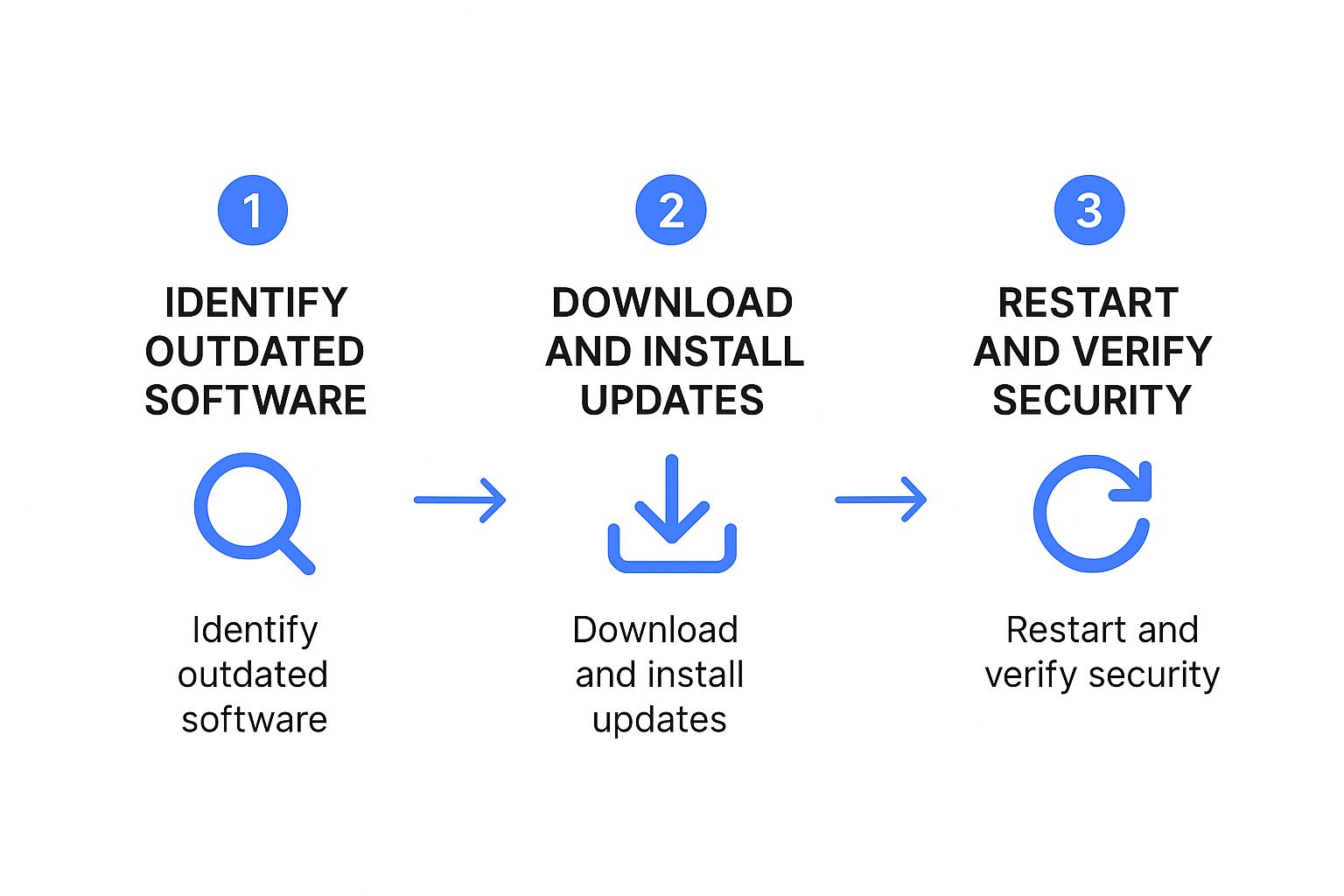
This simple three-step flow- identify, update, and verify- shows how basic maintenance directly closes the security gaps that attackers love to find and exploit. Being proactive with these technical tasks is fundamental to keeping your business safe.
The Human Element: Your Team as a Security Asset

You can have the most sophisticated security software on the market, but it has a blind spot- it can't stop a team member from unintentionally opening the door to an attacker. Technology is a critical piece of the puzzle, but your team is arguably the most important layer in your entire defence strategy.
