Endpoint security is all about protecting the countless devices that plug into your company's network-laptops, servers, phones, you name it. It's like having a dedicated security guard for every single door and window into your business, watching for unauthorised access and fending off cyber threats aimed at those entry points.
Understanding Endpoint Security

Think of your business network as a central fortress. Every single device that connects to it, whether it's a designer's MacBook in the studio or a project manager's phone on the train, is a potential way in. Endpoint security is the strategy and the toolkit you use to lock down and monitor every one of those entry points.
Without it, a single compromised laptop can give an attacker a free pass to your most sensitive data. This is why just guarding the main fortress walls isn't enough anymore. The game has changed, and the real battle is now fought at the endpoints themselves.
To make this crystal clear, here’s a quick breakdown of the core ideas.
Endpoint Security at a Glance
| Concept | Simple Explanation |
|---|---|
| Endpoint | Any device (laptop, phone, server) that connects to your network. |
| Network Perimeter | The traditional "walls" of your office network. |
| Attack Surface | The total number of potential entry points for a cybercriminal. |
| Endpoint Security | The practice of securing each individual device, not just the central network. |
This table shows how the focus has shifted from a single, central defence to a distributed one, where every device plays a role in keeping your business safe.
Why It Matters More Than Ever
The way we all work has completely changed, and in doing so, it has massively expanded the "attack surface" for every business. The boom in remote working and the habit of using personal devices for work means your company's data is now being accessed from countless locations, far beyond the old office walls.
Each of these endpoints is a juicy target for cybercriminals looking to cause chaos through:
- Data Breaches: Stealing sensitive client information, valuable intellectual property, or your financial records.
- Ransomware Attacks: Encrypting your most critical files and demanding a huge payment to get them back.
- Operational Downtime: Grinding your business to a halt, leading to lost productivity and revenue.
The threat isn't some far-off possibility; it's a real and present danger for UK businesses. Cyber security breaches are alarmingly common, with 67% of medium-sized businesses and a staggering 74% of large businesses hit by attacks in the last year. These incidents almost always start with one weak endpoint. You can dive into the full findings from the UK Government to see the trends for yourself.
Getting your head around what is endpoint security is the first, most critical step toward building a truly resilient defence. It's about moving beyond basic antivirus and putting in place a smart, layered system that can spot, block, and shut down threats before they do any real damage.
The Core Components of Modern Endpoint Protection
