So, what exactly is a vulnerability assessment?
In simple terms, it's a proactive process to find, classify, and prioritise security weaknesses across your systems, websites, and networks. Think of it as a systematic health check-up for your technology, designed to spot issues before an attacker can. The aim isn't just to find flaws- it's to understand their potential impact and create a clear plan to fix them.
What a Vulnerability Assessment Really Means
Imagine hiring a security expert to methodically check every door, window, and hidden access point of your office building. They aren't trying to break in. Their job is to create a detailed report of every potential entry point- an unlocked window on the first floor, a weak door frame, or an old keycard system that’s easy to bypass. You get this report so you can secure everything before a real burglar shows up.
A vulnerability assessment does the exact same thing, but for your technology environment. It’s a non-intrusive review that identifies and catalogues security gaps in your entire technology infrastructure. The end result is a clear, prioritised list of weaknesses, helping you make smart decisions about where to focus your time and money.
The hard truth is that no system is perfect. Software needs updating, configurations get missed during busy projects, and new threats are appearing all the time. A vulnerability assessment gives you the visibility you need to manage these unavoidable risks properly.
The Goal Is Understanding Risk, Not Just Finding Flaws
The real purpose here goes way beyond just generating a long list of technical problems. It’s about translating those technical findings into tangible business risks, a distinction that’s absolutely vital for a creative agency. A single vulnerability can mean very different things depending on where it’s found.
For example, a flaw in your public-facing portfolio website is definitely a problem. But a similar flaw in the server storing confidential client campaign data? That’s a potential catastrophe.
An assessment helps you see the difference by answering three critical questions:
- What are our weaknesses? This is the discovery phase, where all potential security gaps are identified.
- How serious are they? This involves grading each vulnerability based on how easy it is to exploit and what the potential fallout could be.
- What should we fix first? This is all about prioritisation- directing your resources to the most critical risks that pose the greatest threat to your operations, client data, and reputation.
A vulnerability assessment provides the roadmap. It tells you which "doors" are unlocked and which "windows" are broken, allowing you to create a clear plan to secure your most valuable assets.
This proactive approach is more important than ever. Cyber-attacks aren't just a problem for big corporations; they are a direct threat to businesses of all sizes. The UK Government’s recent Cyber Security Breaches Survey revealed that 50% of UK businesses had experienced at least one cyber-attack or security breach in the previous 12 months. That’s a huge jump from 39% in 2022.
You can read more about these rising cyber crime statistics to get a sense of the current threat level. It's why understanding what a vulnerability assessment is has become a fundamental part of modern business resilience.
Why Creatives Must Prioritise Security Assessments

For a creative agency, a security weakness isn't some distant, technical issue- it's a direct threat to the heart of your business. Your most valuable assets aren't kept in a vault; they're the ideas, strategies, and confidential data you manage for your clients every single day.
Imagine the fallout if a client's major campaign launch was compromised by a data breach. Or the reputational damage if your proprietary designs were leaked online before a big reveal. These aren't far-fetched scenarios; they're precisely what a good security assessment is designed to prevent.
That’s why a vulnerability assessment isn't just another IT expense. It's a critical investment in business continuity, client trust, and the reputation you've worked so hard to build. It’s about protecting the very things that make your agency valuable.
Protecting Your Priceless Digital Assets
Your agency is the custodian of priceless information. Client lists, strategic plans, unreleased creative work- these digital assets are the lifeblood of your operation. A simple security oversight could lead to their theft, destruction, or public exposure, causing irreparable harm.
The stakes are especially high for businesses in the information and communication sector. For instance, recent findings from the UK Cyber Security Breaches Survey showed that while 20% of all UK businesses faced cybercrime, this figure skyrocketed to a staggering 43% for our sector- more than double the national average.
This elevated risk means a proactive defence isn't optional, it's essential. The key areas you need to worry about include:
- Intellectual Property (IP): Your concepts, designs, and campaign materials are your core IP. Protecting them is non-negotiable.
- Client Data: You hold sensitive client information, which unfortunately makes you a prime target for attackers looking for a backdoor into larger organisations.
- Reputation and Trust: A single security incident can shatter the trust you’ve spent years, or even decades, building with your clients.