When you build a culture of security awareness, you turn a potential vulnerability into your greatest asset. This goes way beyond a one-off training session; it's about embedding secure practices into your daily creative operations. After all, the most common entry points for viruses- phishing emails, dodgy links, and malicious attachments- all rely on a human clicking "yes." A well-informed team member is a powerful gatekeeper.
Training Your Team to Spot Deception
Let's be blunt: the single biggest threat facing your business is phishing. Attackers have become exceptionally good at crafting emails that look genuine, often pretending to be trusted clients, suppliers, or even the CEO. One wrong click on a malicious link can bypass all your technical defences in an instant.
That’s why ongoing training isn't a 'nice to have'- it's absolutely essential. Your team needs to be able to instinctively spot the red flags that give away a phishing attempt.
What does that look like in practice?
- Spotting Urgency and Pressure: Attackers love creating a false sense of panic. An "overdue invoice" or a "final warning" is designed to make people act before they think.
- Noticing the Small, Off-Kilter Details: This could be a sender's email address that’s one character off, or a company logo that looks slightly pixelated. These are classic tells.
- Questioning Unusual Requests: A sudden request to change bank details for a payment or a demand for login credentials should set alarm bells ringing immediately.
Running regular, simulated phishing campaigns gives your team practical experience in a safe environment. It builds muscle memory, making it second nature to pause and scrutinise an email before clicking. A great place to start is by exploring ways of strengthening your team's defense with essential cyber hygiene.
Implementing Strong Password Policies
Weak or reused passwords are an open invitation for attackers. Once a single account is compromised, a virus can spread like wildfire across your network. A clear, enforceable password policy is the foundation for preventing this.
Your policy doesn’t need to be complicated. It's not about making passwords impossible to remember, but making them incredibly difficult for a machine to guess.
Here are the key elements of a solid policy:
- Complexity Rules: Enforce a minimum length of 12 characters and require a mix of upper and lower-case letters, numbers, and symbols.
- Uniqueness is Non-Negotiable: A password must be unique for every single service. If one gets stolen, the attacker doesn't get the keys to your entire collection of accounts.
- Use Password Managers: Actively encourage- or even require- a reputable password manager. These tools generate and store complex, unique passwords for every site, so your team only has to remember one master password.
- Mandate Multi-Factor Authentication (MFA): Make MFA mandatory wherever it's available. This simple step adds a massive security boost by requiring a second check (like a code from a phone app) before granting access.
A password manager combined with MFA is one of the most powerful and practical security combinations a business can implement. It drastically reduces the risk of account takeovers, which are a primary gateway for malware infections.
Safe Practices for Removable Media and Remote Work
Your security perimeter isn't just the office network anymore. With remote work and the routine use of USBs, potential entry points for viruses have multiplied. You need clear guidelines to ensure these modern conveniences don't become vulnerabilities.
For USB drives and other removable media, the rule should be simple: assume they are untrustworthy until proven otherwise. Never, ever plug in a found or unfamiliar USB stick. Any company-approved drives should be automatically scanned by your security software the moment they're connected.
Remote access comes with its own set of rules. Your team needs to understand that their home network is now an extension of the business's.
Consider these non-negotiables for secure remote access:
- Always Use a VPN: Every connection back to the company network must go through a secure Virtual Private Network (VPN), which encrypts all the traffic.
- Secure Home Wi-Fi: Staff must ensure their home Wi-Fi is password-protected using a strong encryption standard like WPA2 or WPA3.
- Company-Managed Devices: Whenever possible, remote work should happen on company-provided devices. This ensures they have the right security software and configurations already installed and managed by your IT team.
Imagine this real-world scenario: a designer downloads a 'free' font from a shady website onto their personal laptop, which they then use to connect to the company server. The font file contains a hidden keylogger virus, which captures their login details. Just like that, an attacker has access. Ongoing training on safe downloading practices and the risks of using personal devices is what stops this exact situation from happening to you.
Keep Your Digital House in Order
Think of your cybersecurity like servicing a car. You don't just fill it with petrol once and expect it to run forever. It needs regular maintenance to stay reliable. The same logic applies to your systems and data; effective virus prevention is an ongoing process of good housekeeping.
Without this continuous attention, even the best security software will eventually develop cracks in its armour. Attackers are relentless, constantly hunting for new vulnerabilities. Your job is to close those security gaps before they can be found and exploited. This is where a disciplined approach to system and data management becomes your most powerful defensive tool.
