When you hear "security operations," it's easy to picture a dark room full of screens, just waiting for a red alert to flash. But in reality, it's about the strategic coordination of people, processes, and technology to keep your organisation’s information systems safe.
It involves non-stop monitoring, spotting threats, and responding to incidents to protect your most critical assets from cyberattacks. A truly effective approach isn't about just fixing things after they break; it's about building a proactive security posture from the ground up.
Understanding Your Security Operations Framework

Security operations, or SecOps, is the central nervous system of your entire cybersecurity strategy. It’s far more than just buying the latest software. Think of it as a continuous cycle: identifying, protecting, detecting, responding to, and recovering from security threats.
For creative teams, this means safeguarding everything from sensitive client data and intellectual property to the project files that are the very lifeblood of your business. A solid SecOps framework is built on three pillars that have to work together. If you neglect one, the whole structure becomes wobbly, like a three-legged stool with a missing leg.
The Three Pillars of SecOps
To get this right, you need to bring three core elements into balance. Understanding what each one does is the first step toward building a cohesive and resilient defence against modern cyber threats.
Let's break down the essential components that form a successful SecOps framework. Each pillar plays a distinct but interconnected role in protecting your operations.
| Pillar | Primary Role | Key Activities |
|---|---|---|
| People | The Human Defence Layer | Security awareness, incident analysis, protocol adherence, skill development. |
| Processes | The Operational Rulebook | Incident response plans, vulnerability management workflows, compliance checks. |
| Technology | The Automated Guard | SIEM systems, Endpoint Detection & Response (EDR), firewalls, threat intelligence platforms. |
Getting these three pillars to work in harmony is the secret to a strong security posture that can adapt to new challenges.
The Core Functions That Make It All Work
So, what does a security team actually do day-to-day? Effective SecOps involves several key functions that work together to keep the organisation protected.
-
Continuous Monitoring: This is about actively watching networks, servers, and endpoints for anything that looks suspicious. It's not a passive, set-and-forget task- it requires constant vigilance to spot anomalies that could be the first sign of an attack.
-
Vulnerability Management: You can't just hope for the best. This means regularly finding, assessing, and patching weaknesses in your systems. It’s a proactive step that closes security gaps before attackers can find and exploit them.
-
Threat Intelligence: It helps to know what the other side is planning. This function involves gathering and analysing information about current and emerging threats, allowing your team to anticipate attacker tactics and strengthen your defences before they even try.
-
Governance and Compliance: This is where security meets the business. It’s all about making sure your security practices align with your business goals and any regulatory requirements you have to meet. Having a clear structure is key, and you can learn more about how to establish one by exploring different types of an https://infrazen.tech/it-governance-framework/. This ensures security decisions support the wider business while keeping you on the right side of the law.
Getting Ahead of Threats with Better Detection and Analysis
Moving beyond basic security isn't just about patching holes; it's about shifting your entire mindset from reactive to proactive. Real threat detection isn't about waiting for an alarm to go off. It's about spotting the breadcrumbs an attacker leaves before they can do any real damage.
This means setting up monitoring and detection systems that give you a clear, honest view across your whole operation. For a creative team, that includes everything- from a designer’s high-spec workstation and the local project server to the cloud bucket holding sensitive client proofs.
The goal here is simple: spot weird activity, figure out what it is, and shut it down fast. A proactive stance is the only way to manage security effectively today.
Choosing the Right Tools for the Job
Your ability to spot threats is only as good as the tools you're using. In any modern security team's toolkit, two pieces of tech are absolutely essential: Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR).
Think of a SIEM system as your central command centre. It pulls in log data from everywhere- servers, apps, firewalls, you name it- and pieces it all together. It's like having hundreds of separate security camera feeds piped into a single, intelligent monitoring station that can connect the dots and flag suspicious patterns.
On the other hand, an EDR solution is your ground-level protection, focusing on individual devices like laptops and servers (what we call "endpoints"). It gives you deep visibility into what’s happening on these machines, letting you catch threats like malware or unauthorised access that would otherwise fly under the radar. You can get a better sense of how this works in practice by exploring what’s involved with managed endpoint detection and response.
The key is to pick tools that deliver clarity, not just more data. A good system should help you find the signal in the noise, turning a million tiny events into a handful of alerts your team can actually act on.
Taming the Beast of Alert Fatigue
One of the biggest problems in security operations is alert fatigue. It’s a real killer. When your team is hammered with hundreds of low-priority or false-positive alerts every day, they start to tune them out. That’s when a genuine, critical threat gets missed.