Beyond Technical Fixes: It’s About Business Resilience
Ultimately, good security is a foundational pillar of business resilience. It ensures you can continue to operate, innovate, and serve your clients without disruption. This involves more than just installing some software; it demands a holistic approach to protection.
Adding layers like strong access controls is a crucial first step. Our guide on what is multi-factor authentication offers practical steps you can take right now to better secure user accounts.
A vulnerability assessment moves your security posture from reactive to proactive. It gives you the power to find and fix security weaknesses before they can be exploited, safeguarding your agency’s future.
For a deeper dive into the wider world of digital protection, this comprehensive guide to enterprise software security provides valuable insights. Understanding these principles will help you build a robust defence that’s truly tailored to the unique challenges of the creative industry.
Exploring Different Types of Vulnerability Assessments
Vulnerability assessments are not a one-size-fits-all deal. The right type of assessment really depends on what you’re trying to protect. Think of it like securing a building: you'd use different checks for the perimeter fence than you would for the electrical wiring inside. The same logic applies to your tech.
Getting your head around these differences is key. It helps you have much clearer conversations with security partners and lets you build a protective strategy that covers all your critical assets- from your internal network right down to the custom software you build for clients.
Network-Based Assessments
A network-based assessment is like having a security guard patrol the outside of your office building. They check for unlocked gates, open windows on the ground floor, and any obvious weak spots on the perimeter. They don't go inside; their job is purely to see what an outsider could potentially exploit.
This type of scan does the same for your digital perimeter. It hunts for security issues across your network that an unauthorised person could use to get in from the outside world.
A network scan is on the lookout for things like:
- Open Ports: These are like digital doors left unlocked on your servers or firewalls, just waiting for an attacker to walk through.
- Weak Configurations: Checking if your network devices are set up securely or if they're still using default settings that are notoriously easy to guess.
- Outdated Protocols: Identifying old and insecure communication methods that attackers have known for years how to break.
A well-run network assessment is a great first step to reducing your attack surface. This is also where good internal practices can make a huge difference. For a deeper dive into managing your internal network more securely, our article on what is network segmentation offers some valuable strategies.
Host-Based Assessments
While a network scan checks the perimeter, a host-based assessment is like bringing an expert inside to inspect each room individually. This scan focuses on specific machines- your servers, laptops, and workstations- to find localised problems that aren’t visible from the outside.
This assessment needs access to the device itself, usually with special credentials. It can then perform a deep-dive analysis, checking for things like missing software patches, poor local security configurations, and weak user permissions. It gives you a much more granular and detailed picture of your internal security health.
A network scan asks, "Can someone get in?" A host-based scan asks, "If someone is already inside, what damage can they do?"
Application and Database Assessments
For creative agencies, your websites, client portals, and custom-built software are often your most public-facing- and most valuable- assets. An application assessment zeroes in on these, hunting for flaws in the actual code that could be exploited. This is where common but dangerous vulnerabilities like SQL injection and cross-site scripting (XSS) are usually found.
Working hand-in-hand with this is the database assessment. Your databases are the secure vaults where you store your most precious information: client data, financial records, and proprietary designs. This scan focuses on the security of the database itself, looking for weaknesses like flimsy passwords, excessive user privileges, or unencrypted sensitive data. Given the value of what’s stored inside, locking down your databases should be a top priority.
Comparing Vulnerability Assessment Methods
Choosing the right assessment can feel tricky, but it's really about matching the tool to the task. Each type offers a different lens through which to view your security posture.
This table breaks down the common assessment types, their focus, and where they fit best in your overall strategy.
| Assessment Type | Primary Focus | Best For |
|---|---|---|
| Network-Based | Your digital perimeter and external-facing systems. | Getting a high-level view of your external attack surface and finding obvious entry points. |
| Host-Based | Individual servers, workstations, and laptops. | Assessing internal security health, patch management, and local configurations. |
| Application | Websites, client portals, and custom software. | Finding coding flaws like SQL injection and XSS in your most visible assets. |
| Database | The systems storing your sensitive data. | Securing client information, IP, and financial records by checking for weak access and encryption. |
By combining these methods, you get a much more complete and layered picture of your security. It’s not about picking just one, but about building a programme that covers your risks from every angle.
