Picture this: a dedicated security team for every single laptop, phone, and server in your business, watching for trouble 24/7. That's the core of Managed Endpoint Detection and Response (EDR). It's not just another piece of software; it's a complete service that pairs advanced technology with human cybersecurity experts to protect your company’s most vulnerable entry points.
Unpacking Managed Endpoint Detection and Response
To really get what managed EDR is, imagine hiring a team of elite security guards who bring their own high-tech surveillance gear. You don't just get the cameras (the EDR technology); you get the skilled professionals who monitor the live feeds, investigate anything suspicious, and step in to stop threats before they can cause any real damage.
In the past, we relied on traditional antivirus software. Think of that as a simple alarm on a door—it’s decent at stopping a clumsy intruder who tries to force their way in. But it's completely blind to a clever thief who picks the lock or slips through an open window.
Modern cyber threats are far more subtle. They don't always use known malware that an antivirus can easily spot. Instead, attackers might use compromised employee credentials or exploit tiny, unknown software flaws to quietly gain access. This is where even a standard EDR tool can fall short. It will flood an IT department with alerts, but it takes an expert to figure out what they all mean.
A standard EDR platform is a powerful engine, but it needs a skilled driver. Without dedicated security analysts, the constant stream of alerts just becomes overwhelming noise, making it almost impossible to spot genuine threats among all the false positives.
The 'Managed' Difference
This is where the "managed" part is so crucial. A managed EDR service gives you both the high-tech engine and the expert driver. It solves a huge problem for businesses, especially creative agencies that don’t have large, in-house security teams.
The service provider handles all the heavy lifting:
- 24/7 Monitoring: Cyberattacks don’t work 9-to-5. A managed service ensures constant vigilance, with analysts watching over your systems around the clock, on weekends, and during holidays.
- Expert Threat Analysis: The service is backed by a team of cybersecurity professionals. It’s their job to sift through all the data, investigate alerts, and decide which ones represent real threats that need immediate action.
- Proactive Threat Hunting: Instead of just waiting for an alarm to go off, these experts actively hunt for signs of hidden intruders or unusual behaviour that might signal an impending attack.
- Rapid Incident Response: When a genuine threat is found, the managed team acts instantly to contain it. They can isolate compromised devices from the network to stop an attack from spreading and then guide you through fixing the issue.
In short, managed EDR combines the best of both worlds: technology and human intelligence. This blended approach is often part of a much broader security strategy. To see how it fits into the bigger picture, you can learn more about Managed Detection and Response (MDR) services, which often include EDR as a core element.
Ultimately, this model delivers enterprise-level security without the immense cost and hassle of building your own security operations centre from scratch. It’s an ideal solution for any business that needs to protect its valuable data and client work.
Understanding The Core Components of EDR
To really get why managed EDR is such a game-changer, you have to look under the bonnet. It’s not just one piece of software; it’s a combination of powerful, interconnected processes, all steered by human experts. Each part has a specific job to do, working together to build a robust defensive shield around your business’s most critical assets.
Think of it like a high-end home security system. You don’t just have a single alarm on the door. You’ve got motion sensors, cameras, reinforced locks, and a team at a monitoring station ready to act the moment something’s amiss. A managed EDR service works on the same principle, layering different functions to provide deep protection for every device on your network.
These functions work in harmony, moving from simply collecting data to taking decisive, informed action against threats. It’s this integrated approach that ensures nothing slips through the cracks, from the smallest anomaly to a full-blown cyberattack.
Continuous Endpoint Monitoring
The foundation of any EDR solution is continuous endpoint monitoring. This is the data collection engine, acting as a constant surveillance system for every single laptop, server, and workstation connected to your network. Lightweight software agents are installed on these devices, and they meticulously record everything that happens.
This isn't your old-school antivirus scan looking for known viruses. These agents capture a rich stream of what we call telemetry data, including:
- Process Execution: What programs and services are running?
- File System Changes: Which files are being created, modified, or deleted?
- Network Connections: What is each device communicating with, both inside your network and out on the internet?