Patch Everything, All the Time
One of the most common ways a virus gets in is through a known security hole in outdated software. It’s like leaving a window open in your house. Developers are constantly releasing updates- or patches– to fix these vulnerabilities, but they only work if you actually install them.
This applies to everything on your network, not just the obvious stuff:
- Operating Systems: Both Windows and macOS release regular security updates that are critical for addressing newly discovered threats.
- Creative Applications: Your entire Adobe Creative Suite, project management tools, and accounting software can all have vulnerabilities.
- Plugins and Extensions: Those handy browser add-ons and website plugins are often overlooked, but they are a favourite target for attackers.
Putting off an update because you’re deep in a project is a risky gamble. The best first step is to enable automatic updates wherever you can. But don't stop there. Get into the habit of manually checking for updates on your most critical apps at least once a week. It’s a simple routine that dramatically shrinks the window of opportunity for an attack.
Your Ultimate Safety Net: The 3-2-1 Backup Rule
No matter how strong your defences are, you have to plan for the worst-case scenario. A rock-solid backup strategy is your ultimate safety net, ensuring that if a ransomware attack ever slips through, you can restore your data without paying a penny to criminals. The gold standard here is the 3-2-1 rule.
It’s a simple concept but incredibly effective:
- Three Copies: Always keep at least three copies of your data- the original on your main machine, plus two backups.
- Two Different Media Types: Store those backups on at least two different kinds of storage, like an external hard drive and a cloud service. This protects you if one type of media fails.
- One Off-Site Copy: Make sure at least one of those backup copies is stored completely off-site. This could be in the cloud or a physical drive you keep at another location.
This strategy ensures that a single event- like a fire, theft, or a virus that encrypts your local network- can't wipe out all your precious work. For most creative businesses, a daily automated backup to a secure cloud service is a practical and powerful place to start.
A well-executed backup strategy is more than just a recovery tool; it's a statement of resilience. It means you can confidently refuse a ransom demand, knowing your business's critical data is safe and accessible.
Give People Only the Keys They Need
Another powerful strategy is the principle of least privilege. Put simply, this means every user and every account should only have the absolute minimum permissions they need to do their job- and nothing more. If an account gets compromised, this approach dramatically limits the potential damage.
For example, a freelance copywriter doesn't need access to your company's financial records. A junior designer doesn't need administrator rights to the main server. If that junior designer's account is compromised through a phishing email, the attacker's access is confined to a very small, contained area. They can't move across your network to more valuable targets.
Putting this into practice involves a couple of key steps:
- Review User Permissions: Regularly audit who has access to what. If they don't need it anymore, remove it.
- Use Standard User Accounts: Avoid handing out administrator accounts for daily work. Staff should use standard accounts and only use an admin account when it's absolutely necessary for a specific task.
This approach is crucial for containing threats. The government's 2025 Cyber Security Breaches Survey revealed an alarming statistic: 43% of UK businesses (around 612,000 organisations) suffered a cyber breach or security incident. You can explore more UK cybersecurity statistics to understand the full scope of the threat, but the message is clear. Proactive measures like the principle of least privilege are essential to avoid becoming part of that statistic.
Advanced Strategies for Heightened Security
If your creative business handles sensitive client files, your own intellectual property, or any kind of financial data, the basics we’ve covered are just your starting point. To build a truly resilient defence, you need to layer in strategies that can contain and neutralise threats even after they get past your first line of defence.
These aren't your everyday security tips. They're deliberate, structural choices that take your security from standard to seriously robust. They do require a bit more planning, but the level of protection they offer against sophisticated attacks is worth every bit of effort.
Containing Threats With Network Segmentation
Picture this nightmare scenario: a single virus infects a designer's workstation and spreads like wildfire across your entire network. In minutes, every machine is locked up, from the design team to the accounts server. Network segmentation is the architectural fix that prevents this from ever happening.
Put simply, it’s the practice of dividing your network into smaller, isolated sub-networks or 'segments'. Think of it as installing digital fire doors in your office- if a fire breaks out in one room, it’s contained and can't easily spread to the others.
This approach gives you some powerful advantages:
- Breach Containment: If a workstation in the design department gets hit, the malware is trapped there. It can't just hop over to the finance network where your critical accounting data lives.
- Reduced Attack Surface: An attacker who gets a foothold in one area can’t see or access your entire infrastructure, making it much harder for them to move laterally and hit their real target.
