What Is Internal Penetration Testing (And Why Creatives Need It)

Imagine your Manchester-based creative agency as a castle. You've built strong walls and a formidable gate (your external security). But what if a threat lurks within? What if someone slips past the defenses disguised as a friendly face, or worse, a trusted guard turns rogue? This is where internal penetration testing comes into play.
Internal penetration testing simulates an attack originating from inside your network. It assumes a threat actor—a disgruntled employee or a compromised account—already has a foothold within your systems. Think of it as hiring an ethical hacker, your own "friendly" intruder, to probe for weaknesses from the inside.
This approach uncovers vulnerabilities that external tests might miss. Imagine discovering that sensitive client folders are accessible to everyone, or an outdated software application acts as an unguarded backdoor. These are the kinds of risks internal penetration testing helps identify.
The UK Cyber Landscape: Why Internal Testing Matters
This isn't just a theoretical exercise. The UK's cyber landscape underscores the very real need for robust internal security measures. The Cyber Security Breaches Survey 2025 reveals that 43% of UK businesses reported a cyber breach or attack in the past year. While this is down from 50% the previous year, it highlights that cyber threats remain a significant concern. Learn more about UK cyber breaches here.
Creative Agencies: High-Value Targets
For creative agencies, the stakes are particularly high. You possess a treasure trove of valuable assets: unreleased campaigns, client databases, confidential briefs, and precious intellectual property. This makes you a prime target for cybercriminals.
Internal penetration testing acts as a proactive shield, identifying weaknesses before a real attacker exploits them. It's like checking for structural flaws in your castle before the siege begins, preventing reputational damage, financial loss, and the strain of fractured client relationships.
Understanding Potential Fallout
This type of testing focuses on the potential consequences of unauthorized internal access. Could someone access financial records? Leak a confidential campaign? Impersonate your agency? Understanding these risks is the cornerstone of building a resilient security posture. It empowers you to prioritize your security efforts and invest wisely.
Why Creative Agencies Are Digital Goldmines For Cybercriminals
Creative agencies are treasure troves of valuable digital assets, often without fully realizing it. Think unreleased campaigns, confidential client strategies, celebrity endorsements, and even potential access to client systems. This isn't just your agency's data; it's your clients' most prized possessions.
This makes creative agencies a prime target for cybercriminals. Imagine a hacker gaining access to a major retailer's Christmas campaign or confidential research for a new pharmaceutical product. The potential payoff is enormous.
The very nature of creative work also creates unique vulnerabilities. The focus is often on creative tools and software, with security sometimes taking a backseat. Teams frequently work remotely, across various devices, and collaborate with external freelancers, multiplying the potential entry points for an attack. Sharing large files across multiple platforms adds another layer of complexity to security management.
Security Lapses Can Have Big Repercussions
A seemingly small security lapse can have devastating consequences. Unlike large corporations with dedicated security teams, many creative agencies operate with leaner structures, where security might not be anyone's primary responsibility.
The evolving threat landscape underscores the need for regular internal penetration testing. The Cyber Security Breaches Survey 2025 reveals that while the overall number of breaches might have dipped slightly, threats like phishing and ransomware remain prevalent. Over 7.7 million attacks targeted UK businesses, highlighting the critical importance of regular penetration tests to identify weaknesses. Learn more about these evolving threats: UK Cybersecurity Statistics 2025.
Interested in learning more about risk assessment? Check out this helpful resource: Cybersecurity Risk Assessment. Internal penetration testing provides a crucial defense, specifically targeting vulnerabilities within creative workflows. Think of it as having a friendly expert burglar test your locks before the real thieves show up. Through simulated attacks, internal testing reveals weaknesses in your systems, processes, and even employee practices, providing actionable insights to bolster your defenses.
Inside An Internal Penetration Test: What Actually Happens
Think of an internal penetration test like hiring a friendly burglar to test your locks before the real thieves come knocking. It's a crucial process for creative agencies in the UK, helping you find and fix weak spots in your security before they turn into major headaches. The infographic below gives you a visual overview of the initial planning stages.