Modern endpoint protection isn’t a single piece of software. It’s an integrated system of defence. Think of it less like a simple padlock and more like a high-tech security setup for your office, with multiple layers all working together. To really get what endpoint security is, we need to look at the key technologies that form this protective shield around your devices.
These components are designed to work in concert, creating a defence that is much stronger than the sum of its parts. Each one plays a distinct role, from preventing initial infections to hunting down threats that somehow manage to slip past the first line of defence.
The following graphic really drives home why this matters, showing how endpoints are targeted, how good protection can slash breach numbers, and where things stand with adoption.
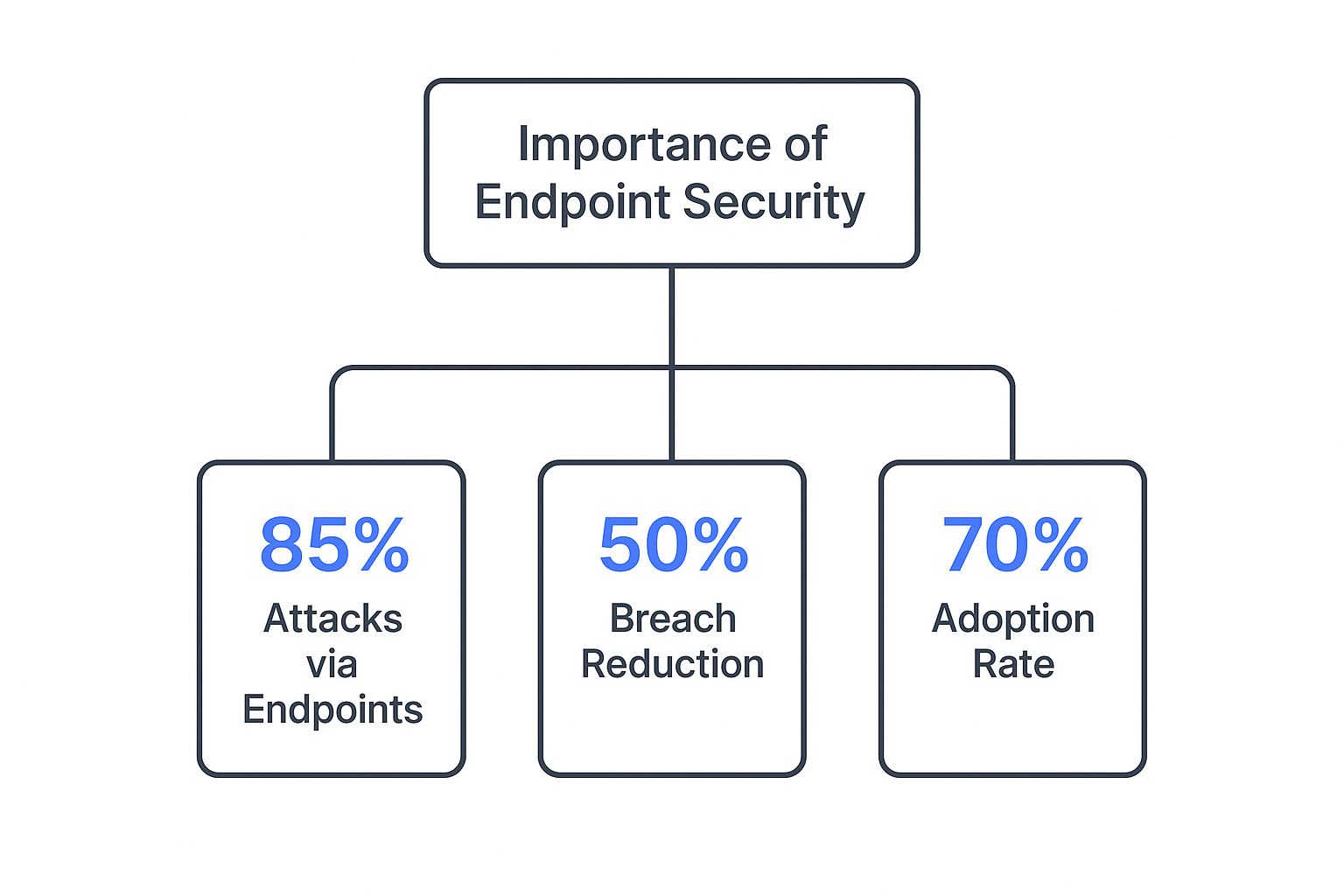
This highlights a sobering fact: the vast majority of attacks (85%) begin right at the endpoint. But the good news is that implementing robust security can cut the likelihood of a breach in half.
Next-Generation Antivirus (NGAV)
This isn't the antivirus you remember from ten years ago. Traditional antivirus relied on a library of known virus "signatures"-it could only stop threats it had already seen and catalogued. Next-generation antivirus (NGAV) is far more intelligent. It uses advanced techniques like machine learning and behavioural analysis to spot and block malware that has never been seen before.
Instead of just checking a file's fingerprint, NGAV watches how it behaves. If a program suddenly starts trying to encrypt all your files or connect to a suspicious server-classic ransomware behaviour-NGAV will shut it down instantly, even if that specific piece of malware is brand new.
Endpoint Detection and Response (EDR)
If NGAV is the guard at the gate, then endpoint detection and response (EDR) is the network of security cameras and motion sensors monitoring everything inside. EDR constantly records activity across all your endpoints, giving you deep visibility into what’s actually happening on your network.
It collects data on running processes, network connections, and user actions. When suspicious activity is detected-for instance, an accountant's laptop suddenly trying to run network scanning tools-the EDR platform flags it for investigation. This allows security teams to hunt for threats, isolate a compromised device, and understand the full scope of an attack to stop it from happening again.
A key principle for modern endpoint security is collaboration. As Microsoft and its partners noted in a recent summit, no single solution is perfect. A layered approach combining NGAV, EDR, and other tools offers a more resilient defence against increasingly complex threats.
These core tools are backed up by other vital components like:
- Application Control: This prevents unauthorised software from being installed or run on a device, drastically reducing the chances of malware ever getting a foothold.
- Web Filtering: This simply blocks access to malicious websites, stopping users from accidentally downloading threats or falling for phishing scams that lead to dodgy sites.
Key Challenges in Managing Endpoint Security

If only managing endpoint security was as simple as installing a program and walking away. The reality, especially for fast-paced UK creative agencies, is a lot messier. The way we work now has thrown up some serious hurdles.