- User Activity: Who is logging in, and what are they doing?
This constant flow of information provides the raw material needed for smart analysis, creating a complete and detailed picture of your IT environment’s health.
AI-Driven Threat Detection
All that data would be completely overwhelming without a smart way to make sense of it. This is where AI-driven threat detection comes in. The managed service uses sophisticated algorithms to sift through the billions of data points collected by the endpoint agents, hunting for patterns of suspicious behaviour.
This is what sets it apart from traditional antivirus software, which just relies on matching threats to a list of known malware signatures. EDR’s behavioural analysis can spot brand-new threats and advanced attack techniques that have never been seen before.
A managed EDR service doesn’t just ask, "Have I seen this specific threat before?" It asks, "Is this behaviour normal for this device and this user?" This shift from signature-based detection to behavioural analysis is key to stopping modern, sophisticated attacks.
Proactive Threat Hunting
While the automated detection is incredibly powerful, it’s backed by a crucial human element: proactive threat hunting. Instead of just waiting for an automated alert to pop up, the provider's team of security analysts actively searches through your data for hidden intruders or subtle signs of compromise.
These experts are trained to think like attackers. They form hypotheses about how an intruder might try to get a foothold and then comb through endpoint data to find evidence. This human-led hunting can uncover stealthy threats designed to evade automated systems, providing an absolutely essential layer of defence.
Incident Response and Remediation
Finding a threat is only half the battle. The final, and arguably most critical, component is incident response and remediation. As soon as a threat is confirmed, the managed security team acts immediately to contain and eliminate it.
Their response actions can include:
- Isolating the Endpoint: The compromised device is instantly quarantined from the network to stop the threat from spreading to other systems.
- Terminating Malicious Processes: The team remotely stops any malicious programs in their tracks.
- Removing Malware: Any malicious files or persistence mechanisms are scrubbed from the system.
- Providing Remediation Guidance: You receive a clear, straightforward report on what happened, how it was stopped, and what steps you can take to prevent it from happening again.
This rapid, expert-led response minimises damage and gets your business back on its feet quickly. The huge value offered by these comprehensive services is driving massive market growth. The global managed detection and response (MDR) sector, which includes managed EDR, was valued at around $3.47 billion and is projected to more than double to $7.27 billion, showing just how much businesses are coming to rely on these expert services. You can discover more about the MDR market's rapid expansion here.
Key Benefits for Modern UK Businesses
So, you understand the nuts and bolts of managed endpoint detection and response. That's a great start, but the real magic happens when you connect those features to what actually matters for your business. For modern UK companies, especially those in the thick of fast-paced creative industries, the benefits go way beyond just stopping viruses. It's about building genuine resilience, letting your team focus, and keeping your operations both secure and above board.
One of the biggest wins is immediate access to an elite cybersecurity team without the eye-watering cost of hiring one yourself. Finding, training, and keeping a full-time, in-house security operations centre is a massive financial and logistical headache. A managed service plugs you into that top-tier expertise from day one for a predictable monthly cost, levelling the playing field against bigger competitors.
This instantly takes the pressure off your internal IT team. Instead of getting swamped by a never-ending flood of security alerts and spending their days chasing ghosts, they can get back to projects that actually drive growth. It's a fundamental shift that turns your tech from a defensive chore into a strategic advantage—a critical edge for any agency that needs to stay innovative. For a closer look at this, our guide on the benefits of MSPs for creative businesses digs into this dynamic.
Supercharging Your Defences
At its core, a managed EDR service is all about shrinking the gap between a threat being spotted and being shut down. In cybersecurity, speed is everything. An attack that’s left to fester for hours or days can do exponentially more damage than one that’s contained in minutes.
This is where the difference between an in-house effort and an expert-led service really shows.