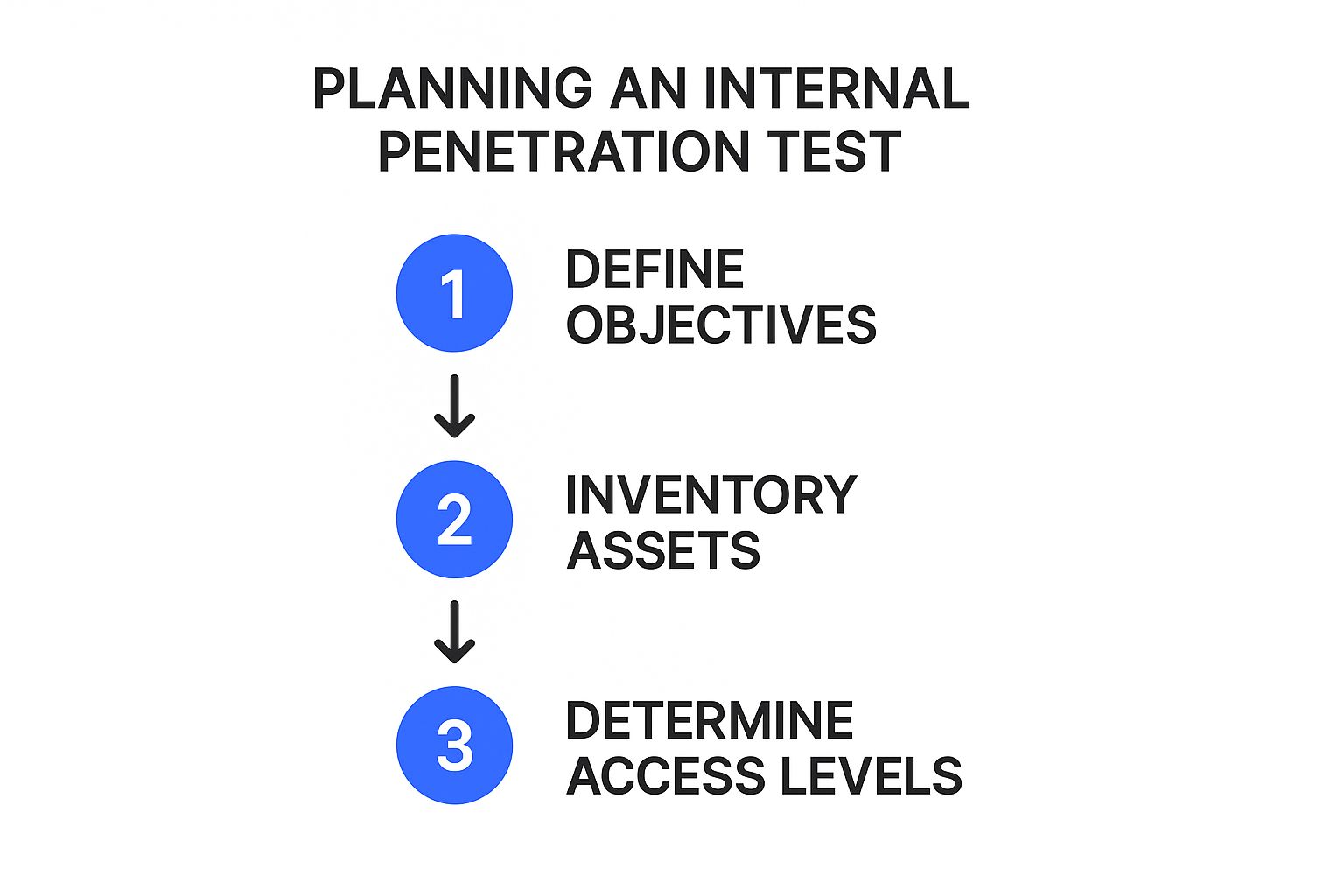
As you can see, a solid foundation for a successful test involves clearly defining your objectives, taking stock of your digital assets, and figuring out the right access levels. This upfront work ensures the test is tailored to your specific needs and priorities.
Reconnaissance: Mapping Your Digital Terrain
The first phase is reconnaissance. Just like a detective gathering clues, the testers begin by mapping your internal network. They'll identify every connected device—servers, workstations, printers, even smart TVs—to understand your agency’s digital layout and potential entry points.
This detailed map helps them spot those less obvious, often overlooked, connections that could be a backdoor for a malicious actor.
Vulnerability Scanning: Checking for Weak Spots
Next up is vulnerability scanning. Imagine a building inspector meticulously checking for structural flaws. Testers systematically search for security weaknesses, like outdated software, default passwords, misconfigured systems, and overly permissive file sharing. This stage highlights the areas that need immediate attention. It's about finding those cracks in the walls before they become gaping holes.
