When we talk about secure file sharing in a business context, we’re really talking about a system for exchanging digital files that keeps them safe from prying eyes. For a creative agency, this is non-negotiable. It means using platforms with end-to-end encryption and tight control over who sees what, so you can protect client IP, sensitive project files, and financial records from a potential data breach.
Building Your Secure Sharing Framework

Before you even think about choosing software, you need a solid foundation. I’ve seen it time and again: a business jumps straight to a tech solution without understanding what they actually need. It almost always ends in one of two ways- they get a system that overcomplicates everyone's workflow, or one that doesn't provide nearly enough protection.
A well-defined framework ensures the technology serves you, not the other way around.
This initial planning stage is all about asking the right questions. What are we trying to protect? Who needs access, and when? What are our biggest risks right now? Answering these honestly gives you a blueprint for a system that balances robust security with the fluid, collaborative nature of creative work.
Identify Your Sensitive Data
First things first, you need to get a handle on the kinds of data your agency deals with every day. Not all files carry the same level of risk, and figuring out the difference is crucial for building a security strategy that makes sense. For a creative business, this data usually falls into a few key categories.
- Client Intellectual Property (IP): This is your bread and butter- and often the most valuable asset you handle. Think unreleased campaign materials, product designs, brand strategies, and proprietary concepts. If this leaks, it could seriously damage your client's competitive edge and your agency's reputation.
- Internal Creative Work: This is your agency’s secret sauce. It covers your own concepts, pitches, and internal strategy documents. Protecting this is vital for keeping your own competitive advantage.
- Financial and Contractual Documents: This bucket includes everything from client contracts and invoices to vendor agreements and your own financial records. If these get out, it could lead to direct financial loss or messy legal disputes.
- Personal Data: You almost certainly handle personal information for clients, employees, and freelancers. This data- names, email addresses, contact details- is subject to UK GDPR regulations.
Once you've categorised your data, you can start to appreciate the potential fallout if any of it were compromised. This isn't just a box-ticking exercise for compliance; it's about protecting the core value of your business and the trust your clients place in you.
Map Your Data and User Access Needs
With a clear picture of what you're protecting, the next move is to map out who needs access and how that data flows through your business. This means tracing the lifecycle of a typical project. Think about how a file moves from the initial brief all the way to final delivery.
A secure file sharing system should feel like a natural part of the creative process, not a barrier to it. The goal is to make the secure path the easiest path for your team to follow, which starts by understanding their actual workflows.
For example, a graphic designer needs full edit access to raw design files, but a client probably only needs view-only access to a final PDF proof. A freelance copywriter might need temporary access to a specific project folder, while your accounts team needs permanent access to billing information.
Building a robust framework means getting these data security best practices in place from the start. Mapping out these access requirements helps you define roles and permissions long before you look at a software platform, ensuring you choose a tool with the granular controls you actually need.
Here in the UK, secure file sharing isn't just a 'nice to have' anymore; it's a fundamental part of running a business, especially as cyber threats continue to rise. In fact, recent analysis shows that around 65% of UK companies now actively use secure file transfer solutions. This shift is driven by a very real need to prevent data breaches in an increasingly challenging security environment.
Choosing the Right Technology for Your Agency
With your security framework sketched out, it’s time to pick the right platform. The market is absolutely flooded with options, and every single one promises flawless security and a seamless experience. For a creative agency, the real challenge is to cut through the marketing fluff and focus on what actually matters.
This isn't about ticking boxes on a feature list. It's about finding a solution that slots neatly into your creative workflows, can grow with your agency, and provides rock-solid security for your most valuable asset: your clients' intellectual property.
This visual data highlights the tangible benefits UK businesses see after implementing dedicated solutions.
