Data Loss Prevention (DLP) isn't just another bit of security software. It's a full-blown strategy, blending technology with smart policies and processes to stop your sensitive information from walking out the door.
Think of it as a specialised security guard for your data. This isn't just a bouncer at the door; this guard knows exactly what information is confidential and has the authority to prevent it from being leaked, stolen, or even accidentally shared by a well-meaning employee.
Decoding Data Loss Prevention

Let’s use an analogy. Imagine your business is a library. Some books, like public flyers, can be taken by anyone. But others are priceless, rare manuscripts that must never leave the building under any circumstances.
Data Loss Prevention is your head librarian. This person knows precisely which documents are sensitive and installs security systems to make sure they stay where they belong. It's a complete system designed to identify, monitor, and protect your data, no matter where it is-whether it’s being sent in an email, saved to a cloud drive, or copied onto a USB stick.
For UK businesses juggling valuable client files, financial records, or confidential project details, this level of control is no longer a 'nice-to-have'. It's essential.
Why DLP Matters Now More Than Ever
The threat of a data breach isn't some distant possibility; it's a constant, pressing concern. According to the UK Government's Cyber Security Breaches Survey, a staggering 43% of businesses reported some form of cyber attack or data breach last year. That number alone shows just how badly robust protective measures are needed.
Data Loss Prevention shifts your security posture from reactive to proactive. Instead of cleaning up the mess after a breach, you’re actively stopping sensitive information from ever leaving your control.
To get to that proactive state, DLP focuses on a few key activities:
- Identifying Critical Data: You can’t protect what you don’t know you have. The first step is always to locate and classify the sensitive information spread across your network.
- Monitoring Data in Motion: This means keeping a close watch on data as it travels through email, web apps, or other network channels.
- Controlling Endpoint Actions: DLP can step in and block actions like printing, copying files to external drives, or even screen-capturing sensitive documents on employee computers.
To help break these ideas down, here’s a quick overview of the core concepts.
Quick Overview of Data Loss Prevention Concepts
This table translates the technical jargon into simple explanations and business analogies, making it easier to grasp how each part of DLP works.
| Concept | Simple Explanation | Business Analogy |
|---|---|---|
| Data Identification | Finding and tagging your important information. | Taking inventory of your most valuable assets and labelling them "High Value". |
| Data in Motion | Protecting data as it travels over the network. | An armoured van securely transporting cash between banks. |
| Data at Rest | Securing data stored on servers, laptops, or in the cloud. | A high-security vault where gold bars are stored overnight. |
| Data in Use | Guarding data while it's being used by an employee. | A security guard watching over a jeweller while they work on a diamond. |
| Policy Enforcement | Automatically blocking or flagging risky actions. | A checkout security scanner that beeps if an item hasn't been paid for. |
Each of these components works together to create a safety net, ensuring your data is protected at every stage of its lifecycle.
If you're operating heavily in the cloud, understanding the nuances of Cloud Data Loss Prevention is particularly important.
Ultimately, a strong DLP strategy is a cornerstone of modern cybersecurity. For some practical next steps, check out our guide on how to prevent data loss.
The Three Pillars of an Effective DLP Strategy
A solid data loss prevention strategy is less like a simple fence and more like a comprehensive shield, protecting your information everywhere it lives. It’s built on three core pillars that work together, securing your data whether it’s sitting still, on the move, or actively being used. Understanding how these pillars support each other is key to closing the security gaps that both external attackers and internal threats love to exploit.
Each pillar is designed to address a unique state of your data, making sure no weak points are left unguarded.
Protecting Data in Motion with Network DLP
First up is Network DLP, which acts a bit like an airport scanner for all your business information. It monitors every piece of data travelling across your network-whether it’s being sent in an email, uploaded to a website, or transferred through an app. The system inspects data packets in real-time, ready to identify and block sensitive content from leaving your secure perimeter without permission.
Imagine an employee accidentally attaches a spreadsheet full of client financial details to an email meant for a personal account. A Network DLP system would spot the classified information inside that file and block the email from ever being sent. It's an immediate intervention that stops a potential data leak before it even has a chance to happen.
This diagram shows how the core components of a successful data loss prevention framework fit together.