- Improved Monitoring: It’s far easier to monitor traffic moving between these segments, helping you spot unusual activity that could signal an attack in progress.
Implementing network segmentation is a core part of building a multi-layered defence. You can explore the advantages of adopting a defense-in-depth cybersecurity strategy in more detail in our dedicated guide.
The Power of Application Whitelisting
Most standard antivirus software works by keeping a 'blacklist' of known threats and stopping them. Application whitelisting completely flips that model on its head. Instead of blocking what’s known to be bad, you explicitly define what’s allowed to be good.
With application whitelisting, you create a definitive list of approved programs that are allowed to run on your systems. Everything else is blocked by default. This is one of the single most effective ways to prevent computer viruses, as unknown or malicious executables simply cannot run.
For a creative agency, your "whitelist" might only include Adobe Creative Cloud, your project management software, office apps, and specific web browsers. If a team member accidentally downloads malware disguised as a font pack, it won’t run. Why? Because it’s not on your pre-approved list.
This strategy is incredibly effective against zero-day attacks- brand new threats that security researchers haven’t even identified yet. Because the malware isn't on your list, it's dead on arrival.
Preparing for the Worst With an Incident Response Plan
Let's be realistic: no defence is ever 100% impenetrable. That’s why having a formal, documented incident response plan is the mark of a truly mature security strategy. This is your step-by-step playbook for the moment you suspect something has gone wrong.
A solid plan removes panic and guesswork, ensuring you can react swiftly and in an organised way to minimise the damage. It should clearly spell out:
- Key Contacts: Who needs to be told immediately, from your IT support to the leadership team.
- Immediate Actions: The first critical steps, like disconnecting affected machines from the network to stop a virus from spreading further.
- Recovery Procedures: How to restore data from backups and bring systems back online safely.
- Post-Incident Analysis: A process for figuring out how the breach happened and, crucially, how to stop it from happening again.
The unfortunate reality is that UK businesses are a major target. In 2025, the United Kingdom became the third most targeted nation for malware attacks globally, with a 7% increase in threats from one quarter to the next. You can discover more insights about UK malware attacks on dailysecurityreview.com. Having a plan ready isn’t paranoia; it's simply responsible business.
Common Virus Prevention Questions Answered
Even with a solid strategy, there are always a few lingering questions. Getting these sorted is the difference between knowing the theory and confidently putting it into practice.
Let's clear up some of the most common queries we hear from creative businesses. These are the details that often make or break how well your security holds up when it matters.
Is Free Antivirus Software Good Enough?
Honestly, for a business, the answer is almost always no. While a free antivirus program is a huge step up from having nothing, it’s rarely enough to protect a company.
Free versions are designed for basic malware scanning. They simply don't have the muscle to fight off modern, sophisticated attacks. Professional security suites come packed with critical tools like an advanced firewall, real-time threat detection that spots suspicious behaviour, and- most importantly- dedicated ransomware protection. If you handle client data or your own valuable creative work, investing in a proper security solution isn't just a good idea; it's a necessary cost of doing business.
How Often Should I Back Up My Data?
This really comes down to one question: how much work are you willing to lose? For most creative businesses, an automated daily backup is the perfect starting point. It means you’ll never lose more than a single day’s progress.
But if your team is deep in a project with constant, heavy file changes- think video editing or complex 3D modelling- you might want to back up even more frequently. The key is to stick to the 3-2-1 rule: keep at least three copies of your data, store them on two different types of media, and make sure at least one copy is off-site or in the cloud.
A consistent, well-managed backup routine is your ultimate safety net. It's the single most effective tool you have for recovering from a severe malware attack, like ransomware, without even thinking about paying a ransom.
Can Mac Computers Get Viruses?
Yes. Absolutely. This is one of the most persistent- and dangerous- myths out there. While macOS has strong security features and wasn’t historically a prime target, those days are long gone.
As Apple's market share has exploded, Macs have become a very attractive target for cybercriminals. Malware built specifically for macOS is now worryingly common. Mac users need to follow the exact same security best practices as Windows users. That means using reliable anti-malware software, being smart about downloads, and keeping your OS and all your apps updated. Assuming your Mac is invincible is a huge security risk.
At InfraZen Ltd, we take the complexity out of cybersecurity so you can focus on your creative work. We build resilient, proactive IT strategies that protect your valuable assets and keep your business running smoothly. To see how your current setup stacks up, check out our services.