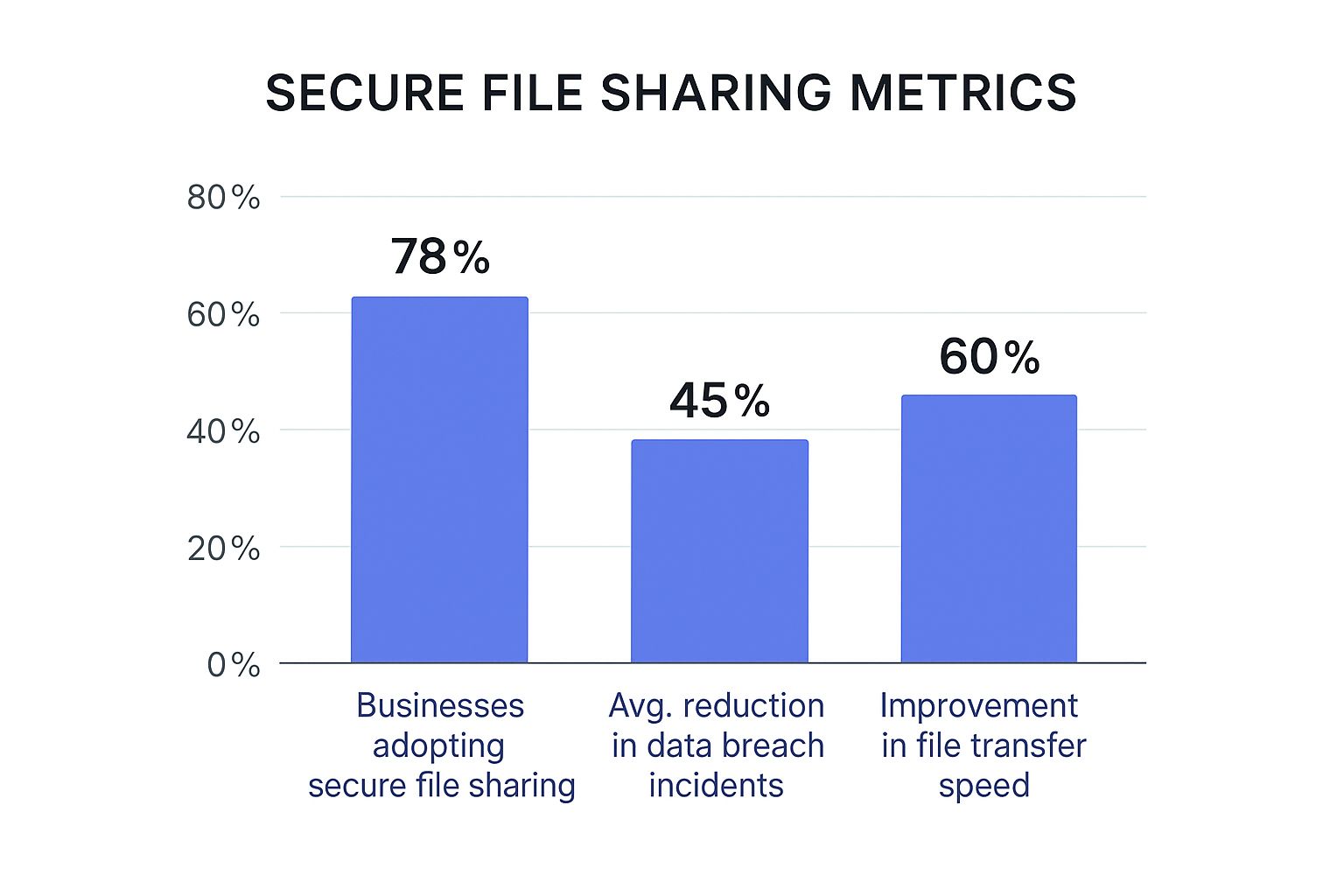
The numbers don't lie. Adopting these systems brings significant gains in both security and efficiency, hammering home the value of moving past basic, insecure methods.
Evaluating Core Security Features
When you're sizing up potential platforms, a few security features are completely non-negotiable for a business that handles sensitive creative work and client data. Think of these as the foundations of a trustworthy system for secure file sharing for business.
- End-to-End Encryption (E2EE): This is the gold standard. It means your files are encrypted on your device and can only be decrypted on the recipient's. Crucially, the service provider can't access them. This is a massive distinction from weaker encryption models.
- Multi-Factor Authentication (MFA): Let's be honest, passwords alone just don't cut it anymore. MFA adds a critical second layer of security, like a code from a mobile app, to verify a user's identity. This simple step dramatically slashes the risk of a breach from stolen credentials.