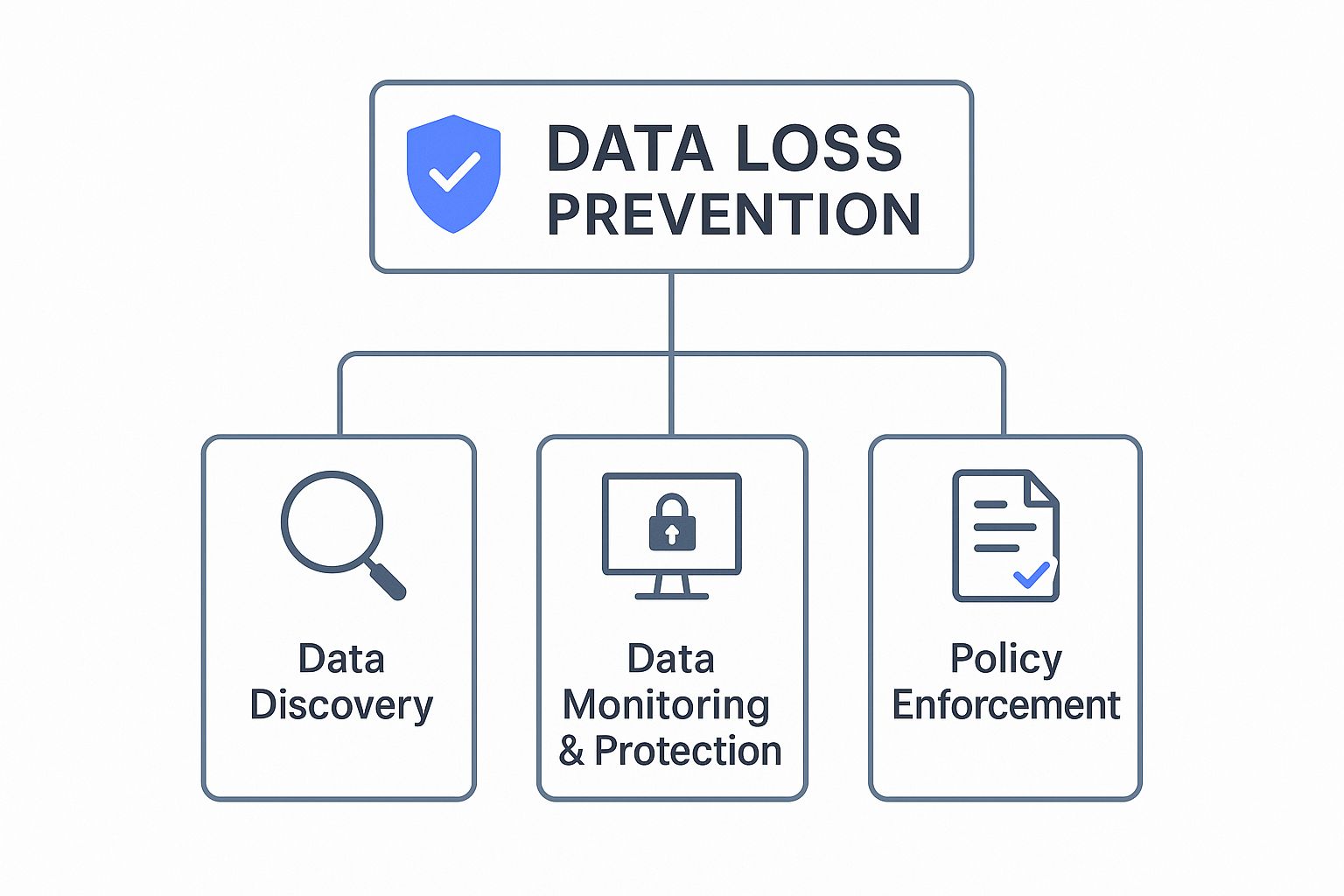
As you can see, effective DLP isn't a single action. It’s a continuous cycle of discovering, protecting, and enforcing rules around your company's data.
Securing Data at Rest with Storage DLP
Next, we have Storage DLP, which is all about protecting your data at rest. This covers all the information stored on your company’s servers, in cloud databases like Google Drive or Dropbox, and on company-issued laptops. This pillar works by scanning these storage locations to figure out where your sensitive data lives and making sure it’s properly locked down.