Exploitation: Simulating Real-World Attacks
Now comes the exploitation phase. Within pre-agreed boundaries, ethical hackers try to use the identified vulnerabilities to gain deeper access. Think of it as a controlled experiment, not a demolition derby. The goal isn't to break things, but to understand how a real attacker might operate. For example, they might discover that an intern's laptop has unnecessary admin privileges or that client project folders are accessible to more people than they should be.
Post-Exploitation: Assessing Potential Damage
After a simulated attack, the post-exploitation analysis kicks in. This phase assesses the potential fallout. Could someone steal client campaigns? Access financial records? Impersonate your agency in client communications? This step quantifies the risks—putting a concrete value on the potential damage—and gives you actionable insights. It's about understanding not just that something could go wrong, but how bad it could be.
Reporting and Recommendations: Turning Insights into Action
The final stage is a detailed report, translating technical jargon into plain English. The report outlines practical business risks and actionable recommendations. This becomes your roadmap for strengthening your agency's security posture. It's your guide to locking all the doors and windows, reinforcing the walls, and installing a state-of-the-art security system. Professional testers understand the importance of minimizing disruption. They'll often schedule tests during off-hours, ensuring your creative workflows remain uninterrupted while your security gets a much-needed boost.
To help visualize the entire process, let’s look at the following table:
Internal Penetration Testing Process Phases
A breakdown of the key phases in internal penetration testing and what happens in each stage
| Phase | Activities | Duration | Expected Outcomes |
|---|---|---|---|
| Reconnaissance | Network mapping, device identification, information gathering | 1-2 days | Comprehensive map of the internal network, identification of potential entry points |
| Vulnerability Scanning | Automated scans for known vulnerabilities, manual checks for misconfigurations | 2-3 days | List of security weaknesses prioritized by severity |
| Exploitation | Attempts to leverage vulnerabilities to gain unauthorized access | 2-3 days | Proof of concept demonstrating how vulnerabilities can be exploited |
| Post-Exploitation | Analysis of the potential impact of successful attacks | 1-2 days | Quantification of risks, identification of sensitive data at risk |
| Reporting and Recommendations | Documentation of findings, recommendations for remediation | 1 week | Actionable report outlining vulnerabilities and mitigation strategies |
This table summarizes the key activities, estimated durations, and expected outcomes of each phase. Keep in mind that these are estimates and can vary based on the complexity of your agency’s network. The important takeaway is the structured approach each phase provides, leading to a comprehensive understanding of your security posture.
Choosing Your Internal Penetration Testing Approach

Not every creative agency in the UK needs the same level of internal penetration testing. Finding the right fit for your agency is a bit like choosing the right insurance policy—you want enough coverage without paying for extras you don't need. Let's explore the different methods and how to pick the best one for your creative business.
Understanding the Testing Spectrum
Internal penetration testing comes in a few different forms. White-box testing gives the testers complete access and knowledge of your systems. Think of it like giving a detective a blueprint of the building—they can meticulously examine every corner. This allows for a really deep dive, but it might not show how a real attacker, working in the dark, would actually try to get in.
On the other hand, black-box testing simulates a real insider threat. The testers start knowing absolutely nothing about your systems, just like a real-world attacker. This gives you valuable insight into how a malicious insider might operate, but it could potentially miss vulnerabilities hidden deeper within your systems. It's more like a surprise inspection—testing your immediate defenses.
Then there's grey-box testing, which sits somewhere in between. Testers get some inside information, maybe login details or system diagrams, but not the complete picture. This often strikes the right balance for creative agencies, offering a good mix of realism and thoroughness. It's like giving the detective a floor plan but not the security codes.
To help you visualize the differences, let's look at a comparison table:
Penetration Testing Approaches Comparison
Comparison of different penetration testing methodologies suitable for creative agencies
| Testing Type | Information Provided | Cost Level | Best For |
|---|---|---|---|
| White-box Testing | Full system knowledge | High | Deep system analysis, identifying all potential vulnerabilities |
| Black-box Testing | Zero system knowledge | Medium | Simulating real-world attacks, assessing external defenses |
| Grey-box Testing | Partial system knowledge | Medium | Balancing realism and thoroughness, suitable for most agencies |
This table highlights how the level of information provided impacts the cost and overall suitability for different needs. While white-box offers the most comprehensive analysis, grey-box often provides the best value by balancing cost and the realism of a potential attack.