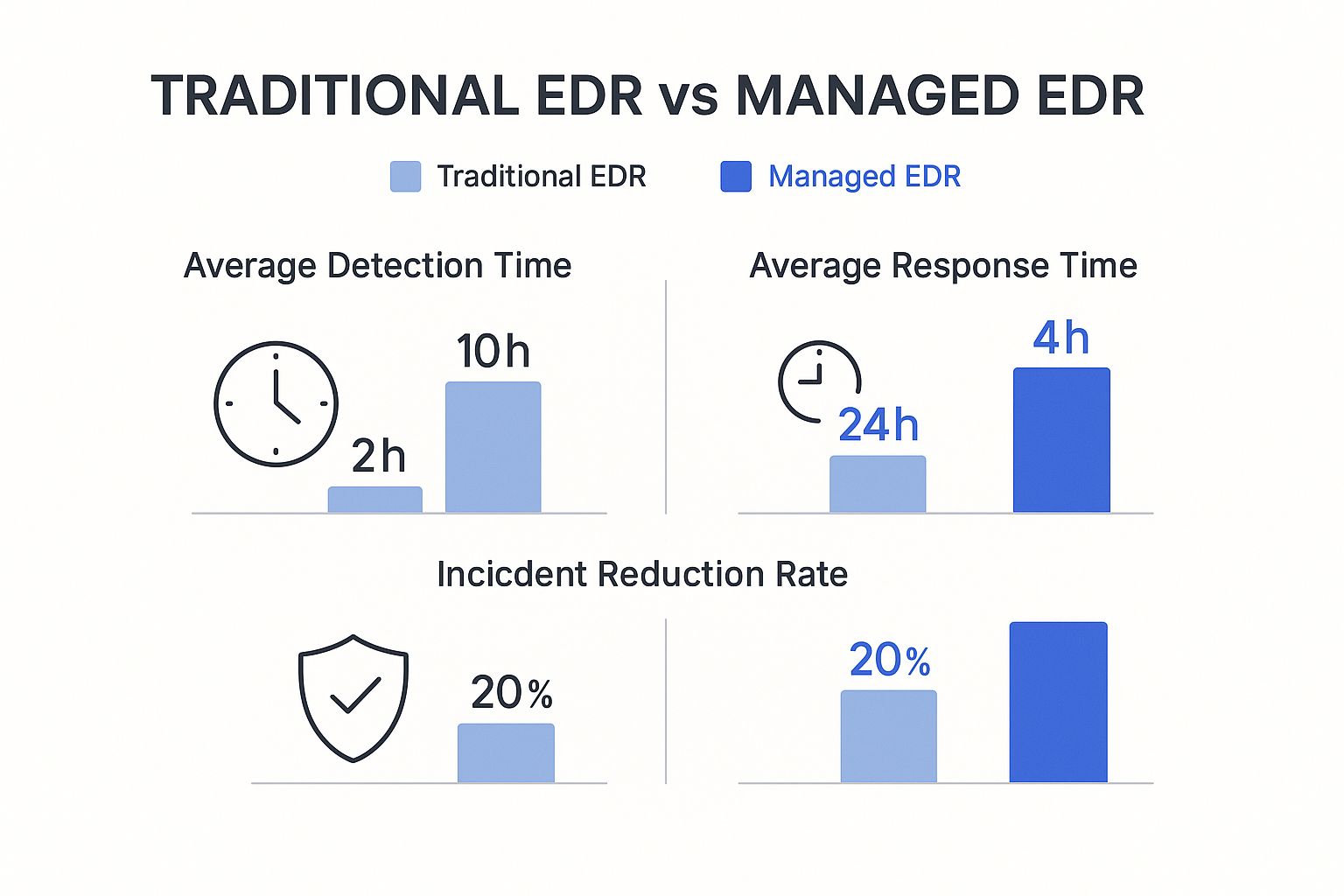
As you can see, a managed service isn't just faster; it dramatically cuts down the number of incidents that succeed in the first place. That rapid containment is absolutely vital for protecting your finances and the reputation you've worked so hard to build.
Nailing Strict UK Compliance Demands
For any UK business that handles client or employee data, regulations like the General Data Protection Regulation (GDPR) aren't optional. A single breach can lead to ruinous fines and a public relations nightmare. Managed EDR provides the robust, documented security measures you need to satisfy these stringent requirements.