- Granular Access Controls: Your agency needs precise control over who can do what with your files. Look for systems that let you set specific permissions like 'view-only', 'download-only', or 'edit' for each user, file, or folder. The ability to add expiry dates to shared links is also a must-have for time-sensitive projects.
A common mistake I see is agencies assuming all cloud storage is secure. The reality is that consumer-grade services often lack the robust, business-centric features like E2EE and detailed audit trails, leaving your agency dangerously exposed.
When you're comparing technologies, make sure you prioritise platforms offering proven secure encrypted document sharing solutions. This focus ensures you're choosing a tool built for professional security, not just for casual file storage.
Data Sovereignty and UK Compliance
For any UK-based agency, where your data lives is a massive compliance headache. Data sovereignty and regulatory rules, especially in a post-Brexit world, heavily influence your choice of file-sharing platform. UK companies must prioritise services that host data within UK or EU data centres to comply with the country's strict data protection laws.
Always ask a potential provider where they will store your data. It’s a simple question with big consequences. Opting for a service with UK-based data centres not only helps with GDPR compliance but often improves performance thanks to lower latency.
Key Feature Comparison for Secure File Sharing Solutions
To help you visualise the options, this table breaks down the key differences between the types of platforms you'll encounter. This isn't about specific brand names but rather the category of service they represent, giving you a clearer picture of what you get at each level.
| Feature | Basic Cloud Storage (e.g., Standard Google Drive) | Business-Focused Solution (e.g., Dropbox Business) | High-Security Platform (e.g., Tresorit, Sync.com) |
|---|---|---|---|
| End-to-End Encryption | Rarely offered | Sometimes, as an add-on | Standard and default |
| Granular Permissions | Basic (owner, editor, viewer) | Advanced (expiry, passwords) | Highly granular, per user/file |
| Audit Trails | Minimal or non-existent | Detailed activity logs | Comprehensive and immutable |
| UK/EU Data Residency | Often unclear or not guaranteed | Usually available as an option | A core feature for compliance |
| Creative Tool Integration | Generally good for common apps | Strong, with specific plugins | Varies- check for your tools |
| Scalability | Limited for business needs | Designed for team growth | Built for enterprise-level scale |
The comparison makes it pretty clear. While basic cloud storage is fine for personal photos, it falls seriously short for the demands of a professional agency. A business-focused or high-security platform is a much smarter investment to protect your work, your clients, and your reputation.
Developing a Secure Sharing Policy People Will Actually Use

Here's a hard truth: even the best security tech is useless if your team doesn't use it properly. A formal sharing policy is what connects your chosen platform to your team’s daily habits. It turns abstract security goals into concrete, understandable rules they can follow without friction.
The real challenge isn't just writing a policy; it's creating one that your creative team will actually read, understand, and stick to. Let's be honest, overly technical, jargon-filled documents are usually ignored, leaving your agency just as vulnerable as before.
Your goal should be a living document that gives your team clarity, not just a list of restrictions. It should build a culture of security awareness, making everyone a partner in protecting the business. After all, when research shows that a staggering 95% of cybersecurity breaches are caused by human error, a clear, usable policy becomes one of your most critical defences.
Keep It Simple and Accessible
The most effective policies are written in plain English, not dense legalese. Your team is made up of designers, copywriters, and project managers- not cybersecurity analysts. The document needs to be scannable, well-organised, and easy for anyone to pull up and find what they need.
Ambiguity is your enemy here. Instead of a vague instruction like, "handle sensitive data properly," define what that means in the real world. For example, state clearly that client IP must never be sent via standard email and should only be shared through the company’s approved secure platform.
Creating this from scratch can feel like a huge task. To get a head start, you can explore an IT security policy template and customise it for your agency's specific workflows. This provides a solid structure, ensuring you don’t miss any crucial areas.
Define What Needs Protecting
Your policy must be crystal clear about what you consider "sensitive data." This removes all the guesswork and helps your team understand the 'why' behind the rules. I've found it helps to break it down into categories that make sense in their day-to-day work.
- Client Data: This is everything a client gives you. Think brand assets, confidential project briefs, customer lists, and any personal data they might share.
- Intellectual Property (IP): This covers all the creative work your team produces- concepts, designs, campaign strategies, and all the source files that go with them.