Tailoring the Approach to Your Agency
For smaller creative studios in the UK, focusing internal penetration testing on the most important systems—like client file servers and creative software—often makes the most sense. It's about protecting your most valuable assets without overspending.
Larger agencies, with more complex networks and potentially higher-value client data, might need a more comprehensive approach. This could include testing everything from individual computers to cloud integrations. This broader approach provides a better overall security picture.
You might also be interested in: Proactive Cybersecurity: How to Maximize Your Business Resilience
Compliance and Timing Considerations
UK creative agencies also need to think about regulations. If you work with clients in finance, healthcare, or government, specific industry standards might determine which testing approach you need. Meeting these standards ensures you’re operating legally and protecting sensitive client data.
Timing also matters. It's smart to coordinate testing around quieter periods, avoiding major campaign launches or client presentations, to minimize disruptions to your creative workflows. Planning ahead and scheduling strategically helps you get the most out of the testing without impacting deadlines. Ultimately, choosing the right approach is about finding the balance between security, practicality, and budget. It's about getting the most useful insights into your actual security without disrupting your creative flow.
Building Security Culture In Creative Teams
Building a strong security culture within your UK creative team is just as important as having strong technical defenses. Think of it like this: even the best lock in the world won't help if someone leaves the key under the mat. Similarly, even the most sophisticated internal penetration testing won't fully protect your agency if team members accidentally create security gaps through their daily activities. Finding this balance requires a careful approach, making sure security works with the fast-paced, collaborative nature of creative work, not against it.
Understanding the Creative Workflow
First, you need to understand how creatives work. They're constantly sharing files, often work outside of typical 9-to-5 hours, use personal devices for inspiration, and collaborate with external freelancers and clients. Meeting campaign deadlines often takes priority over strict security protocols. This isn't about negligence; it's simply the reality of a demanding, deadline-driven industry.
Instead of imposing rigid rules that creatives will likely find ways around, integrate security seamlessly into their existing workflow. Think of it like providing the right tools for a job: if the secure options are actually easier and more efficient than the workarounds, your team will naturally use them. For instance, provide a file-sharing platform like ShareFile that’s genuinely better than using email attachments or consumer-grade cloud storage like Dropbox. Offer password managers that truly save time and hassle.
Empowering Creatives Through Education
Security awareness training needs to be relevant to the creative industry. Ditch the generic corporate scenarios and use relatable examples. Imagine a training session that uses real-world examples of phishing attacks targeting UK agencies, such as fake collaboration requests or urgent (but fake) client demands. This approach will resonate far more than abstract warnings about clicking suspicious links. For a broader perspective on security strategy, you might be interested in: Learn more about a defence-in-depth cybersecurity strategy.
Learn from UK agencies that have already built strong security cultures. Often, this involves including creative teams in finding practical solutions, rather than dictating policies from the top down. This collaborative approach not only gets everyone on board but also uses the team's inherent creativity to discover innovative security solutions.
The Human Element: Addressing Social Engineering
A critical aspect of internal security is addressing the human element. Creative professionals are often targeted with very specific social engineering tactics. These could include fake collaboration requests from seemingly legitimate industry figures, urgent client demands requiring immediate action, or offers of exclusive creative resources. Training your team to recognize these tactics is crucial.
Fostering a Security-First Mindset
The ultimate goal is to create an environment where security awareness actually boosts creative excellence, not hinders it. When security becomes a natural part of the creative process, your team becomes your strongest security asset, not a potential vulnerability. They become the first line of defense, spotting potential threats and contributing to a more resilient and secure agency. This shift in mindset is the foundation of a truly effective security culture.
Making Internal Testing Work For Your Creative Budget

This screenshot from Gartner offers a glimpse into their market research on tech, including security. Their expertise is a valuable resource when UK creative agencies are considering where to invest in security. Understanding market trends and best practices is key to making informed decisions.
Let's face it: budgets for creative agencies, especially in the UK, are often stretched thin. Every penny has a purpose, and security can sometimes feel like a "nice-to-have" rather than a must-have. Internal penetration testing might seem like an extra expense you can skip.
But think about this: what's the cost of a security breach? Imagine losing a major client because their campaign was leaked. Or facing hefty fines for compromised data. What about the hit to your reputation if a security incident goes public? These scenarios quickly make the investment in internal penetration testing look pretty reasonable.
It's a bit like insurance. A smaller upfront cost protects you from potentially catastrophic financial and reputational damage down the line.