One of the biggest headaches is the rise of remote working and personal devices, a trend often called Bring-Your-Own-Device (BYOD). When your team works from home, a client's office, or their favourite coffee shop, their laptops and phones are connecting to all sorts of unsecured networks. This instantly stretches your attack surface, and every new connection is another potential weak point.
The Problem of Tool Sprawl
Another major challenge is something we in the industry call "tool sprawl" – the habit of buying more and more security products to counter every new threat that pops up. This often leads to a chaotic patchwork of solutions that don't talk to each other, creating a system riddled with gaps and visibility blind spots. It’s like hiring ten different security guards who all speak different languages; things will inevitably get missed.
Getting a handle on how to prevent cyber attacks often means simplifying your defences, not making them more complicated.
A worrying study from 451 Research highlights a major issue in UK businesses. When hit by ransomware, a tiny 13% said their endpoint security actually blocked the attack. Even more telling, 40% of those organisations just spent more money on more endpoint tools afterwards, instead of rethinking their strategy.
This data proves that just throwing money at the problem rarely works. You need a unified, strategic approach to build a defence that stands a chance against today’s sophisticated threats.
What Threats Does Endpoint Security Actually Stop?
To really get what endpoint security is all about, you have to understand the dangers it’s designed to shut down. These aren’t just abstract worries; they're real attacks that can paralyse your agency, leak client data, and hit your finances hard. A solid endpoint security strategy is your first line of defence against these specific threats.
Of course, the best tech in the world can’t stop a person from accidentally clicking a bad link. That's why building your team's awareness is such a critical layer of your defence. You can learn more about strengthening your team's defense with essential cyber hygiene.
For now, let's break down the common attacks aimed squarely at your devices.
Phishing and Social Engineering
Phishing attacks are just clever scams. They're designed to trick your team into handing over sensitive details like passwords or financial information. An attacker might send an email that looks like it’s from a trusted client or a software vendor, pushing the user to click a dodgy link or open a dangerous attachment.
Once that link is clicked on a laptop or phone, it can install malware or redirect to a fake login page that steals credentials. Endpoint security helps by:
- Blocking access to known malicious websites before a user can even land on them.
- Scanning email attachments for hidden malware, stopping them from ever being opened.
- Detecting suspicious activity that might kick off after someone accidentally clicks the wrong thing.
Looking at security from a business perspective is always a smart move. It's helpful to get familiar with the core principles of managing cyber risk.
Ransomware Attacks
Ransomware is a particularly nasty piece of work. It’s malware that encrypts every file on a device-or even across your whole network-and holds them hostage. The attackers then demand a hefty payment, usually in cryptocurrency, for the key to get your files back.
For a creative agency, this is a nightmare scenario. Imagine losing access to all your project files, client work, and business records in an instant.
Endpoint security solutions with next-generation antivirus (NGAV) are built to spot ransomware behaviour. They can detect and stop the unauthorised encryption process in its tracks, preventing widespread damage before it can even start.
Malware and Spyware
This is a catch-all term for nasty software, covering everything from viruses and trojans to spyware built to secretly steal data. This kind of malware can find its way onto an endpoint through a downloaded file, a weak application, or a compromised website.
Once it's active, it can log keystrokes to steal passwords, copy sensitive documents, or even use your device's power to launch attacks on others. Modern endpoint protection is always watching for this stuff, identifying and quarantining malicious files to keep your valuable data out of the wrong hands.
To make this clearer, let's look at how specific defences line up against common threats.
Threats vs Endpoint Defences
The table below shows how different endpoint security features are designed to counter specific cyber threats you're likely to face.
| Threat Type | How It Works | Primary Endpoint Defence |
|---|---|---|
| Phishing | A deceptive email tricks a user into clicking a malicious link or downloading an infected attachment. | Web Filtering blocks malicious sites. Email Security scans attachments and links. |
| Ransomware | Malware encrypts files on a device or network and demands payment for their release. | Next-Gen Antivirus (NGAV) with behavioural analysis detects and stops unauthorised encryption. |
| Spyware | Malicious software secretly records keystrokes or steals files from a compromised device. | Anti-Malware/Anti-Spyware scanning constantly monitors for and quarantines suspicious processes. |
| Zero-Day Exploit | An attack that targets a software vulnerability before a patch or fix is available. | Endpoint Detection and Response (EDR) monitors for unusual behaviour patterns, not just known threats. |
As you can see, a layered approach is essential. No single tool does it all, which is why a comprehensive endpoint protection platform is so crucial for keeping your creative work safe.