- Business Information: This bucket holds your contracts, financial records, employee details, and internal strategy documents.
Once you categorise your data, you can set specific handling rules for each type. The rules for sharing a draft of the internal company newsletter are going to be completely different from those for sharing a client's unreleased product designs.
A great policy doesn't just list what not to do. It provides clear, positive guidance on the correct way to do things, making the secure method the easiest and most obvious option for your team.
This approach flips the script. Your policy transforms from a list of 'don'ts' into a genuinely helpful 'how-to' guide for secure file sharing for business. It encourages proactive, smart security habits rather than reactive rule-following, which is always more effective in the long run.
Outline Clear Procedures and Responsibilities
A strong policy doesn't stop at definitions; it outlines specific procedures for common scenarios. This is where you translate theory into action, giving your team a clear playbook for their daily tasks.
Essential Procedures to Include:
- Internal Sharing: How should files be shared with colleagues? Should all internal sharing happen on the secure platform, or are tools like Microsoft Teams okay for non-sensitive files? Be specific.
- External Sharing: What is the step-by-step process for sending files to clients, freelancers, and vendors? This should cover how to set link expiry dates, when to use password protection, and what permissions to grant (e.g., view-only vs. edit access).
- Device Usage: Lay out the rules for accessing company files on personal devices (BYOD). This should include requirements for screen locks, up-to-date anti-virus software, and a strict rule against using public Wi-Fi for sensitive work.
- Password Hygiene: Make using a password manager mandatory and ensure multi-factor authentication (MFA) is enabled on every account that touches company data.
- Incident Reporting: Create a simple, no-blame process for reporting a suspected breach or a lost device. The top priority is getting a report quickly so you can mitigate the damage.
By making these procedures explicit, you get rid of confusion and make it far less likely that people will resort to insecure workarounds just because they're faster or easier. The policy becomes a trusted resource they can turn to for guidance, not a document they dread.
Right, you've got your policy written down. But a document gathering dust on a server doesn't protect anyone. The real work starts when you turn those rules into everyday actions. This is where your chosen tech and the policy come together, creating a workflow that's both rock-solid and so smooth your creative team barely notices it's there.
The aim is simple: make the secure way the easiest way. We're moving beyond abstract theory and applying it to the messy reality of creative work. What does secure file sharing for business actually look like when a project manager needs to send a massive design file to a freelancer? Or when a client needs temporary, view-only access to a proposal? It’s all about building repeatable, secure habits.
Get a Grip on Access Control
One of the most powerful tools in your arsenal is role-based access control (RBAC). Forget about setting permissions one person at a time- that’s a recipe for mistakes and a huge time sink. Instead, you create user groups with permissions already defined. It’s cleaner, faster, and dramatically more secure.
For a typical creative project, you might set up groups like these:
- Internal Design Team: Full control. They can edit, upload, and download anything inside the project folder.
- Project Managers: Can view, download, and add comments, but they can't edit or delete core creative assets.
- External Freelancers: Given temporary edit access to a specific sub-folder only, for the exact duration of their contract.
- Clients: View-only and comment-only access to a dedicated "Client Review" folder. Crucially, the link should have an expiry date, say, one week.
Once these groups are set up, managing access is as simple as adding or removing someone. It's a clean, scalable way to enforce the principle of least privilege without creating an administrative nightmare.
A secure workflow lives or dies in the details. Kicking a freelancer out of the system the moment their contract ends is just as vital as letting them in securely. Meticulous access management isn’t a nice-to-have; it's a core security function.
Checklists for Welcoming and Waving Goodbye to Team Members
Your people are your biggest asset, but they're also the most dynamic part of your security setup. A new hire needs the right access from day one, while a leaver's permissions must be wiped completely to prevent old accounts from becoming backdoors. This is where formal checklists are non-negotiable.
A Simple Onboarding Checklist:
- Create User Account: Set up the new team member on your secure sharing platform.
- Assign to Groups: Add them to the right groups (e.g., 'Designers', 'Marketing').
- Enforce MFA: Make sure multi-factor authentication is configured and tested during their induction.
- Share the Policy: Give them a copy of the secure sharing policy and get them to acknowledge they've read it.