The fix is to fine-tune your detection rules. Don't just accept the out-of-the-box settings; customise them for how your team actually works.
-
Establish a Baseline: First, you need to know what "normal" looks like. When do your designers typically access huge video files? What external servers do they connect to for stock assets? Knowing this helps you build rules that only fire when something is genuinely out of place.
-
Prioritise Your Alerts: Not all alerts are equal. A failed login attempt is one thing; malware executing on your main file server is a five-alarm fire. Your system needs to be configured to assign risk scores so your team knows exactly what to tackle first.
-
Automate the Small Stuff: Use automation to handle the common, low-risk alerts. For example, an automated playbook could check a suspicious IP address against a threat list or temporarily block it without anyone needing to lift a finger. This frees up your human experts for the complex investigations that really need their attention.
Connecting the Dots to Uncover Attacks
Sophisticated attacks are rarely a single, loud bang. They're usually a series of small, quiet steps that build up over time. An attacker might get a foothold with a phishing email, move silently across the network to find valuable data, and then try to sneak it out.
Effective analysis is all about connecting these seemingly unrelated dots. This is where your SIEM and EDR tools prove their worth, as they can correlate events happening on completely different systems.
You might see a pattern like this:
- An unusual login from a new location.
- Followed by access to a sensitive project folder.
- Then a large amount of data being sent to an unknown external address.
Taken individually, each event might not raise a major alarm. But put them together, and you have a clear picture of a potential data breach.
This kind of analytical detective work is at the heart of modern security, and it's more critical than ever. Recent research shows the UK is now the third most targeted country for malware, with over 100 million attacks logged in just three months. This sharp increase highlights just how essential proactive and intelligent threat analysis has become.
Crafting a Battle-Tested Incident Response Plan
Let's be realistic: a security incident isn't a matter of if, but when. Being unprepared for one, however, is a choice you don't have to make. Truly effective managing security operations means having a clear, calm, and repeatable process ready to go when things inevitably go wrong. An incident response (IR) plan is your playbook for minimising damage, getting services back online quickly, and keeping client trust intact.
A smart first move is to develop a robust and clear an incident response policy. This document sets the ground rules and guiding principles for your team, ensuring everyone is on the same page before you dive into the specifics of who does what.
This flow chart breaks down the core stages of a typical response, moving from detection all the way through to containment and learning.
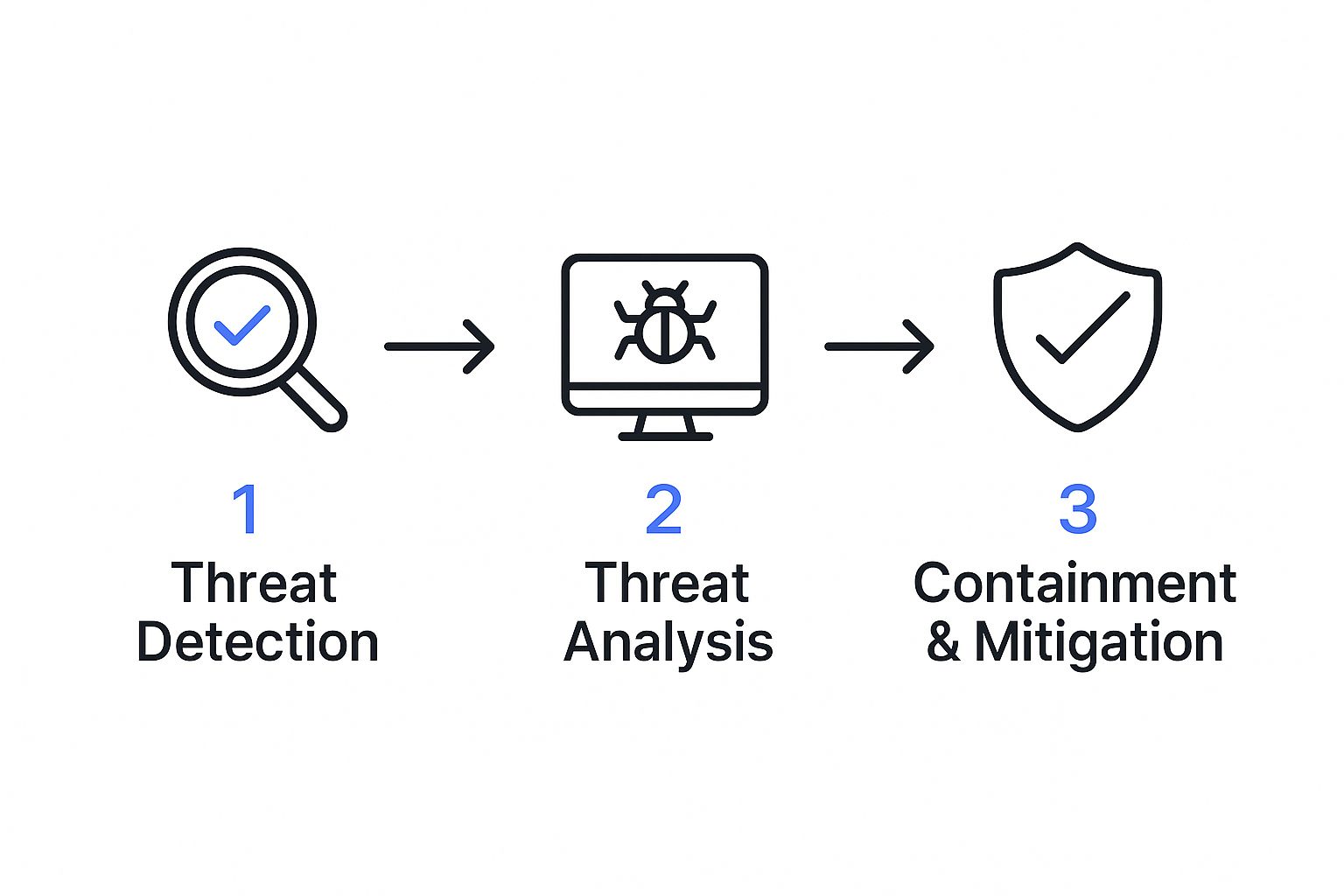
As you can see, a successful response is a structured journey, not a panic-driven scramble. It’s about moving logically from awareness to action.