A crucial part of this is data classification. By identifying and tagging sensitive files, you can enforce specific security policies-like encryption or access restrictions-to ensure only authorised people can view or move them.
A strong DLP strategy goes hand-in-hand with wider data governance principles. Getting a handle on key data governance best practices will seriously boost your data protection capabilities.
Controlling Data in Use with Endpoint DLP
Finally, there’s Endpoint DLP, which secures your data in use. This pillar monitors and controls what people can do on their devices-the endpoints-like desktops, laptops, and mobile phones. It’s focused on stopping unauthorised actions like copying sensitive files to a USB drive, printing a confidential document, or even taking a screenshot of a customer list.
This is where having tight control over user actions becomes absolutely critical. Properly managing who can access and handle data is a foundational security measure. To dig deeper into this, check out our insights on why access management has become a critical part of cybersecurity.
By integrating endpoint controls, your organisation gets granular visibility into user behaviour and can stop risky actions right at the source, completing the protective shield around your most valuable information.
The True Cost of a Data Breach for UK Businesses

It’s one thing to talk about data loss prevention in theory. It’s another to see the real-world fallout when it goes wrong. For a UK business, a data breach isn’t just an IT headache; it’s a full-blown financial and reputational crisis that can spiral out of control with terrifying speed. The costs don't stop when the breach is contained-they ripple through every part of the organisation for months, sometimes years.
The first hit is usually the most direct: the eye-watering financial penalties and clean-up costs. Thanks to the General Data Protection Regulation (GDPR), fines for getting this wrong can be crippling, reaching up to 4% of a company's annual global turnover. But that’s often just the opening act.
The Escalating Financial Fallout
We're seeing more and more how quickly the bill for data loss adds up. When NHS pathology partner Synnovis was hit by a cyberattack, the financial impact was a staggering £32.7 million. The British Library's ransomware incident racked up recovery costs of around £6 to £7 million, not to mention the massive operational chaos it caused. As these examples show, the numbers climb fast. You can dig into more of the figures by checking out these UK cybersecurity statistics.
Beyond those headline-grabbing figures, there’s a long and painful list of other expenses that businesses have to shoulder. These typically include:
- Incident Response: The cost of calling in cybersecurity experts to stop the bleeding, figure out what happened, and get your systems back online.
- Legal Fees: Navigating the legal minefield that follows, which can include class-action lawsuits from angry customers.
- Notification Costs: The surprisingly high expense of formally telling customers, regulators, and anyone else who needs to know about the breach.
- Credit Monitoring: Offering free credit monitoring services to affected individuals to protect them from potential identity theft.
These escalating expenses are a harsh reminder of the hidden cost of bad IT and why it pays to get things right before a crisis hits.
More Than Money: Operational and Reputational Damage
While the financial toll is brutal, the non-monetary damage can be even more destructive over the long term. A data breach can bring day-to-day operations to a grinding halt. Projects get derailed, deadlines are blown, and your team gets pulled away from their actual jobs to manage the chaos, torching productivity in the process.
The most profound cost of a data breach is often the erosion of trust. Once lost, customer confidence is incredibly difficult to regain, leading to client churn and a tarnished brand reputation that can take years to repair.
This is exactly why seeing data loss prevention as just another business expense is a huge mistake. Think of it as an essential investment in your company’s resilience and, frankly, its survival. By proactively putting a DLP strategy in place, you’re not just protecting data-you're safeguarding your financial stability, your ability to operate, and the good name you've worked so hard to build.
Key Technologies That Power Modern DLP
Modern data loss prevention isn't just a simple set of rules anymore; it's an intelligent, multi-layered system that’s become incredibly sophisticated. These tools work in concert to build a formidable defence, moving way beyond just blocking actions to proactively sniffing out and neutralising threats before they can do any real damage. The big shift here has been the introduction of artificial intelligence.
AI-powered analytics act like a vigilant overseer, constantly learning the normal rhythm of how data is accessed and moved around within your business. When it spots something out of the ordinary-like an employee suddenly downloading huge volumes of client files late at night-it can flag that activity as a potential risk long before a human analyst ever could. This predictive capability is what turns DLP from a simple gatekeeper into an active threat hunter.