A managed EDR service acts as a detailed, always-on security logbook for your entire organisation. It provides the concrete evidence of continuous monitoring, threat detection, and incident response that auditors and regulators demand, demonstrating due diligence in protecting sensitive data.
This isn't just about dodging penalties; it's about building trust. It shows clients you're serious about protecting their data, which can be a powerful selling point in a crowded market. The detailed reports and clear audit trails are exactly what you need to prove compliance and keep client confidence high.
This proactive approach is becoming the standard. In fact, larger organisations accounted for about 65% of the global EDR market share. We're seeing this trend across the UK's financial, governmental, and telecom sectors, where these services are relied upon to guard complex systems and high-value data.
To see how the market is shifting, it’s worth a look at the landscape in more detail. Many providers offer in-depth research to help businesses understand these trends.
Keeping the Business Running
Ultimately, all these benefits feed into one critical goal: business continuity. A successful cyberattack can bring your operations to a screeching halt, causing expensive downtime and derailing crucial projects. By proactively hunting for threats and swiftly containing any that get through, a managed EDR service helps ensure your business can weather an attack without major disruption.
This gives you invaluable peace of mind, freeing you and your team to focus on what you do best—delivering brilliant creative work for your clients. It turns cybersecurity from a source of constant anxiety into a quiet, dependable foundation for your business's success.
How to Choose the Right Managed EDR Provider

Choosing a partner to handle your cybersecurity is one of the most critical decisions you'll make. The right provider becomes a seamless extension of your team, quietly neutralising threats in the background. The wrong one? That leads to missed alerts, slow responses, and a false sense of security that puts your client work and reputation on the line.
This isn't just about picking the best tech; it's about trusting a team of experts with the digital wellbeing of your entire business. To make a confident choice, you need to look past the marketing slogans and dig into the specifics of how a provider actually operates. It all comes down to evaluating the people, processes, and technology behind their managed endpoint detection and response service.
Evaluate Their Security Operations Centre
The heart of any managed EDR service is its Security Operations Centre (SOC). This is the command centre where expert analysts watch over your systems for threats. But not all SOCs are created equal.
Your first question should be about their hours. Cyber threats don't keep a 9-to-5 schedule, so your protection shouldn't either. You need to know if their SOC offers true 24/7/365 coverage. Ask them directly: are analysts actively monitoring systems around the clock, or do they just have an on-call system for after-hours emergencies? There's a huge difference.
Next, get to know the people.
- Analyst Credentials: What certifications and experience do their security analysts hold? You want to see credentials like GIAC, CREST, or CISSP, which prove a high level of expertise.
- Team Structure: Is the team big enough to give you dedicated attention without being stretched too thin? A low analyst-to-client ratio means your business won't just be another number in a queue.
- Direct Access: Can you speak directly to an analyst when you have a question, or are you stuck navigating layers of customer support first? Direct communication is vital, especially during a security incident.
A strong SOC is staffed by qualified experts who are always watching, ready to act on your behalf.
Scrutinise the Service Level Agreements
A Service Level Agreement (SLA) is more than just a piece of paper; it's the provider's contractual promise to you. This is where you find their guaranteed response times, and you need to look at these details closely. Vague promises like "rapid response" just aren't good enough.
An SLA must contain specific, measurable commitments. Look for clearly defined metrics like 'Time to Detect' (TTD) and 'Time to Respond' (TTR). These tell you exactly how quickly the provider guarantees they will identify a threat and start taking action to contain it.
A solid SLA sets clear expectations and holds the provider accountable. If these metrics aren't spelled out, it’s a major red flag. You need to know that if an attack hits at 2 AM on a Sunday, there’s a clear, contractually obligated timeline for a response. For a wider view on this, exploring the key things to consider when hiring an MSP can offer some valuable parallel insights.
Assess Their Technology and Integration
While the human expertise is key, the technology they use is just as important. An effective managed EDR service depends on a powerful platform to gather data and enable swift action. Ask them what EDR platform they use and, more importantly, why they chose it. A good provider should be able to explain the specific advantages of their tools.