How to Choose the Right Endpoint Security Solution

Picking the right endpoint security isn’t just about ticking a box; it’s about finding a solution that fits your agency like a glove. With a crowded market full of big promises, knowing what to look for is vital to avoid wasting money on shelfware that doesn't actually protect you.
Your evaluation needs to go beyond the marketing hype and focus on a few critical criteria. Start by looking at the solution's detection capabilities. Does it still lean on old signature-based methods, or does it use modern techniques like behavioural analysis to catch brand-new, unseen threats? This is the key difference between basic antivirus and real endpoint protection.
Evaluating Key Platform Features
When you're shortlisting vendors, zero in on the features that directly impact your efficiency and visibility. After all, a powerful platform is useless if it’s too complicated to manage day-to-day.
Here's what to look for:
- Centralised Management: Can you monitor every single device-whether it's in the office or remote-from one intuitive dashboard? For busy teams, this unified view isn't a luxury; it's non-negotiable.
- Performance Impact: Will the security agent slow down your team's machines? Modern solutions are designed to be lightweight, but you should always test the impact on device speed, especially for resource-heavy creative work.
- Automation and Response: Does the tool automatically isolate a compromised device or neutralise a threat? Automation is a game-changer. It frees up your team and contains attacks much faster than a human ever could.
To make an informed decision, it's helpful to see how endpoint security fits into the broader world of top cybersecurity solutions. This context helps you build a more complete, layered defence.
Matching the Solution to Your Business Size
The needs of a small, agile creative studio are worlds away from those of a large enterprise. Small businesses need effective, easy-to-manage protection that doesn’t demand a dedicated, in-house security team.
For many small UK businesses, this is a huge gap. Shockingly, research shows that about a third of small UK businesses use free, consumer-grade security, and an astonishing 23% have no dedicated endpoint protection at all. This leaves them dangerously exposed to professional attacks that these basic tools simply aren't built to stop.
When you're talking to vendors, ask direct questions. "How does your platform help a business with very limited IT staff?" or "Can you show me a real-world example of how you stopped a ransomware attack?" Their answers will tell you everything you need to know.
Ultimately, understanding the basics of endpoint security is only the first step. For agencies that want expert oversight without the day-to-day management headache, exploring an option like managed endpoint detection and response can provide enterprise-grade security that’s properly scaled to the budget and needs of a creative business.
Your Questions on Endpoint Security, Answered
Jumping into cybersecurity can feel like learning a new language. To clear things up and give you a bit more confidence, here are some straightforward answers to the questions we hear most often about endpoint security.
Is Endpoint Security Just a Fancy Name for Antivirus?
Not at all. Think of traditional antivirus as a bouncer with a list of known troublemakers. If someone's not on the list, they might get in. It’s reactive.
Modern endpoint security is more like a full-blown security team that’s actively looking for suspicious behaviour, not just known faces. It includes next-generation antivirus (NGAV) to spot new threats, endpoint detection and response (EDR) to monitor what's happening in real-time, and a central command post to manage it all. It’s a far more proactive and comprehensive way to protect your devices.
Do We Really Need Endpoint Security? We’re Just a Small Agency.
Absolutely. In fact, small businesses are often seen as low-hanging fruit by cybercriminals who assume their security is weaker. It's a dangerous assumption to let them make.
A single data breach or ransomware attack can be catastrophic for a smaller agency, leading to huge financial hits and a damaged reputation you might not recover from. Endpoint protection isn't an enterprise luxury; for a creative business, it's a critical part of staying in business.
How Does This Work When My Team is Remote?
It's actually essential for any agency with a remote or hybrid team. Modern endpoint security platforms are built for this reality.
They are managed from the cloud, which means they protect your team's laptops and mobiles no matter where they are-a home office, a coffee shop, or a co-working space. Every device is held to the same high security standard as if it were plugged in at the office, closing a massive gap that remote work often creates.
Modern solutions are designed to be lightweight with a minimal performance impact. Unlike older, clunky antivirus programs, today's top platforms use cloud-based analysis and efficient agents that won't bog down employee devices, ensuring productivity isn’t compromised.
This means your creative team can keep their flow without frustrating slowdowns, and your agency stays protected. It all comes down to choosing the right platform to get that balance just right.
At InfraZen Ltd, we help creative agencies work securely and efficiently. We handle the technical complexities behind the scenes, so you can focus on your craft without worrying about cyber threats. To learn how we can protect your business, visit us at https://infrazen.tech.