Defining Roles and Responsibilities
When a breach hits, the last thing you need is confusion over who’s in charge of what. Clearly defined roles are the bedrock of a fast, effective response. You don't need a massive dedicated team, either. For smaller creative agencies, it’s perfectly fine for individuals to wear multiple hats.
The key is absolute clarity. Who is the Incident Commander with the final say? Who’s responsible for the technical heavy lifting, and who’s handling the delicate task of communicating with clients?
- Incident Commander: The single point of contact who directs the entire response, makes the tough calls, and delegates tasks.
- Technical Lead: The hands-on expert responsible for identifying, containing, and booting the threat from your systems.
- Communications Lead: The person managing all internal and external messaging, making sure the story is consistent and transparent.
- Legal/Compliance Advisor: Pulled in to ensure every action complies with regulations, like data breach notification laws.
Get these roles documented, assign a primary and a backup for each, and make sure everyone knows exactly what's expected of them. This simple step can single-handedly prevent chaos.
The Six Phases of Incident Response
A proper IR plan isn’t just a document; it’s a lifecycle. Breaking the process down into these six phases makes it far more manageable, especially when stress levels are high.
- Preparation: This is all the work you do before an incident. It’s about creating the plan, defining those roles, getting the right tools in place, and running drills with your team.
- Identification: This phase kicks off the moment a monitoring tool or a team member spots something fishy. The goal here is to quickly verify if it's a real incident and figure out how big the problem is.
- Containment: Once you’ve confirmed an incident, the immediate priority is to stop it from spreading. This might mean yanking an infected laptop off the network or temporarily disabling a compromised cloud account.
- Eradication: With the threat contained, you have to remove it completely. This means deleting malware, disabling breached user accounts, and patching the vulnerabilities the attackers exploited.
- Recovery: Now it's time to get back to normal. This involves restoring data from clean backups and double-checking that all systems are fully functional and secure. This phase is closely tied to your business continuity plans; having a solid blueprint is essential. You can find some excellent guidance in this disaster recovery plan IT template.
- Lessons Learned: After the dust settles, it's time for a post-mortem. What went well? What was a disaster? Use these findings to update your plan and strengthen your defences for next time.
A common mistake is skipping the "Lessons Learned" phase in the rush to get back to business. This is where you gain the most value, turning a negative event into a powerful opportunity to get better.
This structured approach is vital. In 2024, around 43% of UK businesses reported a cyber breach or attack. While that’s a slight improvement, the fact that phishing and ransomware are still the dominant threats shows just how important a well-rehearsed plan is. A prepared team is a resilient one.