Making Smart Investments in Security
For smaller creative studios, an annual internal penetration test might be less than a month's rent. Larger agencies might budget the equivalent of a junior designer's monthly salary for a more in-depth assessment. Looking at it this way, security spending becomes a manageable, predictable operating expense.
The growth of the penetration testing industry itself speaks volumes. Gartner projects it to be a $4.5 billion industry globally by 2025. This increased demand is reflected in the UK's competitive job market for penetration testers, with salaries ranging from £33,000 for entry-level roles to £50,000 or more for senior positions. Dive deeper into penetration testing industry statistics.
Creative Funding for Creative Security
There are clever ways to incorporate security costs into your existing budget. Some agencies build these costs directly into client contracts, framing it as part of their commitment to data protection. Others treat internal penetration testing like other essential business insurance, similar to professional indemnity or public liability coverage.
Many agencies find that demonstrating robust security practices actually attracts bigger, more security-conscious clients. This shifts security from a cost center to a revenue driver.
Strategic Timing and Cost Savings
Even the timing of your testing can impact cost. Scheduling during quieter periods can often result in more thorough testing at lower rates, maximizing your security investment.
Internal penetration testing can also uncover unexpected cost savings. It can identify inefficiencies in your IT setup, highlight redundant software licenses, or reveal security tools that aren't providing value. These benefits can offset the initial testing cost.
The key takeaway? Internal penetration testing isn't just an expense; it's an investment in your agency's reputation, client trust, and long-term success.
Your Creative Agency's Security Action Plan
Now that you understand why internal penetration testing is so vital for creative agencies, especially in the UK, let's talk about how to actually make it happen. Don't worry, we're not building Fort Knox here. It's about creating practical, sustainable security that protects your business and keeps your clients happy.
Phase One: Building a Strong Foundation
Imagine you're building a house. You wouldn't start with the fancy rooftop terrace, right? You'd begin with the foundation. Similarly, a security baseline assessment is the groundwork for your agency's security. This means taking stock of your current security setup, figuring out what your most valuable assets are (client data, creative projects, core systems), and honestly assessing where you're vulnerable. Think about it: What are your password practices like? How do you share files, both internally and with clients? Where does all that precious client data live? These are the kinds of questions a baseline assessment helps you answer.
It's like taking inventory of your current security toolkit and seeing which tools you’re missing.
From there, focus on the essentials. Make sure all your software is up-to-date, patching those known weaknesses that attackers love to exploit. Set up proper access controls for client projects, ensuring only the necessary people can access sensitive information. And establish secure file-sharing practices that your creative team will actually use. Maybe that means adopting a new platform that’s more intuitive than whatever workarounds are currently in place. This phase is about setting those basic security standards that everything else builds upon.
Phase Two: Your First Internal Penetration Test
This is where the ethical hackers come in – think of them as friendly burglars testing your newly strengthened defenses. When choosing a provider, make sure they understand the specific needs of creative agencies. Don't just go for the cheapest option. Look for a firm that gets your workflow, the type of data you handle, and the UK compliance requirements you face.
Timing is key. Plan your test around your project cycles, ideally during quieter periods to minimize disruption to client work. Prepare your team by explaining the process and addressing any concerns. This isn't an IT audit designed to catch people out; it's a collaborative effort to improve security practices for everyone.
Strategic planning also helps manage costs, taking advantage of quieter periods when testing rates might be lower.
Phase Three: Taking Action and Measuring Success
Once the internal penetration test is complete, don't just file the report away and forget about it. Prioritize fixes based on actual business risk, not just how technically severe a vulnerability might seem. A small technical flaw that could lead to a major client data breach is far more important to fix than a high-severity technical issue with minimal real-world impact.
When implementing changes, focus on solutions that enhance your creative workflow, not hinder it. Security should support creativity, not stifle it. Document everything you change so you have a clear record of your progress.
Set realistic timelines for implementation, perhaps spreading changes out over 3-6 months to avoid disrupting ongoing client work. Remember, security is an ongoing process, not a one-time fix.
So, what does success look like? Fewer security incidents, increased client trust, faster project approvals from security-conscious clients, and a team that's more aware of security best practices. The goal isn't to achieve perfect security overnight. It's about cultivating a culture of security that protects your creative business while still allowing for the collaborative, innovative work that makes your agency thrive.
Ready to strengthen your agency's security? Contact InfraZen today for a tailored security assessment and expert guidance on internal penetration testing. Learn more about InfraZen's cybersecurity services for creative agencies.
Article created using Outrank