How a Vulnerability Assessment Works Step by Step
Knowing the theory behind a vulnerability assessment is one thing, but seeing how it actually plays out is where the real clarity comes from. This process isn't some chaotic, random hunt for flaws. It’s a methodical, multi-phase project designed to deliver clear, actionable insights into your security.
From the initial planning to the final checks, each step builds logically on the last. Let's walk through the four essential phases to understand what a vulnerability assessment looks like from start to finish.
Phase 1: Planning and Scoping
This is where you set the rules of engagement. Before a single scan is run, you have to define precisely what’s being tested and what you’re trying to achieve. Think of it as drawing a map before you start the journey. A well-defined scope prevents confusion and makes sure the assessment focuses on your most critical assets.
During this phase, you need to answer a few key questions:
- What assets are in-scope? Are we looking at your public website, the internal network, your cloud servers, or all of the above?
- What are the objectives? Is the goal to meet a specific compliance requirement, like Cyber Essentials, or is it more of a general security health check?
- What are the constraints? Are there specific times when testing can happen to avoid disrupting day-to-day business?
Clear planning ensures the assessment is targeted and efficient. Without it, you risk wasting time on low-priority systems or, worse, completely missing your biggest risks.
Phase 2: Scanning and Discovery
With a clear plan locked in, the technical work can begin. This phase is all about using a combination of automated tools and human expertise to identify potential weaknesses. Security specialists deploy scanners to probe the systems you defined in the scope, hunting for any known vulnerabilities.
This is the discovery process. It generates a raw list of every potential issue, from missing software patches and weak server configurations to outdated security protocols. The goal here is to be comprehensive- casting a wide net to catch anything that looks like a security gap.
Phase 3: Analysis and Reporting
A raw list of potential vulnerabilities isn't very helpful on its own. This is where the real expertise comes in. During the analysis phase, security experts sift through all the findings from the scans to figure out their real-world risk. They weed out any "false positives"- alerts that turn out not to be genuine threats- and prioritise the issues that actually matter.
Prioritisation is arguably the most important part of the analysis. A vulnerability's risk score isn't just a technical detail; it’s based on how easy it is to exploit, the potential damage it could cause, and how critical the affected system is to your business.