Building a Layered Defence
A strong DLP strategy relies on more than just one tool. It cleverly combines several key technologies that each tackle a different piece of the security puzzle, creating a cohesive and resilient defence.
Across the UK, effective data loss prevention strategies are increasingly leaning on these advanced technologies. Tools like AI-based threat detection have helped cut down on data breach incidents, while multi-factor authentication (MFA) is now standard practice in most mid-to-large businesses. What's more, companies implementing zero trust architectures have seen substantially fewer successful breaches. You can find more insights on these data breach statistics on sqmagazine.co.uk.
Key components of this tech stack include:
- Multi-Factor Authentication (MFA): This is your essential first line of defence. By demanding a second form of verification beyond just a password, MFA ensures that even if login details are stolen, an unauthorised user can't get into your sensitive systems.
- Zero Trust Architecture: This security model works on a simple but powerful principle: never trust, always verify. It assumes threats can exist both inside and outside the network, demanding strict identity checks for every user and device trying to access anything.
- Security Information and Event Management (SIEM): Think of a SIEM system as the central nervous system for your security operations. It pulls in and analyses log data from all your applications, devices, and network hardware, giving you a single, unified view of every security event happening.
When you integrate a SIEM system with your DLP solution, its power is amplified.
Imagine a SIEM flags an unusual login from an unrecognised location (via MFA alerts) at the exact moment the DLP tool detects a large data transfer from that same user's account. This correlated intelligence gives you immediate, actionable proof of a likely breach in progress.
Another vital piece of this puzzle is encryption. For a deep dive into how that works, check out our ultimate guide to managed data encryption services. By combining AI, MFA, zero trust, and SIEM, you create a robust, proactive system that doesn't just react to threats-it anticipates and prevents them. This integrated approach is the bedrock of modern, effective data loss prevention.
How to Implement a Data Loss Prevention Strategy

Putting a real-world data loss prevention strategy into action doesn’t have to be a monumental task. The trick is to break it down into manageable steps, building a robust defence that actually protects what matters most to your company.
And where do you start? Not with flashy technology, but with a simple, fundamental question: what data do you actually have? You can't protect what you don't know exists.
This first step is all about data discovery and classification. The goal here is to get a handle on where your sensitive information-think client lists, financial records, or project IP-is hiding out. Once you've located it, you need to classify it based on its importance, essentially tagging your crown jewels so your security systems know what to guard most fiercely.
Building Your Implementation Roadmap
With a clear map of your data, you can start writing the rules of engagement. This means developing clear, easy-to-understand data handling policies that dictate exactly how employees can interact with sensitive information. These policies become the instruction manual for whatever DLP tools you put in place.
Getting started with a DLP strategy can feel complex, but it boils down to a few core phases. Think of it as a clear roadmap from identifying your assets to keeping them safe long-term.
Here’s a simplified table breaking down the journey:
DLP Implementation Phases
| Phase | Key Actions | Primary Goal |
|---|---|---|
| 1. Identify & Classify | Locate all sensitive data across your network, cloud, and devices. Tag it based on importance. | To create a comprehensive inventory of the assets you need to protect. |
| 2. Define Policies | Create rules for how data can be used, shared, and stored. For example, "No financial data on USBs." | To establish clear, enforceable guidelines for data handling. |
| 3. Deploy Tools | Select and configure a DLP solution that aligns with your specific needs and policies. | To automate the enforcement of your data protection rules. |
| 4. Monitor & Refine | Continuously watch for alerts, review incidents, and adjust policies as your business evolves. | To ensure your DLP strategy remains effective and adapts to new threats. |
This roadmap provides the structure, but making it stick requires more than just process. It requires your people.
Securing Buy-In and Training Your Team
Here’s the thing: technology alone will never stop data loss. Your people are the most critical part of your defence. Securing buy-in from leadership is essential for getting the budget and resources you need, but training your employees is where the real work happens.
They need to understand why these policies exist and how their everyday actions contribute to the company's security. It's about building a culture, not just enforcing rules.