Using Automation to Strengthen SecOps

Manual security checks just can't keep up with the speed and scale of modern threats. For a creative team already pushing to meet deadlines, every minute spent on repetitive security tasks is a minute lost from billable work. This is exactly where intelligent automation becomes your best friend in managing security operations.
The goal isn’t to replace your people, but to supercharge them. By offloading the tedious, high-volume work to machines, your security analysts are free to focus on what they do best: complex problem-solving, strategic thinking, and hunting down sophisticated threats.
Introducing SOAR for Smarter Responses
A game-changer in this space is Security Orchestration, Automation, and Response (SOAR). Think of a SOAR platform as a smart conductor for your security team. It connects all your different security tools- your SIEM, endpoint protection, firewalls- and gets them talking to each other, acting in a coordinated way.
SOAR platforms use pre-defined instructions called playbooks to automate entire workflows. When a specific type of alert fires, the system can kick off a playbook that handles all the initial grunt work automatically, often in a matter of seconds.
Practical Automation Playbooks in Action
That’s the theory, but what does it look like in the real world? Let’s take two common headaches for creative agencies and see how automation flips the script on the response.
Example 1: A Phishing Email Investigation
A designer flags a dodgy email with an unusual link. The old-school manual approach would involve an analyst:
- Checking the sender’s reputation.
- Analysing the email headers for signs of spoofing.
- Detonating the link in a safe sandbox environment to see where it goes.
- Scanning any attachments for malware.
- Searching everyone’s inboxes to see who else got the email.
An automated SOAR playbook does all of this in under a minute. The system then hands a neat summary to the analyst, who just needs to make the final call: block the sender, nuke the email from all inboxes, and create a new detection rule. A 20-minute task just became a 2-minute review.
The real power of automation lies in its consistency and speed. A playbook executes the exact same steps, perfectly, every single time. It doesn't get tired, it doesn't get distracted, and it doesn't skip a step because it's the end of the day.
Example 2: A Malware Alert on a Workstation
Your endpoint detection and response (EDR) tool flags a malicious process on a video editor’s machine.
- Automated Action: The SOAR playbook instantly isolates the workstation from the network. This stops any potential malware dead in its tracks, preventing it from spreading.
- Automated Investigation: It then queries the EDR for more details, checks the file hash against threat intelligence databases, and pulls the machine’s process history for context.
- Analyst Decision: The analyst gets a clear report and can confirm if it's a genuine threat. If it is, they can trigger the next stage of the playbook- wiping and reimaging the machine- with a single click.
The Growing Role of AI in SecOps
While rule-based automation is brilliant for dealing with known threats, artificial intelligence (AI) takes things to another level. AI and machine learning models can sift through enormous amounts of data to spot unusual behaviour that fixed rules would completely miss.
AI is fantastic at figuring out what "normal" looks like for each user and device. It learns that your lead designer often works late but almost never touches financial folders. So, if that account suddenly tries to download a bunch of client invoices at 3 a.m., an AI-driven system will flag it as a high-risk anomaly, even if valid credentials were used. This is a massive help for spotting insider threats or compromised accounts.
AI's ability to process and correlate data is also changing business processes far beyond security. To get a sense of its wider impact, you can find great insights on how robotic process automation and artificial intelligence are revolutionising business processes.
As we look ahead, exploring the role of AI in future operations offers a glimpse into how these technologies will continue to enhance security. The key is to start small. Pinpoint your most repetitive, time-sucking tasks and automate those first. This practical approach delivers quick wins and builds momentum towards a much more efficient and resilient security operation.
Measuring SecOps Performance for Continuous Improvement
Effective security operations don't just happen; they're built, tested, and refined over time. You can't improve what you don't measure, which is why getting a handle on performance is fundamental to running a tight ship. This isn't about chasing vanity metrics like the raw number of alerts you’ve blocked- it’s about understanding how fast, efficient, and effective your team really is when a threat appears.
To do this, we need to focus on key performance indicators (KPIs) that tell a meaningful story about your security posture. The right metrics help you spot weaknesses, justify new investments, and show tangible progress to leadership.
Key Metrics That Actually Matter
It’s easy to drown in security data, but finding real insight is another story. Instead of tracking dozens of metrics, it’s far better to concentrate on a few that directly reflect your team's ability to handle a real-world threat. Two of the most critical are Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
-
Mean Time to Detect (MTTD): This is the clock that starts the moment a security incident begins and stops the second your team spots it. A low MTTD means your monitoring and detection tools are properly tuned, and your team is quick to pick up on anomalies.