And for Offboarding:
- Revoke Access Immediately: On their last day, their account is gone. Don't just disable it- delete it.
- Transfer Assets: Reassign ownership of any files or folders they created to their line manager.
- Review Audit Logs: Do a quick check of their activity log for any unusual downloads or sharing in their final week.
- Notify Collaborators: Let clients or external partners know their point of contact's access has been revoked.
These aren't just bureaucratic steps. They remove guesswork during busy handover periods and protect the integrity of your data.
Your Secret Weapons: Versioning and Alerts
Modern secure sharing platforms come with features that act as an incredible safety net. Two of the most important are file versioning and activity alerts.
File versioning is an absolute lifesaver. It automatically saves a copy of a file every time it's changed. If a critical design file gets corrupted or someone accidentally deletes it, you can simply roll back to an earlier, working version. Even better, it’s a powerful defence against ransomware. If your files get encrypted in an attack, you can often restore a clean, pre-attack version and carry on.
Setting up activity alerts turns your system into an active watchdog. You can get instant notifications for unusual behaviour- like a huge number of files being downloaded at 3 AM or a user trying to poke around in a folder they shouldn't have access to.
UK companies putting these measures in place are already seeing the payoff. Businesses using encrypted file sharing with tight access controls and audit logs are reporting significant operational gains, including up to a 50% reduction in incident response times. If you want to dive deeper into the data, you can learn more about how UK businesses leverage encrypted file sharing. This isn't just about locking things down; it's about boosting client trust by proving you're serious about GDPR compliance.
Training Your Team and Maintaining Vigilance

You can invest in the best security tech and write a flawless policy, but the real strength of your secure file sharing for business strategy comes down to the people using it every day: your team. A system is only as secure as its least aware user, which makes ongoing training and vigilance absolutely essential.
The hard truth is that a staggering 95% of security breaches can be traced back to human error. This isn't about pointing fingers; it's about recognising that a clued-in team is your single most powerful line of defence.
Great security isn't just a set of rules- it’s a culture. When your team understands their personal role in protecting the business’s most valuable assets, from client IP to internal strategies, they become active partners in keeping it safe.
Making Security Training Stick
Let’s be honest: annual, tick-box security training rarely works. For the information to actually sink in, it needs to be engaging, relevant, and continuous. People learn best when they can connect the dots between the training and their daily tasks.
So, instead of dry, technical slideshows, build your training around practical scenarios your creative team will immediately recognise. A brilliant way to start is by running a simulated phishing attack. Show them exactly what a clever phishing email looks like- one that convincingly impersonates a client or a popular software tool they use all the time.
This hands-on approach makes the threat real and tangible. You can also explore how to prevent cyber-attacks with our comprehensive guide, which offers even more strategies to bolster your team’s defences. This style of training highlights the ‘why’ behind the rules, turning security from an abstract chore into a concrete, personal responsibility.
The goal of training isn't to create security experts. It's to build security awareness. A team member who pauses for just a few seconds before clicking a suspicious link because something feels 'off' is a massive security victory.
Scheduling Regular Reviews and Monitoring
A security policy isn't a "set it and forget it" document. Your business evolves, new threats emerge, and your team changes. To keep your security posture strong, you need to build a rhythm of regular reviews and active monitoring.
Schedule a formal security review at least twice a year. This is your dedicated time to:
- Re-evaluate access permissions: Has a freelancer’s temporary project access been properly revoked? Do people who have changed roles still have access to files they no longer need?
- Update the policy: Have you adopted new software or workflows that need to be reflected in your sharing guidelines?
- Review audit logs: Check the activity logs in your secure sharing platform. Look for unusual patterns, like large downloads happening outside of business hours or a spike in failed login attempts.
These reviews don't need to be long, drawn-out meetings. A focused, one-hour session with key people can be incredibly effective for spotting and closing potential security gaps before they turn into real problems.
Keeping Everything Updated
Finally, staying vigilant means keeping both your software and your policies current. Technology providers are constantly releasing security patches to protect against newly discovered vulnerabilities. One of the simplest yet most critical steps you can take is enabling automatic updates for your operating systems, browsers, and your chosen secure sharing platform.