The outcome is a detailed report. A good report doesn't just overwhelm you with technical jargon. It translates the findings into clear business risks and provides actionable recommendations for fixing each issue, starting with the most critical ones first.
This image shows the core flow, from identifying your assets and scanning them to, most importantly, prioritising the risks you find.
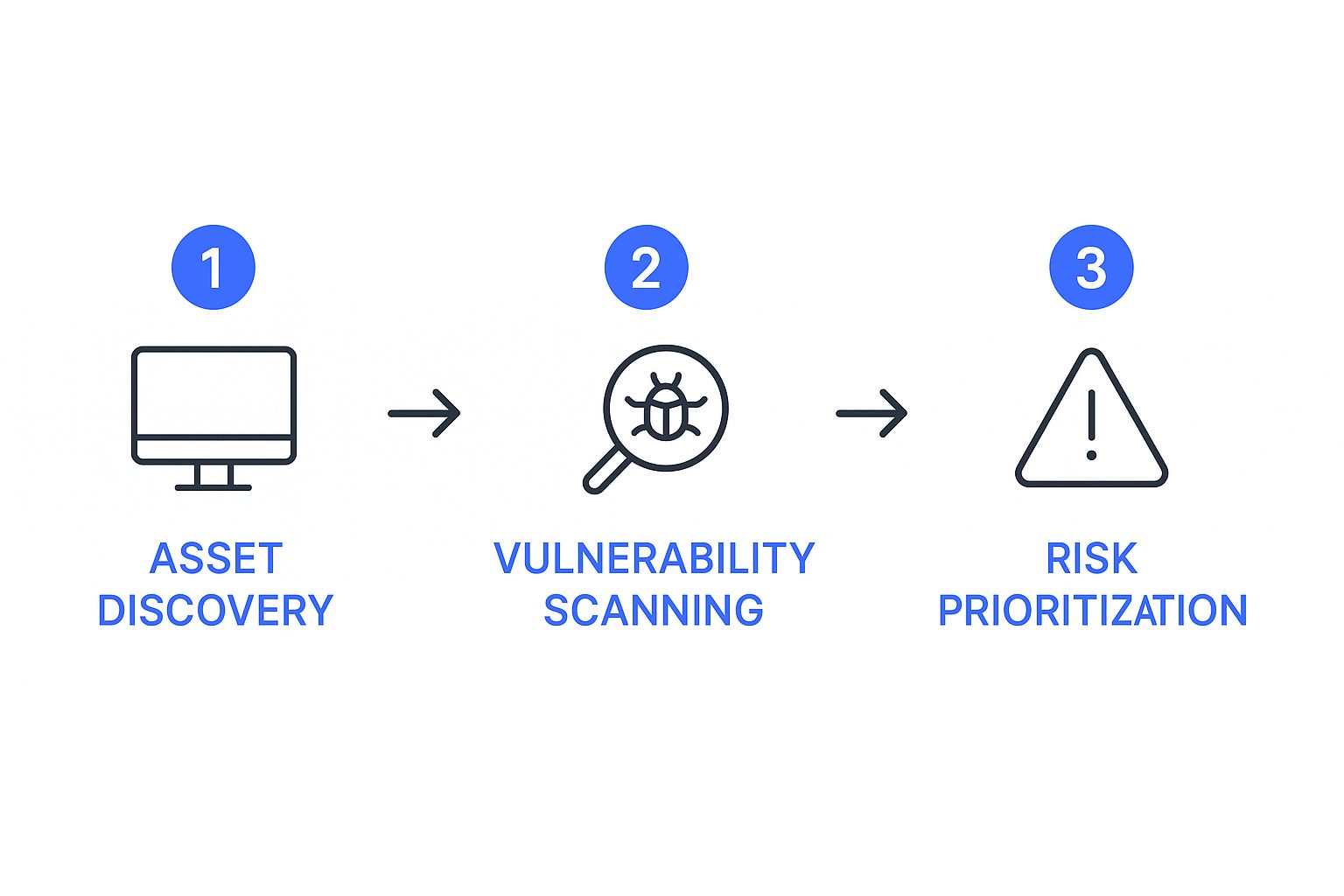
The key takeaway here is that discovery is just the beginning. The true value comes from analysing those discoveries to understand what you need to fix now.
Phase 4: Remediation and Verification
The final phase is all about taking action. Armed with the prioritised report, your team gets to work fixing the identified vulnerabilities. This is the remediation step, where patches are applied, configurations are hardened, and security gaps are properly closed.
But the job isn’t done once the fixes are in place. The final step is verification. The security team re-scans the affected systems to confirm that the vulnerabilities have been successfully patched and that the fixes haven't accidentally introduced any new problems. This verification loop is what confirms your security posture has genuinely improved.
Assessment vs. Penetration Testing: What Is the Difference?

In cybersecurity, you'll often hear "vulnerability assessment" and "penetration test" (or "pen test") used in the same breath. While they sound similar and are definitely related, they are two very different activities. Knowing the difference is key to making smart, effective decisions about how to protect your creative business.
Let’s use an analogy. A vulnerability assessment is like hiring a building inspector to walk through your office. They'll meticulously check every lock, window latch, and potential weak spot, handing you a detailed report of everything that could go wrong. The goal is a complete inventory of potential security issues.
A pen test, on the other hand, is like hiring a security specialist to actually try and break in through those weak spots. Their job isn’t just to list the problems but to see how far they can get and what sensitive information they could access once inside.
Breadth vs. Depth
The core difference really comes down to breadth versus depth.
A vulnerability assessment gives you breadth. It uses a mix of automated tools and manual checks to scan a wide range of systems for potential security flaws. The final report is a broad, prioritised list of "what-ifs."
A pen test delivers depth. It’s a focused, hands-on exercise where an expert actively tries to exploit a few high-risk vulnerabilities to simulate a real-world attack. The result is a practical demonstration of "what could actually happen."
A vulnerability assessment gives you a map of all your potential security problems. A penetration test shows you the actual damage an attacker could cause by following that map.