-
Mean Time to Respond (MTTR): Once you’ve spotted an incident, how long does it take your team to contain and neutralise the threat? That's your MTTR. A low MTTR shows your incident response plan is working and your team can act decisively under pressure.
These two metrics alone give you a powerful snapshot of your operational readiness. They shift the focus from simply counting alerts to measuring the speed and efficiency of your response.
The goal isn't just to build a wall- it's to shrink the window of opportunity for attackers. A low MTTD and MTTR mean that even if a threat gets through, its potential for damage is drastically reduced.
Reporting That Resonates with Everyone
How you present your findings is just as important as the data itself. A deep technical report full of jargon is perfect for your SecOps team, but it won’t land with the C-suite. You have to tailor your reports to the audience.
For Technical Teams:
These reports need to be granular. Zero in on metrics like alert triage accuracy, playbook execution times, and false positive rates. The whole point here is to find operational bottlenecks and figure out where you can fine-tune your tools and processes.
For Executive Leadership:
Translate the technical metrics into business impact. Instead of talking about MTTR in seconds, frame it as "reducing our risk exposure from hours down to just a few minutes." Use clean visuals to show trends over time and connect your security performance to bigger business goals, like protecting revenue and client trust.
Fostering a Culture of Improvement
Measurement is just the starting line. The real value comes from using that data to get better, day in and day out. This really comes down to two crucial practices: post-incident reviews and regular audits.
After any significant security incident, it's vital to hold a blame-free post-incident review. The focus should always be on the process, not the people. What worked? What didn't? How can we update our playbooks or tools to be faster and more effective next time?
Regular audits, whether they’re internal or from a third party, provide a fresh pair of eyes. They can help identify weaknesses you’ve become blind to and ensure your strategies are still aligned with current threats. This continuous feedback loop- measure, analyse, adapt- is the engine that drives a mature and resilient security operation.
Your Questions About Managing Security Operations, Answered
Even with the best framework in place, questions are bound to pop up. Let’s tackle some of the most common ones we hear from organisations trying to build or improve their security programmes, with straightforward answers you can actually use.
What's the Biggest Hurdle When Starting a SecOps Programme?
Honestly, it’s almost always getting the green light- and the budget- from leadership. The trick is to stop talking like a techie and start talking like a business leader. Forget discussing vulnerabilities; instead, explain the real-world financial loss or operational chaos a breach could cause.
The other major headache is the skills gap. You can get around this by training up your existing team, using smart automation to handle the repetitive tasks, or bringing in a managed security service provider (MSSP) to fill in the gaps.
Securing a budget is less about fear and more about business sense. Present security not as a cost centre, but as an investment in business continuity and client trust. When you frame it that way, the conversation changes completely.
How Can a Small Business Handle SecOps on a Shoestring Budget?
For small businesses, it’s all about prioritisation. You need to focus on the fundamentals that give you the biggest bang for your buck.
- Implement Multi-Factor Authentication (MFA): Slap it on everything you can- email, cloud services, and any internal tools. It’s one of the single most effective defences you can have.
- Run Security Awareness Training: Teach your team how to spot phishing emails. It sounds simple, but this is still the number one way attackers get in.
- Patch Everything, Promptly: Make sure all your systems and software are kept up-to-date. This closes the known security holes before anyone can exploit them.
You can also lean on open-source security tools and make the most of the security features already built into your cloud services. And critically, have a simple but clear incident response plan written down so you know exactly who to call and what to do when something goes wrong.
How Often Should We Test Our Incident Response Plan?
A good rule of thumb is to run tabletop exercises at least twice a year, with a more in-depth simulation annually. A tabletop exercise is just a fancy way of saying you get the key people in a room and talk through a crisis, like a ransomware attack. It’s a low-stakes way to find the holes in your plan without actually disrupting the business.
Of course, this isn't set in stone. If your organisation goes through big changes- like launching a new critical system or seeing a new type of threat become common- it’s smart to run a test to make sure your plan still holds up.
The demand for people with these skills is absolutely soaring. In the UK, the cyber security sector employed an estimated 67,299 full-time professionals in 2025, which was an 11% jump from the year before. It just goes to show how critical these roles have become as threats get more complex. You can dig deeper into the UK's sectoral growth and workforce trends in the Cyber Security Sectoral Analysis 2025.
Trying to get a handle on security operations can feel overwhelming, but you don't have to figure it all out alone. InfraZen Ltd provides strategic IT management and cybersecurity designed specifically for creative teams, helping you protect your work so you can stay focused on what you do best.
Find out how we can bring a sense of calm and reliability to your technology by visiting https://infrazen.tech.