Even more crucial is how their technology will integrate with your existing systems. Will it play nicely with your current network, cloud services, and other security tools? A provider that creates integration headaches or forces you to completely overhaul your setup can cause more problems than it solves. You need a seamless fit to create a unified security posture without disrupting your business.
Finally, look for a partner who understands your world. A provider with experience protecting other creative businesses in the UK will already know the unique threats you face and the specific demands of regulations like GDPR. They'll speak your language and get that protecting your intellectual property and client data is everything. This industry-specific expertise ensures the protection you get isn't just generic, but genuinely right for your business.
Implementing Managed EDR in Your Organisation
The thought of bringing in a new security service can seem daunting, conjuring images of disruption and complex technical projects. But getting a managed endpoint detection and response (EDR) service on board is a structured, collaborative journey, not a technical overhaul. It’s designed from the ground up to be a partnership with minimal friction and maximum value, right from day one.
Instead of upending your current operations, think of it as methodically adding a new, powerful layer of protection. A good provider will walk you through every step, ensuring you know exactly what’s happening and why. They turn what seems complex into a straightforward, manageable experience.
The Initial Discovery and Scoping
It all starts with a conversation. The first step is usually a discovery call where the provider’s team gets to know your business. This isn't a sales pitch; it's a fact-finding mission to understand your specific needs, your current IT setup, and what you need to protect most.
They’ll want to know about:
- Your Environment: How many endpoints—laptops, servers—do you have? Are your teams in the office, remote, or hybrid?
- Your Data: What kind of sensitive data are you working with? This could be client intellectual property, employee information, or financial records.
- Your Concerns: What are your biggest security worries? Are you trying to prevent ransomware, stop data breaches, or meet compliance rules?
This initial scoping is crucial. It makes sure the service is tailored to your unique operational needs, so there’s no guesswork later on.
Seamless Agent Deployment
Once the scope is agreed, the next phase is deploying lightweight software agents to your endpoints. This is the part that often worries business owners, but modern deployment methods make it surprisingly smooth. The agents are designed to be completely unobtrusive, using minimal system resources so your team won't even notice they're there.
Deployment can usually be handled remotely and automated across all your devices, often taking just a few days to roll out. This lays the technical foundation, giving the provider’s Security Operations Centre (SOC) the visibility it needs to start protecting your business.
The most crucial phase after deployment is the 'tuning' period. This is where the security team calibrates the system to understand what 'normal' looks like for your business. This intelligent fine-tuning is what separates a great managed service from a noisy one, drastically reducing false alarms.
Fine-Tuning and Establishing Communication
During this tuning phase, the system learns the rhythm of your organisation. It identifies your standard software, typical network patterns, and normal user behaviours. By setting this baseline, the SOC analysts can more accurately spot the genuine anomalies that could signal a threat.
Throughout this process and beyond, clear communication is everything. Your provider will set up dedicated contacts and define how they’ll alert you to an incident. This ensures that when a real threat is found and contained, you get clear, actionable information without any delay. The entire implementation is a partnership built on transparency, turning a complex security upgrade into a simple, reassuring process.
The Future of Endpoint Security and XDR
Cybersecurity never stands still, and your strategy can't afford to, either. The world of managed endpoint detection and response is constantly evolving, driven by attackers who are always looking for a new way to slip past your defences. The future isn't just about spotting attacks; it's about predicting and stopping them before they even get started.
This forward momentum is being powered by artificial intelligence. AI is moving way beyond just flagging suspicious files. The next generation of security services will use predictive analytics to spot potential vulnerabilities and weak points in your defences, letting your managed provider reinforce them proactively. Instead of just reacting to threats, security is becoming predictive.
The Rise of Extended Detection and Response
As powerful as EDR is, it’s laser-focused on one part of your IT world: the endpoints. But modern businesses, especially creative ones, are complex ecosystems. A threat could start from your network, a cloud app, or an email account. This is exactly why the industry is moving towards Extended Detection and Response (XDR).