Your policies need to stay fresh, too. When you onboard a new client collaboration tool or change how you work with freelancers, your secure sharing policy must be updated to match. Communicating these changes clearly ensures everyone is on the same page. This constant cycle of training, reviewing, and updating fosters a security-first mindset that turns your entire team into your greatest security asset.
Answering Your Secure File Sharing Questions
Even with a solid plan and the right tech, questions are bound to pop up. Let's be honest, the world of secure file sharing for business is packed with technical jargon and compliance rules that can feel a bit overwhelming at first.
This is where we tackle the common questions we hear from creative agencies right here in the UK. We'll give you clear, straightforward answers to help you get over those final hurdles and feel confident in the system you're building.
What Is the Most Important Feature for a Creative Agency?
While end-to-end encryption is the non-negotiable foundation of security, the single most vital feature for a creative agency is granular access controls. Think about it: your projects are a constant whirlwind of collaboration. You've got your in-house team, freelance talent, and clients all needing access, but rarely to the same degree.
A great system lets you fine-tune permissions with pinpoint accuracy. You need to be able to set 'view-only', 'comment-only', or full 'edit' rights for a specific file or folder. Even better is the ability to set automatic expiry dates for shared links.
This one feature directly tackles two of the biggest risks in a creative workflow: an accidental edit on a final, client-approved proof, and the unauthorised sharing of your valuable intellectual property long after a project is done and dusted.
How Does This Help with UK GDPR Compliance?
Secure file sharing isn’t just a nice-to-have; it's a core part of being compliant with UK GDPR. The regulation is very clear that businesses must use the right technical and organisational measures to protect any personal data they handle.
A proper secure sharing platform helps you tick these boxes in a few concrete ways:
- End-to-End Encryption: This is a direct technical safeguard. It protects data from prying eyes, both when it's sitting on a server (at rest) and when it's being sent over the internet (in transit).
- Detailed Audit Trails: These logs create a permanent record of who accessed what data and when. This is absolutely critical for accountability and for proving you've done your due diligence if you ever face a data subject access request or a breach investigation.
- Strict Access Controls: This is all about enforcing the 'principle of least privilege'. By making sure people can only see the data they absolutely need to do their job, you dramatically reduce the risk of accidental exposure.
- Data Residency: Choosing a provider with UK or EU-based data centres is a big deal for meeting data sovereignty rules under UK GDPR.
Using a platform with these features is a clear, tangible step towards meeting your legal duties. For specific compliance questions around verifying individuals, exploring various KYC tools for verification can also point you in the right direction for certain business needs.
Is Standard Cloud Storage Secure Enough for My Business?
In almost every scenario we've seen, the answer is a firm no. Consumer-grade cloud storage- even the paid business versions of popular free platforms- simply wasn't designed for the security pressures of a professional creative agency. They're usually missing the key features that truly protect high-value business data.
The core difference comes down to control and visibility. Consumer tools are designed for convenience, while true business solutions are designed for security and compliance. They solve different problems.
For example, many standard services don't offer true end-to-end encryption, which means the provider themselves could technically get a look at your files. They also fall short on other critical business functions.
Key Deficiencies in Standard Cloud Storage:
- Lack of Comprehensive Audit Logs: You often have no way of seeing a detailed history of who's accessed a file. That's a huge compliance blind spot.
- Limited Access Controls: Permissions are typically basic, like 'viewer' or 'editor', lacking the nuanced control needed for complex projects with multiple stakeholders.
- No Remote Wipe: What happens if an employee's laptop is lost or stolen? With most consumer tools, you can't remotely delete the company files synced to that device.
- Unclear Data Residency: You might have zero guarantee where your data is actually being stored, creating a massive risk under UK GDPR.
While these services are fantastic for personal photos and documents, relying on them for your client's intellectual property or sensitive business files introduces a level of risk that just isn't acceptable. Investing in a proper, business-grade platform is essential. Just as important is improving your team's overall security awareness; you can learn more by reading about strengthening your team’s defense with essential cyber hygiene.
At InfraZen Ltd, we help creative agencies implement secure, efficient IT systems that get out of the way and let you focus on what you do best. If you're ready to build a secure file sharing workflow that protects your clients and your business, we can help. Learn more about our human-centred approach to IT for creatives.