This distinction is crucial because they answer different questions. An assessment tells you where you might be vulnerable, while a pen test proves how vulnerable you are.
When to Choose Which
So, does your agency need an assessment, a pen test, or both? The right answer depends on your current security maturity and what you’re trying to achieve.
-
Vulnerability Assessment: This is the foundational first step for any security programme. It should be done regularly to maintain good security hygiene and give you a baseline understanding of your risks. Think of it as your regular security check-up.
-
Penetration Test: This is a more intense and targeted test. It’s best used when you want to validate your defences against a specific threat- for instance, before a major product launch or to meet a strict client compliance requirement.
Most creative agencies start with regular assessments to get a handle on their risk profile. And those risks are very real- a UK government survey found that 43% of businesses experienced some form of cyber attack.
Ultimately, these two activities are most powerful when used together. Regular assessments identify the weaknesses, and occasional pen tests validate that your fixes and defences are holding up as intended. This combined, layered approach is a cornerstone of building proactive cybersecurity to maximize your business resilience.
Still Have Questions? Let's Clear Things Up
Even after you've got your head around the basics of vulnerability assessments, some practical questions always pop up. We get it. Here are some straightforward answers to the questions we hear most often from creative agency leaders, designed to help you move from theory to action.
How Often Should We Run an Assessment?
For most creative agencies, a quarterly assessment is a great starting point. This rhythm helps you stay on top of new threats as they emerge and keeps pace with changes in your own tech, like a new plugin for your website or a new app your team starts using.
That said, your schedule should always be guided by your level of risk and how quickly things change. You absolutely must run an assessment after any significant tech event. Think launching a new client website, overhauling your internal network, or bringing a new cloud platform into your workflow.
If your agency handles highly sensitive data- like financial or healthcare information- or you’re bound by strict compliance rules, you'll want to ramp that up to monthly scans.
Can We Do This Ourselves or Should We Hire an Expert?
You can definitely get started with in-house automated scanning tools. It’s a cost-effective way to get a baseline read on your security and catch the obvious, low-hanging fruit. These tools can give you a continuous stream of data on where you stand.
But automated tools have their blind spots. They're notorious for throwing up a huge number of alerts, including "false positives" that aren't actually real threats. Without an expert to sift through the noise and interpret the results, it’s almost impossible to know where to focus your energy.
For your first deep-dive review- and periodically after that- bringing in a third-party cybersecurity firm is the smart move. Their expertise adds the crucial business context that tools alone can never provide, helping you turn a list of technical jargon into a clear, prioritised action plan.
What Is the Main Deliverable From an Assessment?
The key thing you should get back is a detailed report that acts as a roadmap for improving your security. It needs to be much more than just a raw data dump of flaws spat out by a scanner.
A quality report will deliver several key things:
- Prioritised Findings: Vulnerabilities should be sorted by severity- think critical, high, medium, and low– based on how badly they could impact your business if exploited.
- Clear Explanations: Every finding needs to be explained in plain English. What is the risk, and how could it actually affect your agency's work or reputation?
- Actionable Steps: The report must provide clear, step-by-step instructions for your team to fix each problem it identifies.
- Executive Summary: It should always include a high-level summary for leadership that cuts to the chase, outlining your overall risk profile and the most urgent priorities.
This is what transforms a technical exercise into a strategic document that genuinely guides your security efforts.
Is a Vulnerability Assessment All We Need to Be Secure?
No. A vulnerability assessment is a critical diagnostic tool, but it's not a magic cure. Think of it like a medical check-up that identifies health issues. The report tells you where the problems are, but it doesn't fix them for you.
Real security comes from what you do next. It’s built on an ongoing cycle of:
- Assessing: Regularly finding your weak spots.
- Remediating: Actively fixing the flaws you discover.
- Monitoring: Continuously watching for new threats and changes.
An assessment is just one piece of a much larger, continuous security programme. It’s a vital piece, for sure- it gives you the visibility you need to act- but it's the follow-through that truly strengthens your defences and protects your creative business.
At InfraZen Ltd, we help creative agencies build robust security without the complexity. We manage the technical details behind the scenes so you can focus on your clients and your craft. If you're ready for a calmer, more secure approach to IT, visit us at https://infrazen.tech.