Think of it like this: if EDR is a highly skilled security guard assigned to every single device, XDR is the central command centre that sees everything happening across your entire digital estate. It pulls together security data from multiple sources:
- Endpoints: Laptops, servers, and mobile devices.
- Networks: Analysing traffic for unusual patterns.
- Cloud Infrastructure: Monitoring services like AWS or Microsoft 365.
- Email Systems: Catching phishing attempts and malicious attachments.
By pulling together information from all these places, XDR gives you a single, unified view of a potential attack. It connects the dots between a dodgy email, an unusual login to a cloud service, and a strange process running on a laptop—something that individual tools, working in isolation, would almost certainly miss.
XDR breaks down the silos between different security tools. It recognises that an attack is rarely a single event but a chain of activities, and provides the visibility needed to see and stop the entire chain.
Choosing a Forward-Thinking Partner
This shift towards integrated, intelligent security really highlights how important it is to choose a provider who is looking ahead. A partner committed to XDR and predictive AI can protect you not just from the threats we see today, but from the emerging attacks of tomorrow.
Ultimately, this ensures your business stays resilient and secure in the long term, letting you focus on your creative work with genuine confidence.
Got Questions? Let’s Clear Things Up
Even after getting a good handle on managed endpoint detection and response, it’s natural to have a few questions rattling around. We get it. Let’s tackle some of the most common ones we hear from creative businesses trying to figure out if this is the right move for them.
What’s the Real Difference Between EDR and MDR?
This one trips a lot of people up, but the distinction is actually quite simple.
Think of it like a high-performance race car:
- Endpoint Detection and Response (EDR) is the technology itself. It’s the powerful, sophisticated engine packed with sensors and diagnostics that monitors every part of the car, spots problems, and gives you the tools to fix them.
- Managed Detection and Response (MDR) is the human-led service. This is your expert pit crew and driver, working 24/7. They use the EDR engine (and other tools) to keep the car running at peak performance, spot trouble before it happens, and react instantly during a race.
When you bring on a managed EDR service, you’re getting the best of both worlds: the advanced technology and the dedicated team of experts to run it for you. That combination is what keeps you safely on the track.
Is Managed EDR a Good Fit for a Small Studio or Agency?
Yes, without a doubt. In fact, it's often the perfect solution. Cybercriminals love targeting smaller businesses precisely because they assume their defences are weaker. Most growing creative agencies can't justify the cost of an in-house, round-the-clock security team, which leaves a dangerous gap.
A managed EDR service completely levels the playing field. It gives small and medium-sized businesses access to the same calibre of protection that, until recently, was only affordable for huge corporations. You get enterprise-grade security for a predictable, manageable cost.
For a growing agency protecting high-value client work and sensitive data, this is a game-changer. It takes the security burden off your shoulders without needing a massive internal team.
What Does a Managed EDR Service Typically Cost?
The pricing for managed EDR is usually refreshingly straightforward. It’s almost always based on a simple metric: the number of endpoints (laptops, desktops, servers) you need to protect. Most providers charge on a per-device, per-month basis, which makes it an easy operational expense to budget for.
Of course, prices can vary. The final cost often depends on the specific services bundled in. Factors like how much proactive threat hunting is included, the scope of the incident response actions, and whether you need advanced reporting for compliance can all influence the monthly fee.
How Long Does It Take to Get It Up and Running?
Deployment is much faster and less disruptive than most people think. Once we’ve done an initial discovery session to understand your setup, rolling out the small, lightweight software agent to your devices is a quick job—often done within just a few days.
After that initial rollout comes the most important part: the "tuning" period. This might take a couple of weeks. During this time, the security team is essentially teaching the system what "normal" looks like for your business. This calibration is crucial for stamping out false alarms and making sure that when an alert does pop up, it’s genuine.
Ready to secure your creative business with expert, human-led IT and cybersecurity? InfraZen Ltd specialises in helping agencies and studios work securely and efficiently, without interruption. Discover how we can bring calm, robust protection to your team.