An effective DLP strategy is a living process, not a one-time project. It requires continuous monitoring and a culture of security awareness where everyone understands their role in protecting company data.
This means running regular, engaging training sessions and making security a shared responsibility from the top down. The final piece is establishing a continuous monitoring process, allowing you to respond to incidents, spot patterns, and fine-tune your policies over time. It’s this proactive, cyclical approach that turns your DLP strategy from a static document into a strong, adaptive shield for your business.
Moving From Reactive to Proactive Data Protection
Effective data loss prevention isn't a one-time setup; it's a continuous commitment. Think of it less like installing a burglar alarm and more like having a dedicated security team constantly patrolling, adapting, and learning.
The whole point is to prevent data breaches before they happen, not just clean up the expensive mess afterwards. It’s about shifting your business from a vulnerable, reactive position to one of control and confidence.
Instead of waiting for an alert that your critical data has already been compromised, you have systems in place that stop unauthorised actions in their tracks. This means your team can focus on their actual work, knowing the company’s most valuable assets are secure.
Taking Control of Your Data Security
For UK businesses, the stakes are simply too high to leave data protection to chance. Building a proactive defence requires a well-planned and consistently managed programme.
The core message is simple: true data security means anticipating threats, not just responding to them. This proactive stance is what separates resilient businesses from those merely waiting for the next incident.
A proactive strategy is built on several key pillars:
- Continuous Monitoring: Actively watching for unusual activity rather than just waiting for alarms to go off.
- Regular Policy Reviews: Ensuring your security rules evolve as your business and the threats around you change.
- Ongoing Employee Training: Building a security-aware culture where everyone understands their role in protecting data.
By embracing this forward-thinking mindset, your organisation takes charge of its security destiny. This posture protects your reputation, finances, and client trust, allowing you to operate with the quiet confidence that your most critical asset-your data-is properly safeguarded.
Got Questions About Data Loss Prevention? We've Got Answers.
Even with a solid plan, a few questions always pop up when businesses start thinking about data loss prevention. Let's clear up some of the most common ones to give you a better sense of what a modern DLP programme really does.
Is DLP Just for Big Companies?
Not a chance. While it's true that large corporations rely on heavy-duty DLP systems, businesses of every size have sensitive data that needs protecting. We're talking about customer lists, employee records, and confidential financial details.
The great news is that modern DLP solutions are built to scale. There are plenty of options out there designed to fit the needs and budgets of small to medium-sized enterprises (SMEs). A data breach can be just as damaging-if not more so-for a small business, which makes DLP a vital piece of the puzzle for any organisation.
How Is DLP Different From a Firewall?
A firewall and a DLP system are two different players on the same security team. Think of a firewall as the bouncer at the door-it controls who gets in and out of your network based on a strict guest list, stopping unauthorised traffic from ever reaching you.
A DLP solution, on the other hand, is focused entirely on the data itself. It understands the content and context of your information, and its main job is to stop sensitive data from leaving your network when it shouldn't.
A firewall is like the main security gate at a festival, checking tickets on the way in. DLP is the security guard inside the grounds, making sure no one walks out with the headline act's equipment.
One protects the perimeter; the other protects the crown jewels inside.
Can DLP Stop Every Single Data Breach?
DLP is a powerhouse for preventing many kinds of data breaches, especially those caused by accidental leaks or insiders deliberately trying to steal information. It's incredibly effective at blocking sensitive files from being attached to the wrong email, copied to a USB stick, or uploaded to a personal cloud account.
However, no single tool can stop 100% of all threats. That's why a complete cybersecurity strategy should always include DLP as one critical layer among several others.
This layered approach should always include:
- Anti-malware software to guard against viruses and ransomware.
- Regular security training for employees to build a culture of vigilance.
- A solid incident response plan so you know exactly what to do if a breach happens.
When you combine these elements, you build a defence that's far stronger and more resilient. A good DLP system is a cornerstone of that strategy, but it works best when it's part of a team effort.
Ready to move from reactive fixes to proactive protection? InfraZen Ltd provides strategic IT management and cybersecurity that keeps your creative business secure and focused. Discover your IT health score and learn how we can safeguard your most valuable assets.

